Telling Cyber Security Stories … and Coffee Cups
Telling Cyber Security Stories … and Coffee Cups
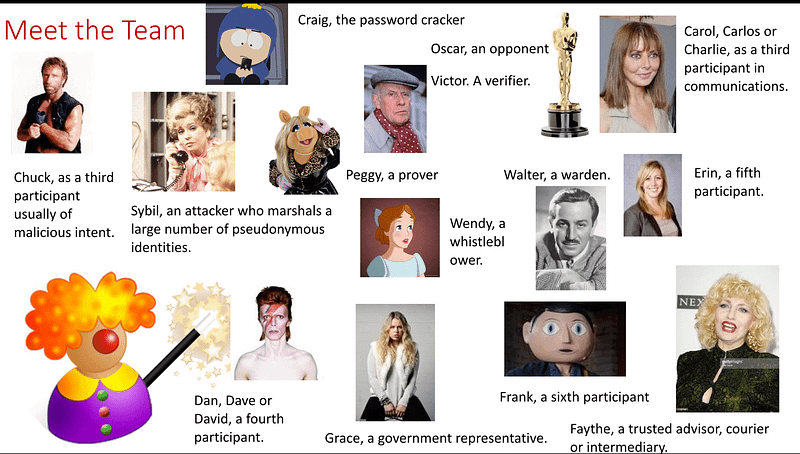
In Cyber Security we like to talk about stories, and to relate them to real-life. So Bruce Schneier — the person who got me hooked on cryptography — came up with a whole lot of roles. The most important were: Bob, Alice and Eve. But there were a whole lot of other characters… can you find them from this picture:

I will put the answers way down the page …
Here are the characters we use for Bob, Eve, Alice and Trent (in a clockwise direction starting from the large graphic):

I even has a T-shirt with Eve on it and some ciphers:

And some props:

And I even have them on the wall of my office:

So when I go into the Starbucks at Bruntsfield (just down the road from our Merchiston Campus):

I like to give my Cyber Security name on the coffee cup, so I give them my Cyber name. So here they are … first I asked for Carol, but they give me “Karol”:

And I really felt like a trusted person the day I used “Trent”:


And then I was the evil one (Mallory), but you can tell they didn’t quite believe my name:

Then “Bobalice” — pronounced “Bob -a-leese” … sounds kinda Italian:

And then “Bob — eve”, which definitely sounds Italian:

And for Walter — the warden — I had to try twice:


And when I finally called myself “Eve”, I got this:

Conclusions
Forget those people who scare you about cyber security. It’s also fun and is helping build a new world!
Answers
How many did you get? Here’s the answers: