The 3T challenge for digital forensics: Tails, Telegram and Tor

The 3T challenge for digital forensics: Tails, Telegram and Tor
In a world on Microsoft Windows, the job of the digital forensics investigator has been relatively easy. The operating system and applications leave lots of fragments of evidence, and these are relatively easy to piece together. In a world of encryption-by-default and the increasing use of Web-based systems, the role is going to get a whole lot more difficult, as secure messaging, secure operating systems and secure network connections can be used to hide all traces of applications, connections and data.

Recently the Afaaq Electronic Foundation (AEF), an arm of the Islamic State who are dedicated to “raising security and technical awareness” among jihadists, published their advice on how to avoid law enforcement surveillance. Their message was broadcast on Telegram, with a message of “Stay calm and use strong encryption”:
It provides a focus on the three T’s which are cause law enforcement to lose sleep: Tor, Telegram and Tails OS.
Tails (The Amnesiac Incognito Live System) OS
With the Tails OS, we see an operating system which focuses on leaving no trace on the computer and which aims to encrypt all the files, emails and instant messages:

As it’s a live operating system, it boots from a USB stick, and this leaves no trace that it has been run (apart from in the running memory, and which will decade quickly). In the promotion of the operating system they define the terms of:
amnesia, noun:
forgetfulness; loss of long-term memory.
incognito, adjective & adverb:
(of a person) having one’s true identity concealed.
and have built their operating system to hide all traces of user activity. Like many of the other open source Linux distributions, it is a collection of tools required for privacy, such as using the Tor Browser:

The Debian-based operating system even detects when it is running in a virtual environment, and not booted live from a USB stick/DVD.
Telegram
A recent example, too, revolves around the usage of encrypted messaging applications. While WhatsApp has been getting much of the press in the UK, it is Telegram which is currently the focus of attention in areas such as East Asia. The promotion of Telegram provides a mine of attributes that malicious agents could use … such as the usage of heavy encryption, the broadcasting of messages, and in the self-destruction of messages:

From their promotion, from a standing start two years ago, they now have over 100 million active users per month (and over 350,000 new users each day), with over 15 billion messages sent on a daily basis:

Overall Telegram integrates into mobile phone applications using API calls, and converts messages in a binary stream. It then uses cryptography to encrypt the communications before sending it over the network using a range of methods (Figure 1), including for Web communications (HTTP or HTTPS) or network communications (TCP and UDP).

Figure 1: Telegram attack
In East Asia, Telegram has seen a large number of adoptions for its service since Park Geun-Hye (the South Korean President) announced that users could be prosecuted for insulting or generally rumor-mongering messages, including through private message systems. In the past two weeks alone, Telegram’s service has seen a three-fold increase in sign-ups.
Tor
The Web traces a wide range of information, including user details from cookies, IP addresses, and even user behaviour (with user fingerprints). This information be used to target marketing to users, and also is a rich seem of information for the detection and investigation of crime. The Tor network has long been a target of defence and law enforcement agencies, as it protects user identity and their source location, and is typically known as the dark web, as it is not accessible to key search engines such as Google.
Obviously Tor could be used to bind to a server, so that the server will only talk to a client which has been routed through the Tor network, which would mean than search engines will not be able to find the content on them. This is the closed model in creating a Web which cannot be accessed by users on the Internet, and only by those using Tor. If then users trade within the dark web servers with Bitcoins, there will be little traces of their transactions.
With the Tor network, the routing is done using computers of volunteers around the world to route the traffic around the Internet, and with ever hop the chances to tracing the original source becomes reduces. In fact, it is rather like a pass-the-parcel game, where game players randomly pass to others, but where eventually the destination receiver will eventually receive the parcel. As no-one has marked the parcel on its route, it’s almost impossible to find out the route that the parcel took.
The trace of users access Web servers is thus confused with non-traceable accesses. This has caused a range of defence agencies, including the NCA and GCHQ, to invest methods of compromising the infrastructure, especially to uncover the dark web. A strange feature in the history of Tor is that it was originally sponsored by the U.S. Naval Research Laboratory (which had been involved in onion routing), and its first version appeared in 2002, and was presented to the work by Roger Dingledine, Nick Mathewson, and Paul Syverson, who have since been named, in 2012, as one of Top 100 Global Thinkers. It since received funding from Electronic Frontier Foundation, and is now developed by The Tor Project, which is a non-profit making organisation.
Thus, as with the Rights to remain private, there are some fundamental questions that remain, and it a target for many government around the World. In 2011, it was awarded the Free Software Foundation’s 2010 Award for Projects of Social Benefit for:

Figure 2 shows a Web browser application setup for Tor. It uses onion routing and also the HTTPS protocol to secure the accesses. With Tor, too, the path between the two communicating hosts is also encrypted, which creates a tunnel between them. To focuses more on the security of the communication over the Internet, and less on the preserving the anonymity of the user. It is, though, often used for proxy accesses to systems, where a user wants to hide their access.
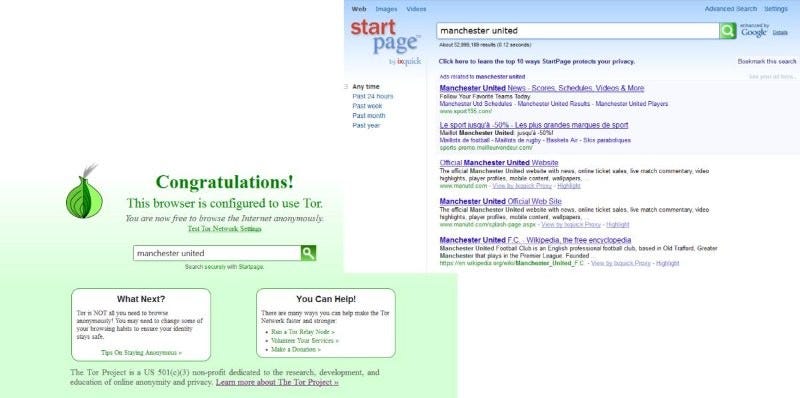
Figure 2: Tor Web browser
Conclusion
The days of the forensics investigator just running EnCase are over. One of their major challenges is now going to be investigating data in each of the three states: on-the-air; in-process; and at-rest. It’s not going to be easy for them, though, as the world moves towards encryption-by-default.