Crashing Systems With a Font: The Homograph Attack

Crashing Systems With a Font: The Homograph Attack
A recently vulnerability was been found to crash many Apple iOS devices (such as WhatsApp, Facebook Messenger and Gmail). It derives from a single character from the alphabet of the Telugu language (and which is a Dravidian language and spoken by over 70 million people). The bug was spotted by the Italian blog, Mobile World.
The vulnerability — known as homograph attack (known since 2001) — was found by a Chinese researcher (Xudong Zheng) and now often used by scammers to trick users in regions of the world. A recent scam used the apple.com domain and was even signed by a valid digital certificate:
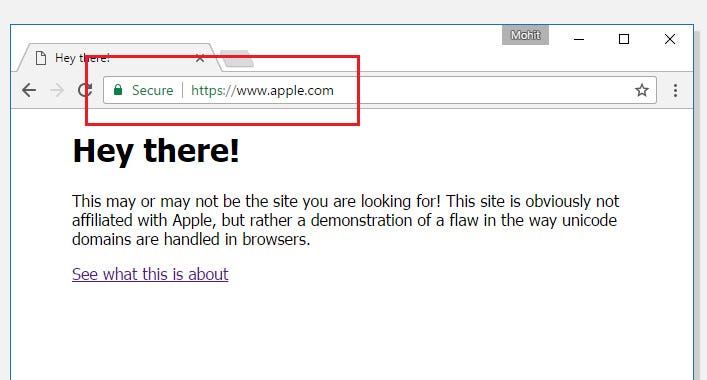
This shows that the certificate is valid (as it goes green), but it is not the Apple site. The epic.com site was used as a demonstrator of the vulnerability:

The site looks to be signed by epic.com, but where we see the Common Name (CN) is xn — e1awd7f.com:

It works by replacing the characters with Unicode characters, where quite a few characters act differently when they are processed as a Web address. With Punycode, the “ — “ part defines a prefix which defines that the domain is formatted in ‘ ‘ to represent the Unicode characters:

can crash your device and block access to the Messaging app in iOS, including WhatsApp, Facebook Messenger, Outlook for iOS, Gmail, Safari and Messages for the macOS versions.
Crashing Twitter with a single character
On 11 July 2014, Twitter announced:
We've temporarily taken TweetDeck services down to assess today's
earlier security issue.
We'll update when services are back up.
This message reported on the spamming of tweets from TweetDeck which had started several hours earlier. The hack was caused by a simple injection of some JavaScript with an automated click on the link. So the script basically went into the TweetDeck interface, which many users leave running in order to watch tweets arrive in real-time, and then cause the link to be clicked on, on a continual basis. It affected the @derGeruhn account with over 84,390 retweets in a short period of time (including on the BBC site):

The following shows one of the retweets:

The script itself was run within TweetDeck, where the (heart) at the end allowed JavaScript to be injected into Tweetdeck to cause a worm which retweet links. The script itself has three main actions. It first finds the top link, and then clicks on it, after this, it marks it for a retweet, and then shows a message to the screen (XSS in Tweetdeck):

The following outlines how the hack works, and some of the issues related to it. To call it a “hack” is perhaps an overstatement, and it seems that the threat has been caused, like many of the original viruses and worms, but a mistake, where a script kiddie ran a bit of code within Tweetdeck, that eventually ended up doing more than just show a simple message to the screen.
It by a 19-year-old computer programmer named in Austria who wanted to show a cute little heart. A worm then spread which came from a tweet of a “♥” symbol (&hearts) and associated code, which retweeted a link in Tweetdeck. The heart symbol caused the Tweetdeck’s software to JavaScript into was discovered by mistake. He then tried it a few times, and then tweet his triumph:
"Vulnerability discovered in TweetDeck. \ o /"
and informed Twitter, but it was too late, as others, including within Hacker Forums, had found it and started creating a mass TweetDeck hijacking ensued. We can see here that was experimenting with hearts, and announced to the world what he had found:
Once the vulnerability had been found, others moved forward and created the worm, but sending the code and automatically clicking on links to be retweeted (including the BBC who retweet to 10.1 million users):
<script class="xss">$('.xss').parents().eq(1).find('a').eq(1).click();
$('[data-action=retweet]').click();alert('XSS in Tweetdeck')</script>♥Basically, TweetDeck picked up the tweet, such as from the BBC, which sent it on to others, which then ran the script if they had TweetDeck open, and then retweet, and so it went on. In it was just like the old days with worms infecting systems, and hog them to the point that they became unusable. In this case, Twitter stepped and switched off the retweeting of the messages.
Conclusions
For system designers, you just can’t test your code enough, and should catch exceptions in a good way.