Detecting Malware In Android Stores

Detecting Malware In Android Stores
We recently publishing a paper in Digital Investigation on the detection of malware within Android marketplaces [here]. For this we analysed marketplaces in China, Russia and Europe, and found a significant number of malware infections on Android apps.
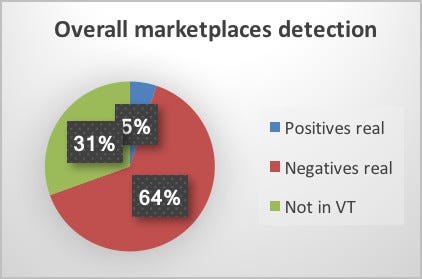
Using the tool designed and implemented in previous sections it was possible to obtain detection data from 9,000 APKs. To begin to analyse the paper’s results, an overall view of the downloaded and scanned APKs is plotted to a pie chart, so to show a realistic proportion of detected applications. As can be deduced from the figure below, analysing a total of nine marketplaces spread through Europe, China and Russia, 64% of the downloaded APKs scanned via VirusTotal result as Negative (or genuine). Only 5% of the total APKs have been detected from more than 5 AVs but it is still circa 450 malicious APKs.
Furthermore, 31% of the total downloaded APKs are still unknown because they have never been uploaded to VirusTotal.At this point, it is important to remember that these statistics are based on AV detections and for this reason, it means that it is not guaranteed that the 64% of the applications are completely safe, although it is more likely that they do not contain malicious code (or at least currently known malicious code). At the same time, the 31% of new applications to be stored, reflects an Android world in continuous growth, with many new or repackaged applications built every day, and for this reason, difficult to manage in terms of security.

The diagram gives a more in-depth the division of detected malicious activities throughout the three main regions adopted for this project (Russia in green, China in blue, Europe in red). As it would be expected from the literature review, because Chinese does not have a legal Google Play Store active at the moment, the number of positive detected APKs is considerably higher than the other two regions (248 vs 81 and 90). It is also interesting to note how China has a remarkable difference in terms of “never scanned” APKs.

The diagram defines the Top 15 detected malware samples given by the sum of three analysed Russian marketplaces (Softportal, Tegramarket, and Uptodown). As it can be seen, at least 5 of the most detected threats are AirPush adware. AirPush is a mobile ad network based on push notifications and instead of using in app advertisements, they add notifications inside the Android tray bar.

The first and second detected malware threats, with a number of 51 and 48 respectively, are instead generic detection for Trojan, which usually could refer to adware and spyware. The second histogram, reveals more or less the same scenario found for the Russian marketplaces, with just an increased number of Artemis threats. Artemis was detected for the first time by McAfee and is considered a potentially unwanted program. It usually works as an adware and it can also hijack the main browser.

The diagram reflects the Chinese average marketplace scenario and it is undoubtedly more dangerous than the previous two. Even though the highest number of detections are still generic malware it shows how riskware such as SMSPay or the similar SMSReg are spread throughout the Chinese web. SMSPay is a malware used to add an SMS activation fee to fake legitimate applications.
Conclusions
As it was analysed in the result section a first overall view of the current situation on the average third-party marketplace reveals that 5% of the total APKs have a high likelihood of containing malicious code, 64% are likely to be clean and 31% of them have never been scanned by VirusTotal. These percentages can be considered only as a guideline, because VirusTotal’s AVs cannot guarantee to uncover malicious code inside a specific APK. Furthermore, every one of the AVs used by Virus Total uses its own database and method, which brings to a plethora of different malware types detected. For these reasons, a lower cap of 6 positive detections was set during this paper to define an APK as malicious. On account of that, two previously analysed studies, DroidMOSS and DroidRanger, have been compared revealing a similar malware and repackaging percentage in similar Android marketplace scenarios.
Geo-localized over three main regions (China, Europe, and Russia) has been plotted showing a majority of malware detections focused on China, with 248 probable malicious APKs found. Furthermore, in China a vast number of applications was found as never detected by VirusTotal, if compared with the other two regions, confirming that China is a continuously changing scenario with always either new or repackaged applications growing wildly because of the absence of an official Play Store.
Subsequently a proper malware detection comparison has been analysed throughout the three main regions. While Russia and Europe had similar results, with a preponderance of generic malware detection, adware, and Airpush (advertisement mobile network for push notifications) and only a few cases of the most dangerous applications, China had again a completely different scenario, revealing a highly detected number of riskware like SMSPay, which are used to trick money from users.
Finally, searching through all the detected malware types, a couple of noteworthy Trojans have been found like GoldenEagle and Plankton. Also GinMaster, a trojanized application strictly geo-localized in Chinese marketplaces was detected numerous times. Furthermore, Fusob, a mobile ransomware discovered recently, was also detected throughout the dataset.
As it would be expected, this research has shown how a high percentage of dangerous APK can still be found over the web through untrusted marketplaces, especially Chinese ones. However, most interesting, it has to be noted how many applications are distributed along the internet without any security check as VirusTotal database revealed.