Boiling Every Ocean on the Planet … 16,384 times … To Crack A Single Key
Boiling Every Ocean on the Planet … 16,384 times … To Crack A Single Key

I had to smile the other day when a company asked for my advice. They thought that 128-bit keys for AES were too small and that they were thinking of migrating their systems to 256-bit keys. A consultant from a major consultancy company had advised them that 128-bit keys were not safe and that they could be easily cracked.
I smiled because a 128-bit key has 340,282,366,920, 938,463,463,374, 607,431,768,211, 456 different keys (2¹²⁸). If we try 10 billion keys per second, and it will take:
529 million million million years [ link]
to brute force.
So what was the problem that the consultant had identified?
Well, they reported that they were worried about GPU crackers and Cloud-based instances. But GPUs are generally attacking hashes and not AES. There are many weaknesses in password hashing that make it fairly easy for them to be cracked. Anyway, it’s the cost of the work that really matters and how much it will cost an adversary to crack the messages. Also, it’s the way you generate the keys from passphrases that actually matters more than the key size. If the keys are truly random, then there’s virtually no chance that an AES encrypted message will ever be cracked within our lifetime (even with the advent of quantum computers and accounting for Moore’s Law).
If the consultant had identified that the weakness was around the generation of the encryption key through passphrases was the problem, that would be a better argument, but again an improved passphrase generation can still be used with 128-bit encryption. It is really all about key entropy, and if you use the key space of 128 bits you are fine. If you choose keys from well-known words, you massively reduce the key space, and that’s not the problem with selecting a 128-bit key.
If the consultant had identified that the risk was around quantum computers in the future, that again would be a valid argument as quantum computers will require symmetric encryption algorithms to up their game. The show, though, is over for many of the public key methods.
Boiling an ocean
In order to understand the concept of work in cracking cryptography, Lenstra [here] defined the concept of Global Security in order to show the amount of energy required to crack cryptographic algorithms and compare this with the amount of water that energy could boil. This could be seen as the carbon footprint of cracking. For a 35-bit key, you only need to pay for the boiling of a teaspoon of energy, and for a 50-bit key, you just need to have enough money to pay for a shower:
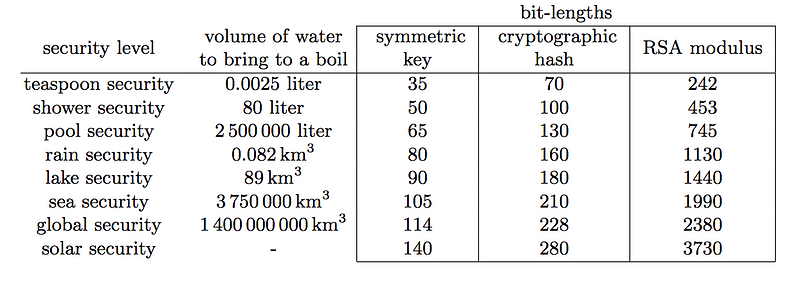
To break a 114-bit key would require the energy to boil every ocean in the world Global security is boiling all water on the planet amounts. That’s a lot of energy!
And remember that 128-bit security, would require double, double, double, double, double, double, double, double, double, double, double, double, double and double the amount of energy. In fact you would have to pay for boiling every ocean, 16,384 times. And it is just a single key cracked, if you wanted to do more, you’d have to pay for the boiling all over again.
And who could afford that? Not even … [%&#] … Ssh! You know who!
Conclusions
When it comes to encryption, we need better education in the industry and for those to not create false arguments for a tick box solution. There generally needs to be an improvement in the way that technical specialists map their knowledge to business problems, otherwise the industry is being sold things on the back of jargon. That’s why I’ll never be a salesman, as I’d probably say,
“Well you could probably do it better if you just did this simple thing and not buy my product”