Watch Those Chargers AT Public Spaces … A Major Android Flaw

Watch Those Chargers AT Public Spaces … A Major Android Flaw
A decade ago I wrote books on AT commands and I used to work with them extensively when I integrated with RS-232 connections and modems, but their day seemed to be past. Unfortunately, they are still around and are typically still used by venders to test their equipment.

The days of the modem have since past, but vendors have continued to use the commands, and have even expanded the number of AT commands used, in order to build in their own functionality.
So when your smart phone leaves the factory, it is given a test with scripts which call up these AT commands, and then test the phone. It is thus a lot easier to do this with these scripts than to actually get humans to do the actual testing. If something isn’t working, a tester will also use AT commands to probe the inner workings of the device.
But now researchers from the University of Florida, Stony Brook University, and Samsung Research America have discovered a number of AT (Attention)-based attacks on Android devices from 11 mobile phone venders (presented at Usenix Security Symposium):

AT commands has been used for many years, and their history dates back to modem integration. For this, I wrote a book on RS-232 communications a few years ago, and here’s my quick review of some of the commands:


In the days of the modem, we used to send three ‘+’ symbols along the line (‘+++’) and it would send the modem into a command mode, after which the commands can be entered. And so an ATPT command does a pulse dial for a given number, and the ATH command hangs up on the call. These commands used to passed through a serial connection (RS-232) to the modem, and which could then configures the modem’s settings, and makes calls.
These days, though, even though we typically connect with USB or Ethernet, we mimic the RS-232 connection, and still use the commands. The great security worry is that many venders have since built on these commands and adding ones for advanced features, such as to control the camera on the phone.

The researchers generated a range of AT-related commands and watched to see if the devices responded to the commands that they probed with. Overall they analysed a number of Android firmware systems including ASUS, Google, HTC, Huawei, Lenovo, LG, LineageOS, Motorola, Samsung, Sony, and ZTE. They found that there were around 3,500 different types of AT commands. Quite a few of these AT commands had serious security issues, such as where someone could dock their phone with a USB charging socket, and a malicious agent could send an AT command to control the camera on the phone:
“we systematically retrieve and extract 3,500 AT commands from over 2,000 Android smartphone firmware images across 11 vendors. We methodically test our corpus of AT commands against eight Android devices from four different vendors through their USB interface and characterize the powerful functionality exposed, including the ability to rewrite device firmware, bypass Android security mechanisms, exfiltrate sensitive device information, perform screen unlocks, and inject touch events solely through the use of AT commands.”
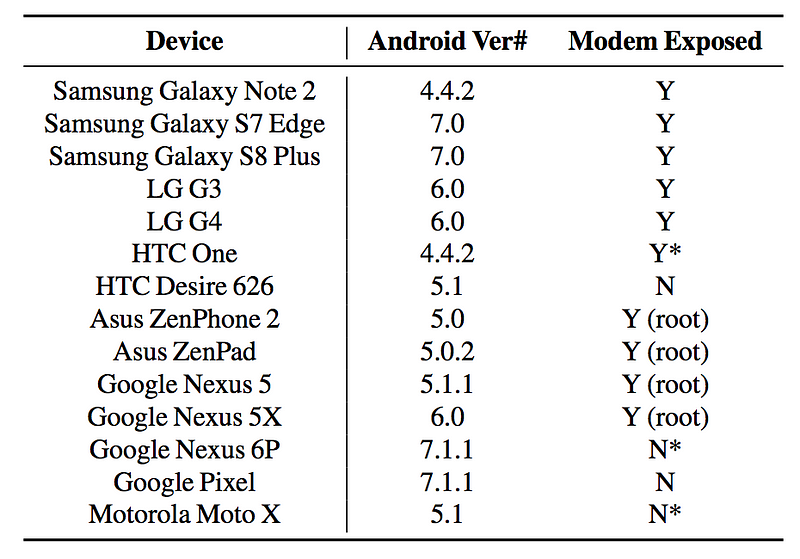
They found that the could unlock a phone with an AT command, too, and bypass the security settings on the device. On LG and Samsung phones they found the could mimic human actions in keyboard interactions, and the researchers think that these features are purely for testing, and not meant to be used in live systems. Of the phones that exposed the modem connection by default, they found that Samsung and LG devices exposed it as default, but Asus and Google ones required rooted devices, where the Google Pixel and Motorola Moto X did not expose at all:
Some of the advanced commands included a full factory reset (AT FRST or AT FACTORST=0,0), a firmware download (AT DLOAD) and a power off (AT^RESET):

Other features commands discovered included “AT KEYLOCK=0” to unlock the keypad, “AT CGDATA” to connect to the Internet, “AT$QCMGD” to delete messages, and “AT CMGS” to send an SMS message:

And as if this wasn’t enough, the researchers dived into the low-level security settings of the devices, with “AT IMEINUM” returning the series number and “AT SYSCAT” doing a listing from the /sys folder:

Conclusions
We think our devices are security, but we find that vendors don’t turn off their testing infrastructure … sloppy work!
Postscript
If you are interested, here is me using AT commands to hack a kettle.
In the following example the wi-fi kettle has an IP address of 192.168.0.22. If we use nmap we see:
$ nmap 192.168.0.22
PORT STATE SERVICE
23/tcp open telnet
2000/tcp open cisco-sccp
We can then connect to port 2000:
$ telnet 192.168.0.22 2000
HELLOKETTLE
HELLOAPP
To switch the kettle on or off:
set sys output 0x4
set sys output 0x0
We can then connect to port 23 and enable the Web server. Notice that the password to get me into the AT command shell is “000000”:
$ telnet 192.168.0.22
AT+ Command Shell
Password: 000000
Login Successfully
AT+WEBS=1
AT+PMTF
AT+Z