Generating an Encryption Key Without A Pass Phrase — Meet ECIES
Generating an Encryption Key Without A Pass Phrase — Meet ECIES
Many encryption systems are compromised because they generate their encryption key using a passphrase, and which can considerably reduce the overall security infrastructure. A passphrase which is taken from a standard dictionary, for example, might reduce the key strength from 256 bits to just 20 bits (for a list of around one million words).
So we often use a key exchange method, such as ECDH (Elliptic Curve Diffie-Hellman) to negotiate a shared key, and where we can then use symmetric key encryption (such as AES or 3DES) to encrypt and decrypt. But we might be worried about a man-in-the-middle attack so we can use an Elliptic Curve Integrated Encryption Scheme (ECIES) to generate a shared key without the need for the Diffie-Hellman exchange.
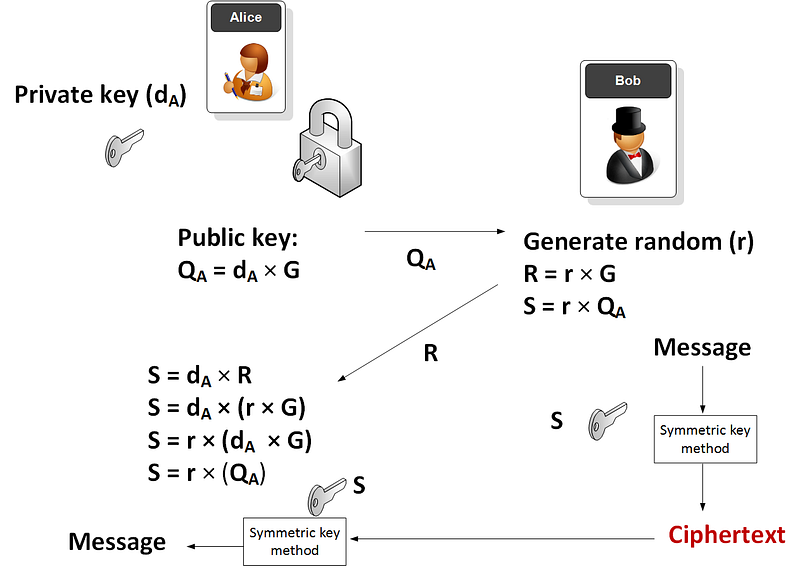
The method basically starts with Alice created a random key (dA) and then selecting a point on an Elliptic Curve (typically, this is secp256k1), and then determining her public key which is:
QA = dA 𝗑 G
The public key (QA) is then passed to Bob who creates a random number (r) and then calculates R and S:
R = r 𝗑G
S = r 𝗑 QA
The S key is now used with a symmetric key algorithm to encrypt a message. Bob then sends the encrypted message along with R. Alice can then calculate the same key (S) with:
S = dA 𝗑 R
The method is illustrated here:

A sample run using the Rabbit light-weight cryptography method is [here]:
Private key: 0xccc793ee9d6fdd1c861ee3d9802b88761197def9ca8095bd7fadc9acbc28ef72L
Public key: (0xee0353193d5d420937feddbb12b140360ada273ca0dbcbc78a251808f6675d8e, 0x6e3bbc0d94bb7563b4d2e0dd6cc8d863bc78bb96e853c0768799b3052deb0b88)
=========================
(107656332029419599769917802512067512277081367313115463981738372970225420688782L, 49859955215437065838080692650774396405197161844861238419024390410367486593928L)
======Symmetric key========
Encryption key: 115265696742704657762445767803179441175485868153958521219784268029749732914900
Encrypted: 78fd20cabc
Decrypted: Hello
If you are interested, the code is here:
private, public = make_keypair()
print "Private key:", hex(private)
print "Public key: (0x{:x}, 0x{:x})".format(*public)
r = 123456
print public
R = scalar_mult(r,curve.g)
S = scalar_mult(r,public)
print "Encryption key:",S[0]
msg=Rabbit(enc_long(S[0])).encrypt(message)
print "Encrypted:\t",binascii.hexlify(msg)
text=Rabbit(enc_long(S[0])).decrypt(msg)
print "Decrypted:\t",text
And if you prefer AES, here’s an example.
Conclusions
Whether it’s Blockchain, Tor, Bitcoin or IoT security, elliptic curve methods seem to be ruling the roost just now. While RSA still wins within digital certificates, it is elliptic curve methods that are winning in most other areas. While elliptic curve is typically used for signing data and for key exchange, we can see it can also be used to create a symmetric key which can then be applied to encrypt/decrypt a file using symmetric key methods. In this case I’ve used the Rabbit and AES encryption methods, but you can apply many other method, if required.