Posting The Key To Your Front-Door … To Stop A Robbery
Posting The Key To Your Front-Door … To Stop A Robbery

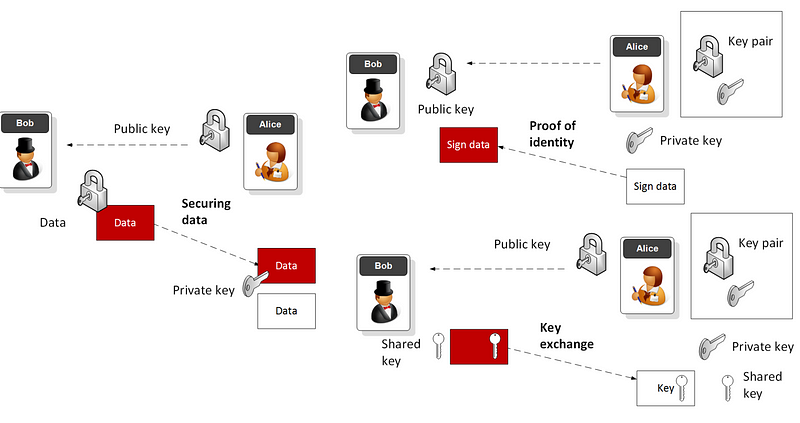
Before I start, here’s a bit of crypto. With public key encryption, we create a key pair — a public key and a private key. The two work together, so that I can encrypt with one and then decrypt with other. The main usages of this is are signing a transaction and in key exchange. In transaction signing, I encrypt something related to a message (such as the hash of the message) with my private key, and then everyone can prove it was me that signed it by decrypting with my public key (and which is known to everyone who wants it). In the following diagram we can see the two main usages of public key encryption are on the right hand side:
Well, the world still awaits Satoshi Nakamoto to reveal his/her private key, but another mystery has been cleared up. It related to an alerting system which was built into bitcoin, and was released by Bryan Bishop and Andrew Chow. The alerting system is now long-gone, but the developers wanted to release the keys so that they would not pose a future risk.
The bitcoin alerting system had long been criticised for its security model and in 2016 it was effectively retired after a public email by Greg Maxwell [here]. This included pin-pointing that the alerting system’s private key had possibly been leaked, as it was seen as being used in the MTGox hack:

The posting signs off with:
At some point after that, I would then plan to disclose this
private key in public, eliminating any further potential of
reputation attacks and diminishing the risk of misunderstanding
the key as some special trusted source of authority.
At the core of the problem is that no-one quite knew who had the key and who could thus broadcast messages. Along with this, as it was a single key, no-one could verify who sent the messages, as they were signed by a single key. The shut-off was not as simple as just migrating the code for bitcoin, as there are many other altcoins on the market which may have still been using the code with the alerting system.
The process to getting rid of alerting system started in 2016, but the private keys were kept secret as it could expose a security weakness for cryptocurrencies which used to an older version of the bitcoin code. Pavol Rusnak, though, ran a script for altcoins on GitHub and found that there was only one which still has the alert key. Bishop and Chow have also outlined that it may be possible for developers to continue to use the bitcoin alerting system method, but highlight an available patch to be run on nodes.
While the Github based patch helps to fix many of the issues of the bitcoin alerting system, the release of the keys affectively kills it off. The distribution of any private key is obviously a worry, and some in the industry also highlighted that a malicious use of it could spread fake messages across the network.

On14 June 2018, Bryan Bishop even challenged Craig Wright to prove that he could sign a message with the bit alerting private key:

Conclusions
The release of the alert key effectively kills-off the alerting system, and where anyone can now sign a message with the private key. It does, though, show a piece of history, and that only those with the original private keys can claim to be past of the history of what could be one of the most disruptive forces ever created. At the current time, this is the closest we have come to revealing Satoshi Nakamoto.
So … what those private keys! A breach of a trust infrastructure is thought to be one of the greatest weaknesses of the Internet, and is likely to be the most costly of an organisation:
https://www.linkedin.com/pulse/great-security-threat-encryption-keys-digital-room-william-buchanan/