Meet Troika — A Hashing Method Fit For IoT Blockchains?

Meet Troika — A Hashing Method Fit For IoT Blockchains?
When there’s a new crypto method, it’s like an early Christmas present for me. And so the Troika hash takes to the stage. It has been designed to integrate with the IOTA distributed ledger, and aims to be one of the most secure and energy efficient methods around. Before I outline it, we need to understand why we need a new hash signature, and why we need one that is fit for IoT devices.
Why?
One of the greatest challenges that we have on the Internet is the scale-up of devices within an IoT era. For this organisations may have millions (or even billions) of devices which must be monitored and controlled, and then discover the current state of the overall network infrastructure. Most existing system would struggle at a large-scale to create a current consensus of the infrastructure, but IOTA -with its Tangle engine — can report on the current state, along with previous states [here].
Along with scale, the greatest challenge in a world of IoT devices is that we can often have devices with limited capabilities. This might related to the number of transistors that can be supported on the device, or the amount of memory. But the greatest challenge is often energy consumption, and where we have device that have extremely limited power drain capabilities. For this we cannot use our existing energy-consuming cryptography, and thus need to implement methods which optimize for battery drain. In many cases, too, we have passive devices — which have no battery source — and which must draw their power from the radio wave which is applied to the device. And so the world is looking for new cryptography methods which are secure, robust, fast, and efficient. The first to focus the world on defining new standards for hashing methods for IoT was NIST.
The NIST Competition
Researchers in Canada have defined that the SHA-3 method will take longer to crack that the time that the universe has existed. The total time to crack, with some of the best cracking hardware around, is 10²⁹ years or 1,000,000,000,000,000,000,000,000,000,000 years to crack the hash.
SHA-3 was known as Keccak and is a hash function designed by Guido Bertoni, Joan Daemen, Michaël Peeters, and Gilles Van Assche. MD5 and SHA-0 have been shown to be susceptible to attacks, along with theoretical attacks on SHA-1. NIST thus defined there was a need for a new hashing method which did not use the existing methods for hashing, and a competition for competing algorithms.
In October 2012, Keccak won the NIST hash function competition and is proposed as the SHA-3 standard. It should be noted that it is not replacement SHA-2, which is currently a secure method. Overall Keccak uses the sponge construction where the message blocks are XORed into the initial bits of the state, and then inevitably permuted.
The sponge function takes a simple function f and involves a number of stages, and where we create a fixed output (dependent on the bit length of the hash function). Simple operations of XOR, AND, and bit shifts are used, and which leads to a fast generation of the hash function:

The f permutation function takes a variable-length input and produces an arbitrary output length. A is the bit rate, and each f function operates on b bits, and where a capacity is defined as c = b — r.
The SHAKE method is useful as it can be used to create a hash method of a variable length. For the 128-bit version will produce a hash value is 32 hex characters.
The contenders
NIST published the new standard, based on Keccak, on 5 August 2015 [here], and which beat off competition from BLAKE (Aumasson et al.), Grøstl (Knudsen et al), JH (Hongjun Wu), and Skein (Schneier et al.). After two rounds the final round an evaluation of security, performance and hardware space. Blake and Keccah did well in terms of the number of gates which implement the methods:

But it was in throughput that Keccak really shone, and beat the others by at least a factor of between three and four:
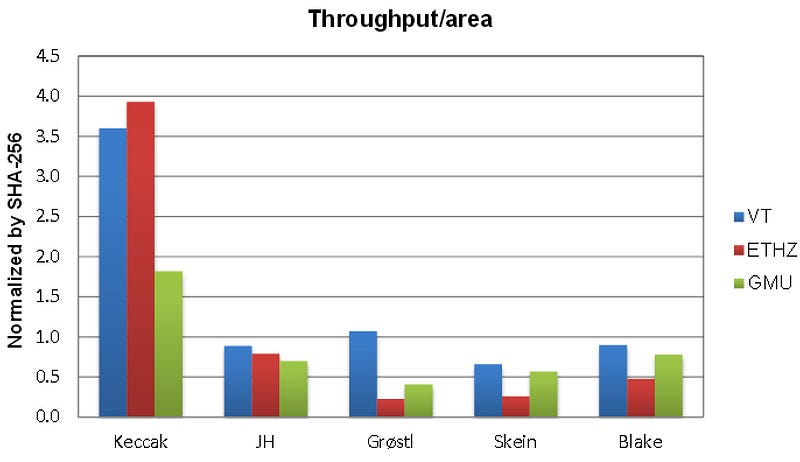
With energy consumption becoming a major factor within mobile devices and for IoT, the energy consumption for Keccak again trumped the other finalists:

In this Keccak consumed less than half of the power per bit than Blake.
Note: The tests were conducted by ETHZ — Eidgenössische Technische Hochschule Zürich, VT — Virginia Tech and GMU — George Mason University.
Troika
The IOTA method supports a fast consensus of the overall state of an infrastructure, and without the use of energy guzzling miners. Unfortunately, the curl hash function in IOTA had a core problem, and the Foundation has since been engaging with top professionals in the field in order to help build a more secure and robust infrastructure.
The problem was initially identified by Ethan Heilman et al in Sept 2017 and published [here]:

A follow-up paper [here] formalised the results around the weaknesses around collisions within the Curl hash function. A deep analysis of the Curl source code identified that it could be broken through differential cryptanalysis.

For the new hash method, the IOTA Foundation turned to Dr. Andrey Bogdanov (see photo on the left-hand side), and his Cybercrypt team. The overall objective was to create an ultra-secure lightweight hash that was fit for IoT. Unfortunately existing hash functions — such as with SHA-3 — do not directly work with the data messages that IOTA uses.
The result is Troika — the Russian for a vehicle pulled by three horses — and which is the proposed IOTA hash for its distributed ledger, and which operates on ternary messages [here]. These types of messages are represented by trits {-1,0,1}, and which is a base-3 balanced numbering system. Within IOTA we also have the concept of a tryte which is 3 trits and which can represent 27 states. These states are then named with uppercase letters (A-Z) and the “9”. The message “Hello”, for example, is translated into the trytes of “RBTC9D9DCD” [here]. An IOTA hash and seed has 81-tryes.
A transaction in IOTA has 2,673 bytes, and includes:
- Hash (81-tryes). This is the hash of the transaction, and is the focus for the Troika method.
- Signature (2,187-tryes). This is the signature created by the private key of the entity.
- Address (81-tryes). This is the address of the referenced device.
- Value (Integer).
- Timestamp.
- Nonce (81-tryes). This relates to the proof-of-work undertaken.
As with SHA-3, Troika uses a sponge-based construction, and has an output length of 243 trits, and with a state of 729 trits using a rate r of 243 trits and capacity c of 486 trits (and which matches SHA-3). At present it is thought to be robust against most attacks, including differential and linear cryptanalysis, diffusion properties, meet-in-the-middle attacks, algebraic attacks and invariant attacks.
But, the only true way of testing that it is secure is to challenge the research community to break it. For this the IOTA Foundation has created a 200K Euro bounty for anyone who can crack it [here]:

Conclusions
The Bitcoin-type blockchain (Blockchain 1.0) is old and crumbling, and the DApp approach (Blockchain 2.0) -such as with Ethereum — still needs its proof of work and miners. But, in an IoT era, we need new ways to understanding the current state of our infrastructure, and the DAG approach provides this. This new hashing method should hopefully progress its adoption, and see some serious work towards creating scaleable and security IoT infrastructures.