Data Security and Resilience using Secret Shares and Elliptic Curve Methods
Data Security and Resilience using Secret Shares and Elliptic Curve Methods
Our data structures are often not secure, and these are especially at risk when we use public cloud systems. Along with this, we become highly dependent on specific cloud systems. Over the past few years, all the cloud infrastructures have had significant outages, and thus we need to build-in resilience into your data storage, and where we can cope with an outage.
In our data centres, we often use RAID 10, and where we stripe and mirror data across disks, and where a failure of one or more disks does not lose any of the data. So can we re-create this type of system without our Cloud-based architectures, but still be ultra-secure? The answer is yes, and I’ll show you a method which achieves this.
Threshold schemes
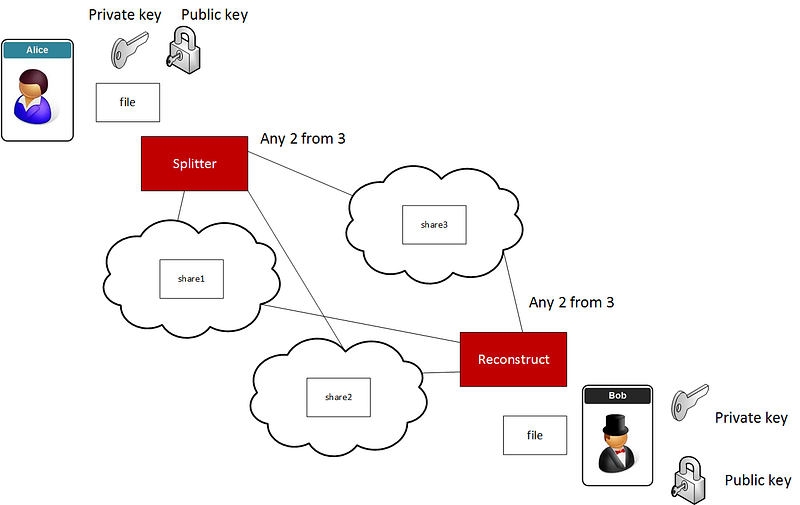
A threshold scheme allows us to create a number of secrets and then define a threshold number of the shares to come back together again. If we have n shares we can define that t shares need to come back together to reconstruct the original data.
What we want is for Bob and Alice to generate a key pair (either for the session or long-term keys). They will then pass their public keys to each other, and at the end will have a shared key. This key is then used to secure each of the shares:

Generating a shared key with Elliptic Curve
The starting point of the method is for Bob and Alice to agree on a shared key. For this Alice will create a private key (a) and Bob will create his private key (b). Each of them will then generate their public key with aG (mod p) and bG (mod p), and exchange these values:

Generating and reconstructing the shares
Next Alice will split a secret message (m) into a number of secret shares (n) and which have a threshold of t. She then converts each of the shares into points on the elliptic curve with Pᵢ=mᵢ+abG:

These points can then be passed to Bob. He will take t points and then compute m ᵢ=P ᵢ−abG [demo]:

A sample run is for a threshold of 2 and with 4 shares is [here]:
===================================
Elliptic curve: SECP256k1 Parameters
G_x= 0x79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798L
G_y= 0x483ada7726a3c4655da4fbfc0e1108a8fd17b448a68554199c47d08ffb10d4b8L
Order: 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141L
===================================
===================================
t: 2
n: 4
===================================
===================================
Original key 0x1b39b5771afbe1a01928e87c957a55a9681586f836593b7ad63f5cf5cbc85576L
===================================
===================================
Share 0x3defd23c1ec75f353d9917e9c12f78270ae74f589ad00e030935c0f4f2cbaa6L Verified: True
Share 0xec8444d068dd0a468e8a3a80a2ab995a33f63fd98c4966814ab9b9b5a2c76117L Verified: True
Share 0xd5298c7d0fcd9e99c93ae382a9443b333c8f2dd6df9d2be6a50db8cf262bc647L Verified: True
Share 0xbdced429b6be32ed03eb8c84afdcdd0c45281bd432f0f14bff61b7e8a9902b77L Verfied: True
===================================
Reconstructed key: 0x1b39b5771afbe1a01928e87c957a55a9681586f836593b7ad63f5cf5cbc85576L
===================================
Original message: 5555
Reconstructed message: 5555.0
An application
An application of this is to split up the shares and then distribute them over different cloud systems, and then reconstruct from t shares. In this way we get both security and resilience, and one cloud could fail, and we would still be able to reconstruct the data:

Conclusions
Our key focus for the future is to build both security and resilience into our data infrastructures. Shamir’s shares can thus play a core part in creating these.
Here is a presentation based on this page: