Your Headphones Might Break The Security of Your Computer

Your Headphones Might Break The Security of Your Computer
Sennheiser has now been pinpointed as have a major security vulnerability in its HeadSetup app. It involves a self-signed TLS signature and which Sennheiser placed in the Trusted Root CA Certificate store (or in the macOS Trust Store). This means that this certificate can be used to validate other certificates, as the private key on the certificate could be easily extracted.
Once the private key is derived, it is then possible to sign for maliciously installed applications, as we have a trusted root certificate. The password on the certificate was SennheiserCC, and was found by reverse engineering the HeadsSetup application and finding the configuration file :

To prove vulnerability, Secorvo spoofed a Google certificate, along with other audio companies [CVE-2018–17612]:

The spoof certificate was:
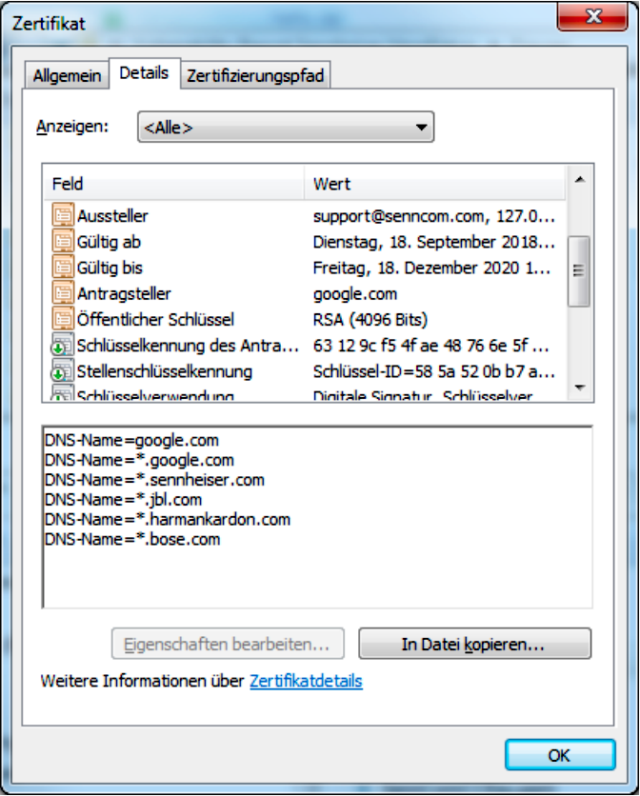
In the install, the self-signed CA certificate is from CN of SenncomRootCA , and is valid until 2037, and is stored in the SenncomRootCA.cert.pem file. The pem file is actually encrypted with AES (using AES-128-CBC), but the testers searched for the key within the application, and found that the key was contained within WBCCListener.dll:

SuperFish
A similar hack vulnerability occurred with Superfish.
As PC vendors have found their margins reducing, they have looked to other ways of creating a business case, such as including third party tools into their pre-installation list. Most users, though, dislike this type of software, and will often avoid those with bloated pre-installs. Sometimes, though, it can work well, especially when it integrates security products like virus scanners, and with demo versions of Microsoft Office, but it works less well with untested tools, especially ones which integrate with the default Web browser or interfere with the security settings of the computer.
These additions on the pre-install list are often referred to as shovelware, where vendors care little about the actual usefulness of the software, and do very little in the way of due-diligence. Often it includes games which have backdoors and which could reveal user activity, or have ways to trick users into paying for subscriptions to play on-line games. More often these days, the focus is on understanding what users like to browse, and then pushing content to them. Increasingly targeted marketing has become a key focus, and where Web search results from trusted sites, like Google, are tampered with before they are presented back to the user.
Lenovo created an embarrassing “own goal” by including Superfish, which is software alters search results, and then produced information of competing lower-priced products, whenever the user moves their mouse over the search results. Unfortunately it also crippled the Web browser’s security, using a third party library do perform an SSL connection, and allow intruders to listen to the communications.
SSL redirect
For Lenovo, the pre-installed software, named Superfish, altered search results to show related advertisements, and is well known to many who inadvertently install adware into their browser. So rather than search Google, the browser redirects the results back, and adds it own for the search query. Unfortunately it also allows intruders to see the search queries, even though it looks like you are communicating securely with Google.
Whenever communications are secured in a browser, the remote Web site sends its public key for the client to create an encryption key for both the browser and the server to use. In this way a secure tunnel is setup. In Superfish, the private key has been discovered, as the digital certificate containing the public and private key has been included in the software, and has since been hacked.
At the core of the problem is the tricking of the Web browser into thinking it is connected to a trusted site, but actually the data within the secure communications is created by another application. At the core of the security issues is the usage of SSL hijacker software (Komodia Redirector) developed by Komodia.com:

The Komodia Redirector product says:
Komodia’s Redirector allows you to change TCP/IP network sessions with a few simple clicks. The platform intercepts traffic on the local machine based on rules that you define, and it includes many built in functions that you can use without writing a single line of code (if you need a solution that only sniffs the network traffic without modifying it, visit Komodia’s Interceptor web page).
So we have a piece of software that can trick the user into connecting to an incorrect Web site, without the browser actually knowing that the data is going to the wrong place. This would, in itself, be a particularly bad breach in security, as it tricks the browser into thinking it has a secure connect to a remote site.
What broke Superfish?
As if the communication redirection of the SSL session was bad enough, the final nail in the coffin was that Komodia embed their root CA certificate into the software. This certificate contained both their public and private key — which should never happen, as the private key should never be shared. This certificate has been easily broken by brute forcing the password on it, allowing the private key to be gained.
The private key is the thing that is used to read the data contained in the secure tunnel, so any intruder with the private key of the root certificate can view the data in the secure connection.
So it is a bit like you finding the best locks to secure your home, and then putting the keys for the locks under a plant pot. Many encryption systems are compromised in this way, as secure keys are used for the encryption, but the keys are actually protected by a simple password.

Figure 2: Abstraction of vulnerability
In the end, the password on the private key was cracked within 10 seconds, and had a password of … you’ve guessed it … “komodia” (which is the same name as the company who procedure the SSL redirector). [Method].
Conclusions
To have a self-signed certificate installed as a root certificate is negligence of the highest level for a company such as Sennheiser. For some reason, software developers often forget to turn off debug features, and then do little in the way of testing before applications are pushed out.