SHA-3: Keccak, Grøstl, Blake, SHAKE and Skein — The Final Versions

SHA-3: Keccak, Grøstl, Blake, SHAKE and Skein — The Final Versions
Where Keccak just wiped out all the competition
Researchers in Canada have defined that the SHA-3 method will take longer to crack that the time that the universe has existed. The total time to crack, with some of the best cracking hardware around, is 1⁰²⁹ years or 1,000,000,000,000,000,000,000,000,000,000 years to crack the hash. But remember, too, Ron Rivest said that RSA was safe for 4 quadrillion years, but the numbers he used could be cracked within days now.
Introduction
Often we have to create a digit fingerprint for data, and a hash signature gives us a value which validates the data. This can be a 128-bit signature (MD5) or a 160-bit signature (SHA-1). Unfortunately both MD5 and SHA-1 have been shown to produce the same hash for different data values. MD5 is the worst at this, and where three photographs are been created which have the same hash signature.
SHA-1 is showing some weaknesses, but it would take a great deal of processing power to actually produce a SHA-1 signatures for an entity. But the weaknesses are there, and the industry worries that with increasing computing power that SHA-1 will be cracked. Thus NIST designed a new hash function for SHA-2, and which has four main hash sizes: 224-bits (SHA-224); 256-bits (SHA-256); 384 bits (SHA-384); and 512 bits (SHA-512). But there is a worry, too, that the method that SHA-2 uses might be cracked, so NIST setup a competition to find the next version of hash signatures, and where we can find a signature which is fit for an IoT world.
The contenders
MD5 and SHA-0 have been shown to be susceptible to attacks, along with theoretical attacks on SHA-1 (and where Google produce the first practical collision on SHA-1 in 2017, but it took two years of computation). NIST thus defined there was a need for a new hashing method which did not use the existing methods for hashing, and a competition for competing algorithms.
In October 2012, Keccak won the NIST hash function competition and is proposed as the SHA-3 standard. It should be noted that it is not replacement SHA-2, which is currently a secure method.
NIST published the new standard, based on Keccak, on 5 August 2015 [here], and which beat off competition from BLAKE (Aumasson et al.), Grøstl (Knudsen et al), JH (Hongjun Wu), and Skein (Schneier et al.). After two rounds the final round an evaluation of security, performance and hardware space.
Gates: Blake and Keccak did well in terms of the number of gates which implement the methods:

Throughput: It was in throughput that Keccak really shone, and beat the others by at least a factor of between three and four:
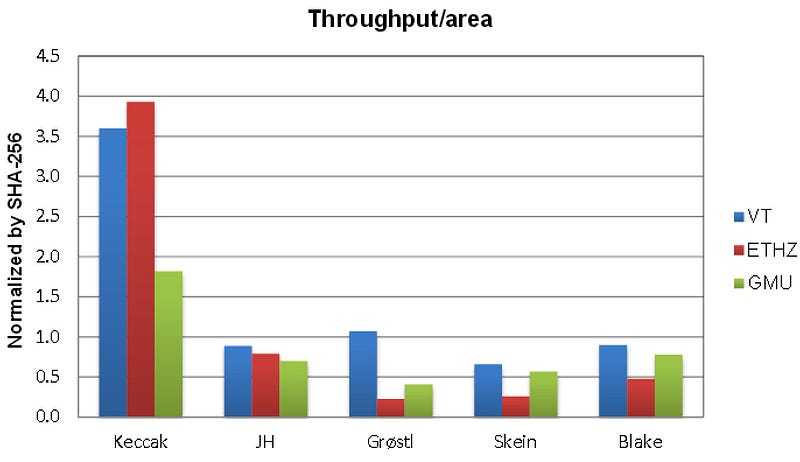
Energy consumption: With energy consumption becoming a major factor within mobile devices and for IoT, the energy consumption for Keccak again trumped the other finalists:
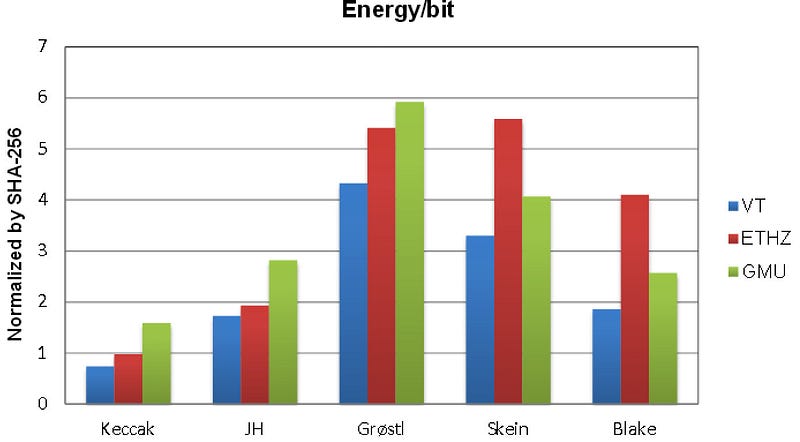
In this Keccak consumed less than half of the power per bit than Blake.
Note: The tests were conducted by ETHZ — Eidgenössische Technische Hochschule Zürich, VT — Virginia Tech and GMU — George Mason University.
Keccak
SHA-3 is known as Keccak and is a hash function designed by Guido Bertoni, Joan Daemen, Michaël Peeters, and Gilles Van Assche. Overall Keccak uses the sponge construction where the message blocks are XORed into the initial bits of the state, and then inevitably permuted.
The sponge function takes a simple function f and involves a number of stages, and where we create a fixed output (dependent on the bit length of the hash function). Simple operations of XOR, AND, and bit shifts are used, and which leads to a fast generation of the hash function:

The f permutation function takes a variable-length input and produces an arbitrary output length. A is the bit rate, and each f function operates on b bits, and where a capacity is defined as c = b — r.
The SHAKE method is useful as it can be used to create a hash method of a variable length. For the 128-bit version will produce a hash value is 32 hex characters.
BLAKE and BLAKE2
BLAKE and BLAKE2 are hash functions based on the ChaCha stream cipher. If you want to try out Blake and Blake 2, they are [here].
Input: The quick brown fox jumps over the lazy dog
— — — BLAKE Version 1 — — — — -
BLAKE 224-bit: c8e92d7088ef87c1530aee2ad44dc720cc10589cc2ec58f95a15e51b
BLAKE 256-bit: 7576698ee9cad30173080678e5965916adbb11cb5245d386bf1ffda1cb26c9d7
BLAKE 384-bit: 67c9e8ef665d11b5b57a1d99c96adffb3034d8768c0827d1c6e60b54871e8673651767a2c6c43d0ba2a9bb2500227406
BLAKE 512-bit: 1f7e26f63b6ad25a0896fd978fd050a1766391d2fd0471a77afb975e5034b7ad2d9ccf8dfb47abbbe656e1b82fbc634ba42ce186e8dc5e1ce09a885d41f43451
— — — BLAKE Version 2 — — — — -
BLAKE 2 224-bit: 477c3985751dd4d1b8c93827ea5310b33bb02a26463a050dffd3e857
BLAKE 2 256-bit: 01718cec35cd3d796dd00020e0bfecb473ad23457d063b75eff29c0ffa2e58a9
BLAKE 2 384-bit: b7c81b228b6bd912930e8f0b5387989691c1cee1e65aade4da3b86a3c9f678fc8018f6ed9e2906720c8d2a3aeda9c03d
BLAKE 2 512-bit: a8add4bdddfd93e4877d2746e62817b116364a1fa7bc148d95090bc7333b3673f82401cf7aa2e4cb1ecd90296e3f14cb5413f8ed77be73045b13914cdcd6a918
The code to implement this is:
from pyblake2 import blake2b
data=""
print 'Input:',data
print '-----Blake Version 1 ---------'
print 'Blake 224-bit:', BLAKE(224).hexdigest(data)
print 'Blake 256-bit:', BLAKE(256).hexdigest(data)
print 'Blake 384-bit:', BLAKE(384).hexdigest(data)
print 'Blake 512-bit:', BLAKE(512).hexdigest(data)
print '\n-----Blake Version 2 ---------'
h = blake2b(digest_size=28)
h.update(data)
print 'Blake 2 224-bit:',h.hexdigest()
h = blake2b(digest_size=32)
h.update(data)
print 'Blake 2 256-bit:',h.hexdigest()
h = blake2b(digest_size=48)
h.update(data)
print 'Blake 2 384-bit:',h.hexdigest()
h = blake2b(digest_size=64)
h.update(data)
print 'Blake 2 512-bit:',h.hexdigest()
Skein
Skein was a contender for SHA-3 and was created by Bruce Schneier, Niels Ferguson, Stefan Lucks, Doug Whiting, Mihir Bellare, Tadayoshi Kohno, Jon Callas and Jesse Walker. It is based on Bruce’s Threefish block and is compressed using Unique Block Iteration (UBI). This supports a chaining mode which allows for variable sizes of hashes. It gets its name the intertwining of the input, which looks like the twining in a skein of yarn:

The following is a calculator for it [here]. A great advantage of Skein is that we can generate hash sizes of varying sizes. While the larger the hash, there will be a lesser change of a collision, but sometimes we might be constrained with processing and storage, so a smaller hash signature may work:
Input word: The quick brown fox jumps over the lazy dog.
— — -Skein — —
Skein-256–8: 9e
Skein-256–16: 6e67
Skein-256–32: b714761b
Skein-256–64: c82c6bcfb18c4ccf
Skein-256–128: e4cbcf28782f052ef43f9be52bc15755
Skein-256–256: 9a6a517c9dff4a1be99439de0c133b205fe151833d5ad7c2c587baef4cd5b436
Skein-512–256: 41e829d7fca71c7d7154ed8fc8a069f274dd664ae0ed29d365d919f4e575eebb
Skein-512–512: 658223cb3d69b5e76e3588ca63feffba0dc2ead38a95d0650564f2a39da8e83fbb42c9d6ad9e03fbfde8a25a880357d457dbd6f74cbcb5e728979577dbce5436
Skein-1024–512: a65cdf3d9a81a04c3674b1e113e48963d49926ff50930f03f58bb10fc748fa288596153d7e8336991dfd9519cf9f6264671153bc536d50c190c89502591b396d
Grøstl
Grøstl was designed cryptographers at the Technical University of Denmark (DTU) and TU and is defined as a new hashing method. Overall it is an iterated hash function, using two fixed and different permutations, along with a compression function. Grøstl comes from an Austrian dish of hash.
The following is a calculator [here] and some sample hashes are:
Input word: The quick brown fox jumps over the lazy dog
Grostl-224: 8ce3ce0f7092cada755be8f614fd6d5e5738ff1f6cd5dabe42404c46
Grostl-256: 8c7ad62eb26a21297bc39c2d7293b4bd4d3399fa8afab29e970471739e28b301
Grostl-384: 9330aeb62a1fc0a464dd70ac27b57075e00ae5d627f9bd6ff72952b3857aba2cfbcc4345af9a04fcc13eb346829e4088
Grostl-512: badc1f70ccd69e0cf3760c3f93884289da84ec13c70b3d12a53a7a8a4a513f99715d46288f55e1dbf926e6d084a0538e4eebfc91cf2b21452921ccde9131718d
Conclusions
National Institute of Standards and Technology (NIST) released the final version of the method as a new standard: Federal Information Processing Standard (FIPS) 202, SHA-3 Standard: Permutation-Based Hash and Extendable-Output Functions. A key factor in the definition of the new standard was that each of the methods submitted required signed statements that the method would be available on a royalty-free basis.
So here is the code [Keccak].
I’ve tested all the vectors against the NIST spec, so they should be correct.