SOCLAB — Building The Future of Cyber Security Training and Awareness

SOCLAB — Building The Future of Cyber Security Training and Awareness
Towards an investment in people, awareness and training in Cyber Security

This week we took another significant step towards creating an internationally-leading infrastructure for training around cyber security within our #SOCLAB.
The step forward is the recruitment of three new graduate apprentices (GAs), and who will work with Satisnet and ourselves in the development of training around areas such as ransomware, DDoS, and data stealing.

If there’s one thing that the BA Hack shows, is that companies need to start to train their staff around cyber security events, and get them more aware of what they should look for. Every single person in a company has a role to play, from the security/threat/risk analysts and the development teams, to those responsible for physical security and for executive decisions, it is all about knowing your threats and dealing with them, and every single person in an organisation should be aware of the threats as they see them.

If you are into cyber security, and you don’t know Satisnet, then you should. They have a deep desire to make a difference in the training of security analysis, and in 2018 they won the IBM Community Award for their work with ourselves and Sheffield Hallam.
For many in the industry our existing training methods within cyber security just do now scale, and where we do not provide people with training around detecting, responding to, and investigating cyber security threats. Increasingly we need every single person in an organisation to be trained to detect the signs of a hack, and then be able to respond. That is not just stand-alone training, but observing how groups of people react to these threats.

We have seen a massive demand already for this type of training infrastructure, and our now finalisation a programme for the coming months which will train those from law enforcement, government, industry, and a wide range of organisations. Our new GAs will, in the first few months, be going through extensive training on Splunk, QRadar and AWS, and support our new training material. At the current time we have Cyber Kombat and vSoC (our environment we use for our undergraduate and postgraduate courses). Each of these creates a real-life environment for scenarios, and where we can play back scenarios for the trainees to learn, and which is safe and controlled.

It is our dream to build immersive training for cyber security that mirrors other industries. We see pilots training for scenarios that they hope will never happen, and industrial plant controllers training for worst-case scenarios, so why should we do this with cyber security professionals? Our partnership with Satisnet is the key to this, and it is one that will scale to all our graduates.

The BA, Equifax and Ticketmaster hacks show that organisations are being increasingly targeted for extortion, credit card steals, and a whole range of threats. We must thus increasingly invest in 20x7 monitoring of organisations, and detect threats (and stop them). For BA to be running for several weeks and where credit card details were being siphoned off for every single user, is not acceptable, and highlights a lack of investment in protecting customers. The days of 9–5pm monitoring of logs in IT systems has gone, and now we need to build systems which monitor in real-time, and can quickly make sense that something is not quite right. This means we may be taking billions of alerts each day, as we need every single one of them, as each of them could be the one that actually identifies a hack. We then need to make sense of them and try and correlate them onto a timeline.
Invest in incident response and data loss protection

You may think that your credit card details are the most precocious thing that a hacker can gain, but think again, as your health care record is probably worth a great deal more. Well the Ponemon Institute and IBM have just released their finding for health care data breaches for 2018, and it doesn’t make comfortable reading [here]:

A cost of $148 per record has increased the costs by 6.4% than 2017 (the average cost of a data breach is $3.86 million), but there’s a $14 per record saving if it involves an incident response team. South Africa had the worst track record in breaches (43%), while Germany had the best (14.3%).
The study found that the mean time to identify (MTTI) was 197 days (over six months), then thee mean time to contain (MTTC) was 69 days (over two months). Those who managed to contain a breach to within 30 days were identified as having considerable overall savings in their costs.
But many saw that the cost of Cyber Security is a saving in the long-term, but what are good investments in terms of data breaches. Well having an incident response team, using encryption, user training and threat sharing are all good investments, and moving to the Cloud, having third-parties involved, compliance failures and lost/stolen devices all lead to increased costs:
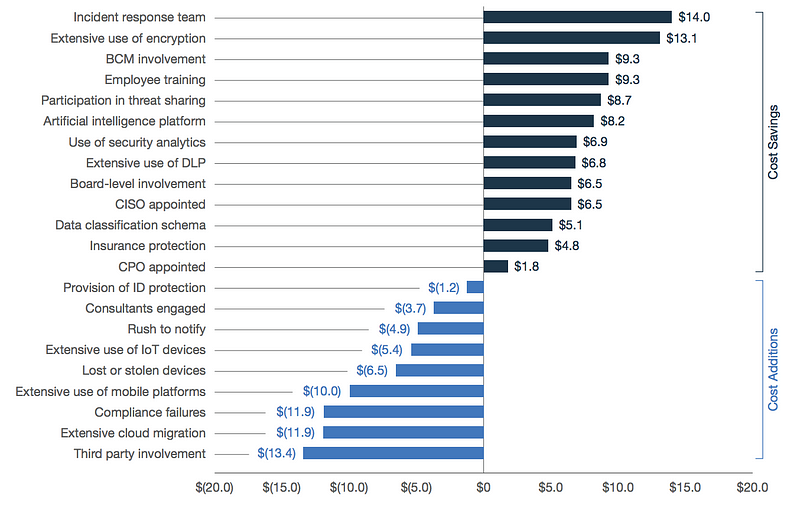
Perhaps worrying is the rust to report, especially with the requirement to report within 72 hours through GDPR. In terms of costings, Poneman classified these into four key areas:
- Detection and escalation. This includes the costs of auditing, incident response costs, and so on.
- Post data breach response. This includes the cost of providing help and support for those affected by the breach.
- Notification costs. This includes the costs of informing the organisation and individual affected (data subjects), including associated legal costs.
- Lost business cost. This includes the general loss of future business through brand reputation, and so on.
In terms of the factors which affected the overall cost of the breach, Poneman found that these were the key factors:
- The unexpected loss of customers following a data breach.
- The size of the breach or the number of records lost or stolen .
- The time it takes to identify and contain a data breach.
- Effective management of detection and escalation costs.
- Effective management of post data breach costs.
Selling it your CEO
The bottom line for many companies is the loss of business and loss of customers. For abnormal churn — which relates to a greater than average loss of customers — increased by 3.4% (with France, Japan and Italy having the highest abnormal churn rate), and highlights a significant factor in data loss. In health care and finance we see the greatest churn rate, with entertainment and the media having the lowest rates:

Conclusions
The recruitment of our three new GAs is another significant step along the track to build training which matches the threats we face. We need to radically change our approaches to the way the operate, and it all comes down to people, awareness and training. We need to invest in taking people and teams though scenarios, and show them how the should detect and respond. This is every single person in your organisation … including your board of directors.
We see many large banks invested intensively in cyber security, as they know that trust will build our future, and it will be the trust of shareholders and customers which will be key in this. Organisations need to understand this, and make investments in both secure infrastructures and monitoring, and the training of staff. Awareness will be key to the security of our future.

What is wonderful is that we have such as strong bond in our vision with Satisnet, and who clearly see the future, and are willing to invest in it.
To people like John McCann — Director of Satisnet and his whole team — I tip my hat. I wish our industry had more like him, and many just want to keep the status quo, and we continue to train our future workforce in the same old ways. John — and his team — has a passion and drive to address the core problems in our industry, and then pick partners who can help support that drive. We are proud to be a partner in this journey, as it is our shared vision, too.
The risks are too create to our economy, our critical infrastructure, and for our citizens for us not to invest in training. A single hack could bring down a company, and a single hack could bring down a country. It is all our responsibly to put in-place mechanisms to protect our infrastructure, and training and awareness must play the core part of this.
If you interested in your company getting involved, please contact us. You can follow us on Twitter here.
If you want us to pop into your company for an hour or two, just say, we have some “fun” content to both scare and amuse. We have done our “fun” awareness session with many organisations across Scotland, and we are now being invited to present in companies in England, so just give us a call, and we will help engage staff into cyber security. And then … we might even see them in our SOCLAB in the future.