Your Coffee Shop Wi-fi Can See What You Are Connecting To …

Your Coffee Shop Wi-fi Can See What You Are Connecting To …
We connect to public wi-fi systems and think that we are not giving away the sites we are visting, as we are using HTTPs connections. But think again, our DNS requests reveal the sites we are connecting to. Also the start of the TLS connection actually reveals the site we are connecting to.
So in our sticking plaster world of security, we leak lots of information. One of these things are the servers we connect to. Cloudreach is one of the leading companies in the world which is trying to force the industry to plug the games around DNS and TLS. They would like to see the world moving to TLS 1.3 as quickly as possible.
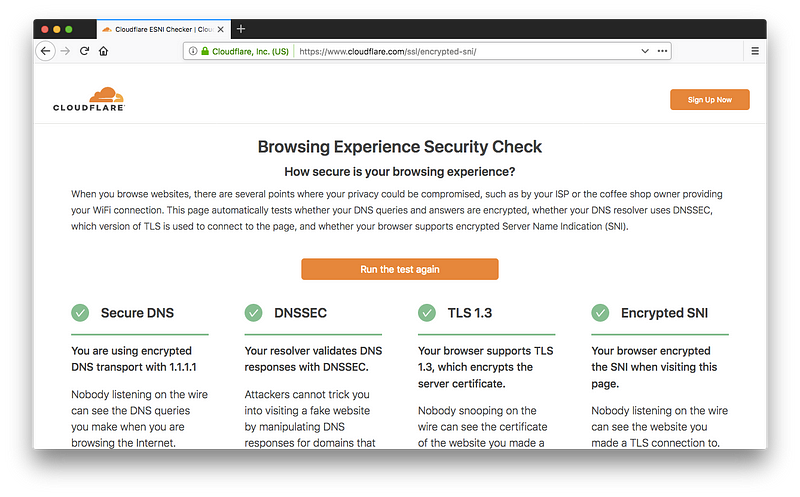
And so Cloudflare have just announced that they have implemented ESNI (encrypted Server Name Indication (SNI) TLS extension). This aims to stop ISPs and public wi-fi providers from snooping on your Web accesses (or anyone else who listens to your network packets). The first integration is within Firefox Nightly, and you can test your browser here:

Cloudflare are also pushing to secure DNS requests, while driving the move toward DNSSEC and TLS 1.3. Once ESNI is enabled, it should show the following:
Cloudflare has released Wireshark traces to show the difference. The following shows a normal TLS and where we see the server name (cloudflare.com) within the TLS packet:

If the encrypted SNI extension is now added we get:

A TLS connection should be secured and tunnel, but in the initial negotiation with the Client Hello we reveal the server name, and which can be seen by anyone listening to our network packets.
Method
With ESNI, the server with a DNS record publishes its public key. The client then changes the SNI extension to an encrypted version. The key used is a symmetric key derived from the server’s public key (using Elliptic Curve Diffie Hellman key exchange). The associated server which owns the associated private key can also derive the same symmetric key, and can decrypt the extension. This can only work with TLS 1.3 and above. With TLS 1.2 and below, a snooper can examine the digital certificate that is sent from the server to the client, and thus determine the site to which the user is connecting to.
Conclusions
TLS 1.0, TLS 1.1 and TLS 1.2 need to be dumped, asap. We need to improve DNS, too. Well done to Cloudflare in pushing the industry forward. Google has changed the world with their drive for HTTPs. We need to do the same with some of the other protocols, and properly plug the gaps we have created.
Here is an article on TLS 1.3:
So after nearly four years and 28 drafts, the IETF (Internet Engineering Task Force) has finally pushed TLS (Transport…medium.com
Sometime, soon, our 20th Century Internet needs to be switched off, and replaced with one which truly respects the rights of our citizens to privacy.