The Complexity of the “Cyber Security” Role — When 52 Becomes One

The Complexity of the “Cyber Security” Role — When 52 Becomes One
We have a problem when it comes to Cyber Security. The main problem is that many will define a “Cyber Security” Professional and think that it is one job function and where we can ask the person about a wide range of things from risk to IoT security. But it’s not true. It is just a name that we have attached to a growing area, and it gives very little hint as to where the expertise of a person might lie. And it doesn’t really define their level of expertise in the area.
One of the problems is that there are so many subject areas involved, and they can range from highly technical subjects such as Penetration Testing, Cryptography and Malware Analysis (the red circles in the diagram) to Human Factors, Risk and Organisation Factors (the blue circles):
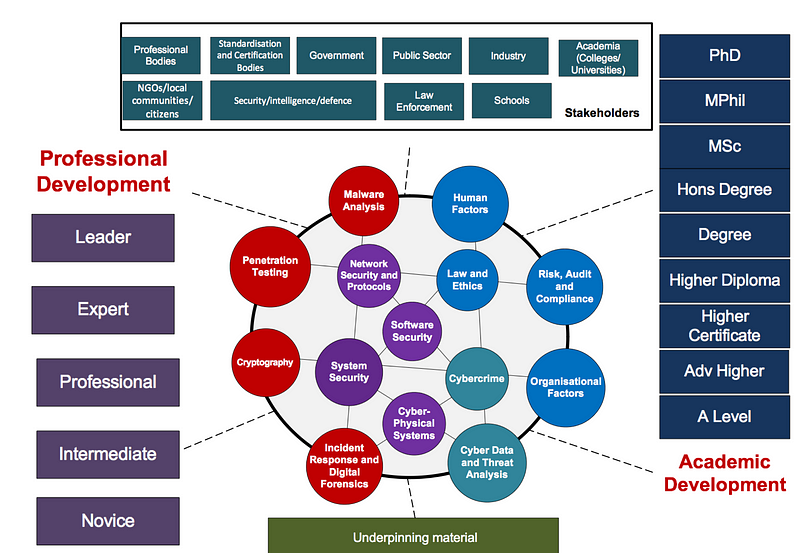
NICE has tried to simplify this complexity, and all the various stakeholders involved, and create this abstraction of the problem:
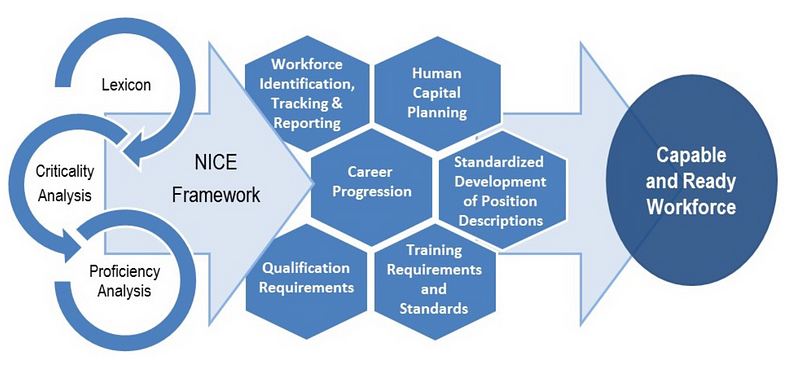
But our current mappings between industry and academia do not quite match up the things that industry would define within jobs roles, where academia often fails to link with professional development. At one time an academic qualification might be the thing that gets you your promotion, but increasingly its more about the knowledge and skills that you have, and your career progression. NIST thus want us all to use the same names for roles, knowledge, skills and abilities, and this will help recruiters to identify the best candidates and for companies to plan their skills development activities.

In order to address this NIST has broken the field into categories and then split these into speciality areas, work roles, skills, knowledge areas and abilities.
For Cyber Security they define seven categories; 33 speciality areas; and 52 work roles [here], and then map these to 1,007 tasks, 374 skills, 630 knowledge areas and 176 abilities:
- Securely Provision (SP). Risk Management (RSK); Software Development (DEV); Systems Architecture (ARC); Technology R&D (TRD); Systems Requirements Planning (SRP); Test and Evaluation (TST)
- Operate and Maintain (OM). Data Administration (DTA). Knowledge Management (KMG). Customer Service and Technical Support (STS); Network Services (NET); Systems Administration (ADM); Systems Analysis (ANA)
- Oversee and Govern (OV). Legal Advice and Advocacy (LGA); Training, Education, and Awareness (TEA); Cybersecurity Management (MGT); Strategic Planning and Policy (SPP); Executive Cyber Leadership (EXL); Program/Project Management (PMA) and Acquisition;
- Protect and Defend (PR). Cybersecurity Defense Analysis (CDA); Cybersecurity Defense Infrastructure Support (INF); Incident Response (CIR); Vulnerability Assessment and Management (VAM)
- Analyze (AN). Threat Analysis (TWA); Exploitation Analysis (EXP); All-Source Analysis (ASA); Targets (TGT); Language Analysis (LNG).
- Collect and Operate (CO). Collection Operations (CLO); Cyber Operational Planning (OPL); Cyber Operations (OPS).
- Investigate (IN). Cyber Investigation (INV); Digital Forensics (FOR).
Cognitive v Psychomotor?
A major problem within the area is that academia perhaps doesn’t match their courses to the required skills and attributes that are required in the industry. Often academic uses a cognitive model of educational advancement (typically the Bloom’s model), and where we move from knowledge, though to comprehension and up to synthesis and evaluation. It is the way that we have designed our curriculum for years.

At the first year of an undergraduate course we might ask
“What type of classification of address is 10.10.10.1?”,
and where we probe for knowledge (that the student knows about the five types of IP addresses) and comprehension (that the student can then link the values in the address to the IP address classification). As we progress onto BEng (Hons) and MSc levels, we might then ask,
“A company has four main hubs, and there are 20 networks which connect to each of these addresses. They have invested in a back-up route for each of the connections. The company have asked you do evaluate a range of solutions for their infrastructure. Outline and evaluate these solutions -taking into account key metrics such as latency — and present results on your finds”.
In this case, we ask the student to understand the range of solutions that are possible (analysis) and then design a range of solutions (synthesis) and then to evaluate the designs (evaluation).
But does this really match to the type of work would be required to define a profession in industry? For the industry certifications, such as with Microsoft and Cisco System, we see the advancement of “doing” skills, and the higher the complexity of the “doing” skills the more expert the person becomes. It is all about creating things that are real, and much less about abstract concepts. And so the psychomotor pedagogy may be at the heart of a future academic model, where students are assessed from being set tasks which they follow (set) and up to the highest level of being able to adapt and originate:
Configure the router with its hostname by entering the command of “hostname myrouter” [set]
We can pick out IP addresses with a regular expression of “[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}.[0-9]{1,3}”. Scan your log file using this expression and view the results. What problems can you identity with it? Now modify so that it only picks up IP addresses. [adaption]
We can scan a log for IP addresses using a regular expression, but this will often provide false positives. Using machine learning and probability theory, train your system to identity an IP address, and then evaluate its success. [origination]
Supporting the brightest students?
The other major problem that we have in Cyber Security, is that academia will teach to the average level of a class. So how can we best support the development of the brightest students?
Well, one way is for them to self organise themselves, and let them learn from each other. Also let them work together while competing, and have fun along the way. This focuses more on the psychomotor academic model. So, over the past year or so we’ve helped support a range of Capture The Flag (CTF) activities.

In my own university, we have the Edinburgh Napier Security Society (ENUSEC>) who have found ways of organising themselves and building a community of support and learning. They are a supportive group, and who also integrate with recent graduates, and who feedback their experience and help.
And they are there at conference events talking to industry leads and building bonds between academia and industry:

And in creating their own CTF events:










Conclusions
We have many problems in academia related to cybersecurity. The first is whether industry should just pick off the best from school and get them into a job (and perhaps just study in a day release mode). In this way, we produce graduates who have the required skills when they graduate, rather than teaching them things that are not currently relevant.
The second is that increasing Bloom’s model of learning is not quite matching industries requirement of people who just do things.
And lastly, we are a “profession” of 52 jobs, and but the industry still sees it as one job. In the days of the “Information Security” professional it was easier, but the buzz word of “Cyber Security” came along, and the bandwagon was created. And so what is the common knowledge that all Cyber Security professionals have? I have no idea, but perhaps a professional body focused on Cyber Security will sort it out, but which way will it lean? Towards the requires of Governments, or towards industry, or towards academia?
It’s going to take a bit of settling down.