So Who Wanted to Break the Internet … Governments, Law Enforcement … and Banks?

So Who Wanted to Break the Internet … Governments, Law Enforcement … and Banks?
Our digital world has very little trust, and many of the problems that we have relate to the complete lack of trust in anything that we see on-line.
Very few emails that we receive, too, can ever be properly trusted (in fact no emails can really be trusted that someone has faked them, changed the contents, or read the message).
At one time it was fairly easy of intruders to listen to our communications, but, then SSL/TLS came along to fix a problem of the sniffing of network traffic, but it is merely a sticking plaster. Many modern day firewalls, though, break these communications, as they have the required private keys which are able to break the tunnel. But TLS 1.3 will make it a whole lot more difficult, as digital certificates will not be used for the keys.
The new standard is defined as RFC 8446 [here]:

The nightmare for governments and law enforcement is end-to-end encryption, and where data is encrypted at its source. Then it doesn’t matter if you use a tunnel or not, the data will not be cracked and only the hosts on either end will know the key. If the Internet was created now, it would implement end-to-end encryption, and would adopted the Tor network infrastructure. But for governments and law enforcement agencies, a world of end-to-end encryption leads to the nightmare scenarios that it will not be possible to listen to communications. The term “responsible” encryption has been termed, but in practice it is almost impossible to create a system which allows for good, but block bad.
A back door?
So TLS 1.3 has been been published as a standard. As part of the standardisation, several organisations pitched ideas on the options that would be added. A strange one come from BITs [here], and which is an organisation that represents over 100 of the top US financial organizations. In [here] we see a draft of a back-door around the TLS connection:
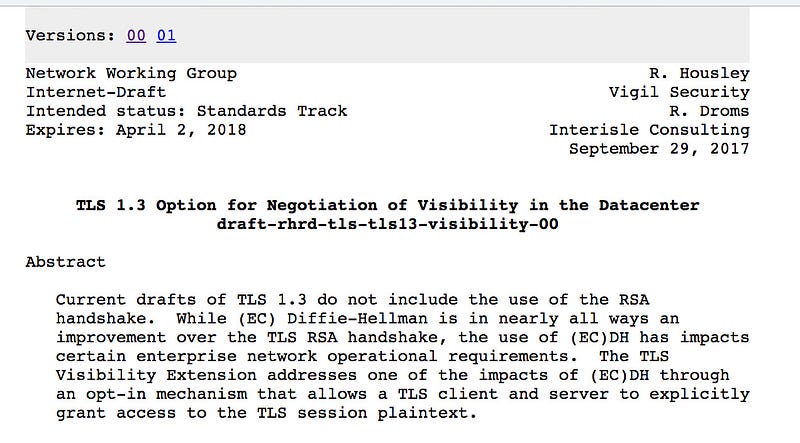
The option allows a server to take control of a connection on behalf of a client, and thus insert a backdoor into the communications. A risk thus exists of malicious man-in-the-middle attacks against connections from within data centres and ISPs. While the banking industry obviously wants this, so that they can scan for malicious leaking of data, the wider ramification is that it could be used by any advisory to spy on communications. The Internet would thus be a much less secure infrastructure.
With TLS we have a static key exchange between the client and the server, and where the client creates the key and then encrypts with the public key of the server. This is defined as “non-forward secrecy”, where the key could only be determined with the private key of the server. Unfortunately it is possible to proxy the operation and decrypt the key, and this is the method that many banks use to break the tunnel. With TSL 1.3 the key exchange would be with a ephemeral Diffie-Hellman handshake, where it will not be possible to use the private key from the server, and only the end devices would have the required keys.
Here is how SSL/TLS works:
Conclusions
For many in the technology industry, this approach would be a complete non-starter as an idea. The line has been crossed, and the freedom of the Internet could be at stake. If you think we have problems with security, just imagine we go back to the time of WEP and non-encrypted traffic, and where anyone could listen to your communications.
Luckily the proposal did not go ahead, and was rejected. If you are interested, here are the things that were successful: