Crypto: The True Defender of Privacy or the Greatest Threat To Society?

Crypto: The True Defender of Privacy or the Greatest Threat To Society?
The rights to silence apply to most things, apart from unlocking a mobile phone. If you do not present your finger or the PIN number for your phone, you are likely to end up in prison.
Assistance and Access Bill consultation
In Australia — as part of its Assistance and Access Bill consultation — the government has now defined that companies must unlock mobile phones, or their owner will face up to a decade in prison. Imagine the headlines:
Apple sends Fred Smith to prison because it refuses to open up his iPhone
Currently, a person in Australia will get two years for withholding data, but the new laws will increase this to a decade. The bill, too, covers telecom operators, devices vendors and application developers, and, in fact, any company with any kind of presence in the country.
To implement this, consultation defines two notices:
- Technical assistance notice. This involves the hand-over of all the encryption keys that companies hold related to a suspect.
- Technical capability notice. This is where it is not possible to gain the encryption keys, and where a company must put in place data taps that would allow government agencies access to the target’s information — a backdoor by any other name.
The consultation defines that companies must hand over detailed specifications for their equipment and product, and allow agents to install their own equipment, in order to gain access to data, and for these operations to be kept secret. A non-compliance to this is likely to bring heavy fines and penalties.
While the consultation stops short in applying backdoors into software for encryption tunnels, it does highlight the capability of intercepting data before and after the encryption process — which thus could perform a man-in-the-middle attack against the end-to-end encryption, and might allow for backdoors to be inserted before and after the encryption process (such as in the client interface).
Overall the consultation mirrors the UK’s Investigatory Powers Act, and leaves in enough slack for governments to implement their investigations in a wide range of scenarios.
Academics, governments and crypto
It is not the first time that there has been tension around cryptography within Australia. With the Defence Trade Controls Act — implemented in April 2016 — there is a restriction on the export of cryptography related material, and many academics worried that they would have to gain licences to teach and even research into material that relates to cryptography [link][act]:
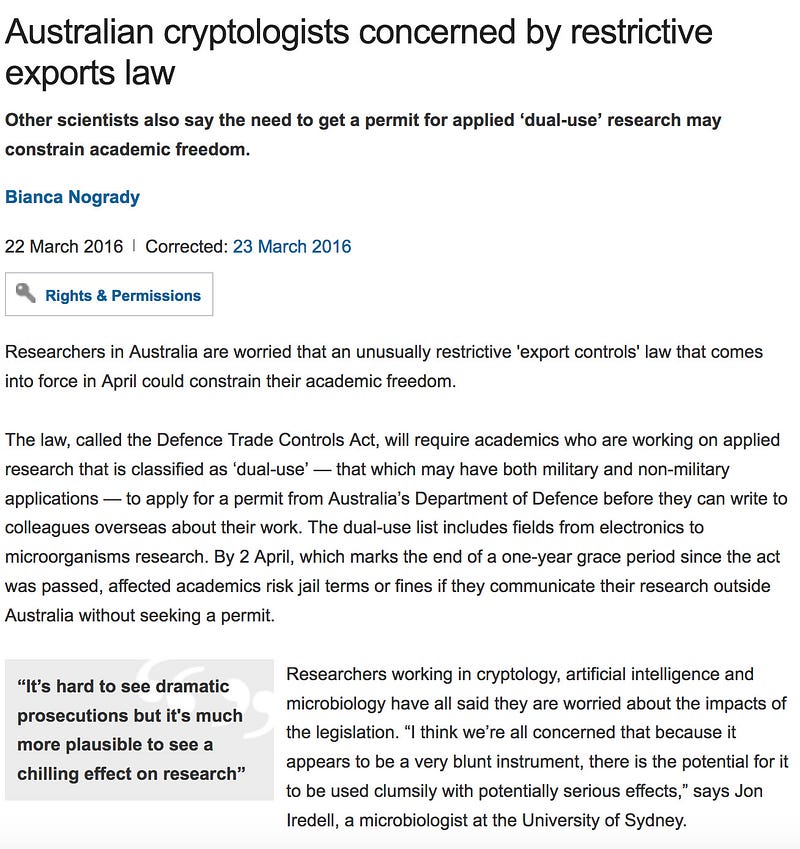
In the article above the author says that academics risk jail if they communicate their research to anyone outside Australia, without having a permit. A number of exemptions were finally added to the act, in order to calm the nerves of those teaching security-related subjects:
Because of these exemptions, most academic activities such as conducting research, teaching students, submitting publications or patent applications, or attending conferences, either inside or outside Australia, are not subject to export control. Additionally, streaming a lecture to overseas students is exempt.
Rights at the fore
The tension thus rises between vendors and governments, with several countries around the world banning end-to-end encryption methods. As industry struggles with the usage of cryptography, you really must wonder if the courts can really make sense of encryption, and where it can only be seen as someone hiding something.
On 4 October 2016, Samata Ullah from Cardiff was charged with terrorism-related offenses. His main charges relate to him being part of ISIS, which is contrary to Section 11 of the Terrorism Act 2000, and in having terrorist-related material. But there are a few other counts which focus purely on the usage of encryption:
- He provided instruction or training in the use of encryption programmes, and at the time he provided the instruction or training, he knew that a person receiving it intended to use the skills in which he is being instructed or trained for or in connection with the commission or preparation of acts of terrorism or for assisting the commission or preparation by others of such acts.
- He engaged in conduct in preparation for giving effect to his intention namely, by researching an encryption program, developing an encrypted version of his blog site and publishing the instructions around the use of program on his blog site. Contrary to section 5 Terrorism Act 2006.
- In his possession an article namely one Universal Serial Bus (USB) cufflink that had an operating system loaded on to it for a purpose connected with the commission, preparation or instigation of terrorism, contrary to section 57 Terrorism Act 2000.
From what I read here: he trained someone in using encryption; he did some research on the usage of encryption for the creation of a blog; and that he had a bootable operating system that allowed him to create a secure operating system. The 1st and 3rd both talk about the intention to pursue terrorist goals, so I would assume there is evidence there to back these up.
It is the 2nd one sticks out as being rather strange as it involves the research around creating an encrypted blog, and then with the intent to just publishing the setup of it. If we look at the highlighted text, you could pin-point anyone who said anything about setting up security on a web site, or in how to use encryption.
Rights to silence and the fifth Amendment
In the UK, citizens have the right to silence (a Fifth Amendment Right in the US — related to the right against self-incrimination) but there is an exception to this related to encryption keys, and the failure to reveal encryption keys can often be seen as a sign that someone has something to hide, and is covered by Section 49 of RIPA. The move by Apple and Google may thus breach law as they must be able to hand-over their encryption key when required. This was highlighted in 2014 when Christopher Wilson, from Tyne and Wear was jailed when he refused to hand encrypted passwords related to investigations related to an attack on the Northumbria Police and the Serious Organised Crime Agency’s websites. He handed over 50 encrypted passwords, but none of these worked, so a judge ordered him to provide the correct one, but after failing to do this, he received a jail sentence of six months.
In 2012, Syed Hussain and three other men were jailed for discussing an attack on a TA headquarters using a home-made bomb mounted on a remotely controlled toy car. Syed, who admitted have terrorist sympathies, was jailed for an additional four months for failing to hand-over a password for a USB stick.
Crypto in court
In 2016, US citizen was sent to prison for failing to provide a password that decrypted two hard disks, and that he will remain there until he complies with the order to provide the password. It relates to a crime that was investigated in March 2015, after monitoring of the network activity within Freenet.
The case of decrypting the drive was dismissed by a district court, but this has since been overruled by a federal court — invoking the All Write Act from 1789, which defines that citizens must co-operate with criminal investigations. This law has been used by the FBI to compel Apple to decrypt the iPhone of Syed Rizwan Farook. The Fifth Amendment privilege, though, defines that individual ha the rights against self-incrimination:
No person shall be… compelled in any criminal case to be a witness against himself.
Your must reveal your finger
For years security professionals have been outlining that usernames and passwords are too insecure on their own, and new methods are needed to properly authenticate users, especially for high-risk access. This leads to multi-factor authentication, where users use two or more methods to authenticate, typically: something you know (your password), something you have (an access card), and something you are (your fingerprint) — and we can also add somewhere you are (such as your GPS-tracked location). Many users now have fingerprint scanners on the mobile device and can even make payments with Paypal using a scan of a fingerprint.
So the tensions between the two camps was highlighted within a Circuit Court judge in Virginia which ruled that fingerprints are not protected by the Fifth Amendment. This means that users who use fingerprints for their mobiles devices may have to reveal their fingerprints when they are being investigated. The judge (Steven C. Fucci) outlined that a user would not have to pass over a passcode, but they would have to give up their fingerprint.
The ruling itself relates to the Fifth Amendment and which protects things that are memorized (passwords and passcodes), but not fingerprints, as these are similar to giving DNA samples or someone’s signature.
A recent case related to a person (David Baust) who was accused of strangling his girlfriend, and where it was suspected that he stored the video of the attack on his phone. With the ruling, the mobile device was protected by a pass code that would not be allowed to be investigated, but a fingerprint protected device will.
Conclusions
As I said in the opening, industry is struggling with the usage of encryption, so one must worry if the courts can make sense of the use of it, apart from thinking that someone has something to hide. Society has never before seen such a barrier to observing the activity of those who may do it harm, but the same barrier also protects our citizens from those who do them harm.