The Application That Made The Internet Is Now It’s Greatest Flaw

The Application That Made The Internet Is Now Its Greatest Flaw
So what is nearly 50 years old and drove the adoption of the Internet? Well it’s good old email. And so, in 1971, Ray Tomlinson sat beside two computers in Cambridge, Massachusetts, and transferred a single message of …
QWERTYUIOP
From there, email has been the driving force for the adoption of the Internet, and is the application that most shapes our digital world. The simplicity of the method and the usage of the “@” symbol, just worked so well, along the ability to attach files. It truly build the foundation of our information age. And so, SNDMSG, READMAIL and CYPNET (the program to attach files) were born, and basically, after a good few RFCs and several decades, the actual methods involved with email have never really grown up.
The special child who never really grew up
They are basically stuck in the 1980s, and have never grown up. Underneath, the Lotus ccMail package that I used in the 1980s is not that different from the Microsoft Outlook client that I use now. It still does the same thing, and cares little about the actual trustworthiness of the messages that I receive. We now have a whole lot of filtering going on to guess when something is credible or not, but it doesn’t actually work! Thus a system administrator in 2019 can still look at all the emails on the system in the same way they could in the 1980s, and a person who has access to your password can read all of the emails that you have read and sent.
Building the foundation
The foundation we have now with email was basically formed at the start of the 1980s with the creation of RFC821 (Simple Mail Transfer Protocol — SMTP) and RFC918 (Post Office Protocol — POP). These protocols allowed for the sending (SMTP) and reading of emails (POP). With this, system designers could break away from the monopolies created by large computer manufacturers and create software which could integrate across different systems. These standards did not now have to go across international standards agencies, they were published as RFCs, and then rapidly adopted.
But, there was little in the way of security build into it, and there was no thought about protecting the message in any stage of its transmission, or in authenticating systems or users. Even though public key encryption had just been discovered at the end of the 1970s, the designers of the Internet thought little about the scope of their work, as they were often using private networks.
It was then up to Netscape in 1994 plug a gap with the release of SSL v1 (and which was since caused so many problems, such as with Logjam and BEAST). For this, they secured the machine-to-machine part of the communication, and making sure that the server was properly authenticated, and that a tunnel existed for the transmission and reading of emails.
But still system administrators, cyber criminals and spies could still view the emails as they sat on local systems in plain text format. The cracking of a password was all a cyber criminal needed to gain access to sensitive emails, and for system administrators, it was just sys admin access that was needed.
The single greatest problem refuses to be fixed
And so, we are still here. Email is the single greatest problem in cyber security, from a technical, social and organisational point-of-view. Most of the hacks on corporate systems happen through phishing emails or through social engineering through email. We seem incapable of plugging the gap that leaves our systems wide open.
The solution is the usage of proper end-to-end encryption systems such as Telegram and WhatsApp, but these keep law enforcement awake at night, and are the nightmare scenario. And so we have on one side, cyber criminals, some governments and law enforcement, and on the other the rights to privacy and consent on the other side. Fortunately, GDPR has been placed very much on the side of the rights to privacy.
PGP is still the only show in town?
While companies such as Google are now showcasing their secure email solutions, they are not proper models of a truly secure email infrastructure. This would scare them, as it shuts the door on a whole range of things that they want to do — such as mining your emails for interesting things. If Google was to offer you a discount on that new laptop you want to buy, just because you showed interest in buying one, then you might consider allowing them to read your emails, but, in most occasions we are often uncomfortable about seeing an advertisement for something that we have just sent in a personal email. A single email to your dentist will often propagate to advertisements on Twitter, LinkedIn, and other platforms for tooth-related products.
There has been a long history of defence agencies trying to block and control high-grade cryptography. The US government took copies of encryption keys through its Clipper chip, attempted to prevent publication of the RSA public key encryption method, and dragged Phil Zimmerman through the courts after claiming his PGP (“pretty good privacy”) encryption software leaving the country was tantamount to illegally exporting weapons.
But Phil’s software was the answer — and still is — and which properly used encryption to build up trust. It used public key encryption to prove the sender (Bob) and carry his unique session key, and symmetric key encryption to encrypt the message, and a hashed based signature to prove that Eve hadn’t tampered with it:
The magic happens …
With PGP, we sign a hash of the message with our private key, so that the other side can check the sender (and that the message hasn’t been changed). We then create a new encryption key for every message, and then just need to encrypt this key with the other side’s public key. The receiver then receives the message, and decrypts the email encryption key with her private key, and reads the message. After she takes a hash of the message, and then decrypts the encrypted hash with Bob’s public key, and checks the result. If the values match, she has proven the sender and that the message hasn’t been changed:
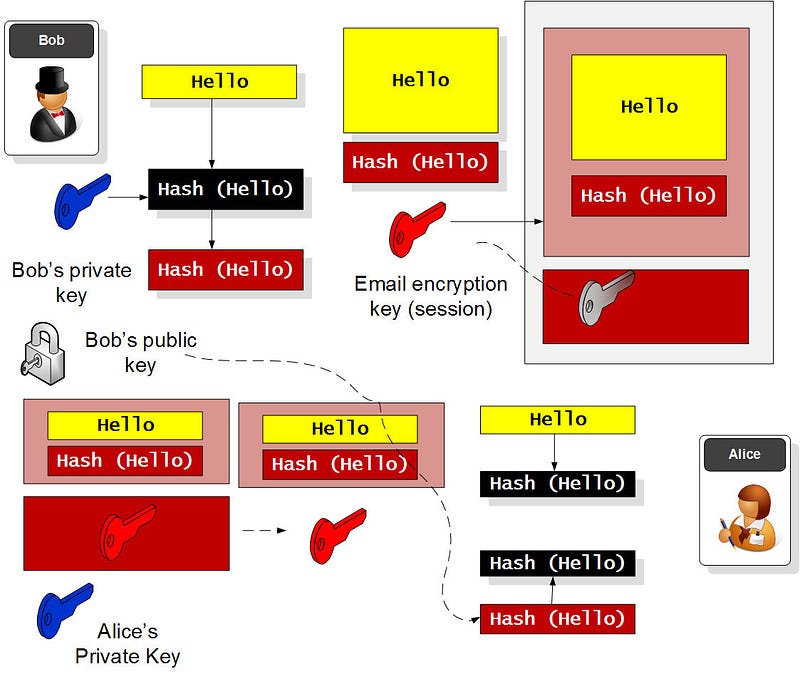
So what has gone wrong in the adoption of secure email? Well, we haven’t found a method where users can easily register their public keys, and for software to support the proper signing of email. Microsoft Exchange has never really properly supported signing and encryption, and it is left to third-party plug-ins, which aren’t easy to use.
An old software world v a new open world?
And here we are in 2019, and we are really stuck in the 1980s, but the world has moved on from C++, Windows and DOS. Our new world is not full of servers and DLLs any more and heavy weight coding systems, it is Web-based, and we have gone open, in order to free ourselves from the companies who wish to close our information world, and make money from us. They have often stifled innovation, as companies blindly reliance for the same old software.
But a new world is evolving, it’s a scripted and open world, and is full of Docker, Node.js, Cassandra, and Python. For the first time we are breaking out of the 1970s and 1980s, and building systems which are free and open to all. In this new world, you don’t have to be a software engineer to build complex information systems, the world is their for everyone to build their own world. This new world grows not within the R&D labs of the monopolist information companies, but with GitHub. The true controllers of the future of our digital world will be the owners of GitHub repositories.
And so in a Node.js world, how does Bob create his keys (a public one and a private one) so that Alice can send him a secure email. We, it’s a simple “npm install openpgp”, and we are away [here]:
const openpgp = require('openpgp')
var name1='bill';
var email1='[email protected]';
var args = process.argv;
if (args.length>1) name=args[2];
if (args.length>2) email=args[3];
openpgp.initWorker({ path:'openpgp.worker.js' }) // set the relative web worker path
var options = {
userIds: [{ name:name1, email:email1 }], // multiple user IDs
numBits: 512, // RSA key size
passphrase: 'password' // protects the private key
};openpgp.generateKey(options).then(function(key) {
var privkey = key.privateKeyArmored;
var pubkey = key.publicKeyArmored;
var revocationCertificate = key.revocationCertificate;console.log(pubkey);
console.log(privkey);
});
A sample run with 512-bit RSA keys is:
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: OpenPGP.js v4.4.5
Comment: https://openpgpjs.org
xk0EXEOYvQECAIpLP8wfLxzgcolMpwgzcUzTlH0icggOIyuQKsHM4XNPugzU
X0NeaawrJhfi+f8hDRojJ5Fv8jBI0m/KwFMNTT8AEQEAAc0UYmlsbCA8Ymls
bEBob21lLmNvbT7CdQQQAQgAHwUCXEOYvQYLCQcIAwIEFQgKAgMWAgECGQEC
GwMCHgEACgkQoNsXEDYt2ZjkTAH/b6+pDfQLi6zg/Y0tHS5PPRv1323cwoay
vMcPjnWq+VfiNyXzY+UJKR1PXskzDvHMLOyVpUcjle5ChyT5LOw/ZM5NBFxD
mL0BAgDYlTsT06vVQxu3jmfLzKMAr4kLqqIuFFRCapRuHYLOjw1gJZS9p0bF
S0qS8zMEGpN9QZxkG8YEcH3gHxlrvALtABEBAAHCXwQYAQgACQUCXEOYvQIb
DAAKCRCg2xcQNi3ZmMAGAf9w/XazfELDG1W35l2zw12rKwM7rK97aFrtxz5W
XwA/5gqoVP0iQxklb9qpX7RVd6rLKu7zoX7F+sQod1sCWrMw
=cXT5
-----END PGP PUBLIC KEY BLOCK-----
-----BEGIN PGP PRIVATE KEY BLOCK-----
Version: OpenPGP.js v4.4.5
Comment: https://openpgpjs.org
xcBmBFxDmL0BAgCKSz/MHy8c4HKJTKcIM3FM05R9InIIDiMrkCrBzOFzT7oM
1F9DXmmsKyYX4vn/IQ0aIyeRb/IwSNJvysBTDU0/ABEBAAH+CQMIBNTT/OPv
TJzgvF+fLOsLsNYP64QfNHav5O744y0MLV/EZT3gsBwO9v4XF2SsZj6+EHbk
O9gWi31BAIDgSaDsJYf7xPOhp8iEWWwrUkC+jlGpdTsGDJpeYMIsVVv8Ycam
0g7MSRsL+dYQauIgtVb3dloLMPtuL59nVAYuIgD8HXyaH2vsEgSZSQn0kfvF
+dWeqJxwFM/uX5PVKcuYsroJFBEO1zas4ERfxbbwnsQgNHpjdIpueHx6/4EO
b1kmhOd6UT7BamubY7bcma1PBSv8PH31Jt8SzRRiaWxsIDxiaWxsQGhvbWUu
Y29tPsJ1BBABCAAfBQJcQ5i9BgsJBwgDAgQVCAoCAxYCAQIZAQIbAwIeAQAK
CRCg2xcQNi3ZmORMAf9vr6kN9AuLrOD9jS0dLk89G/XfbdzChrK8xw+Odar5
V+I3JfNj5QkpHU9eyTMO8cws7JWlRyOV7kKHJPks7D9kx8BmBFxDmL0BAgDY
lTsT06vVQxu3jmfLzKMAr4kLqqIuFFRCapRuHYLOjw1gJZS9p0bFS0qS8zME
GpN9QZxkG8YEcH3gHxlrvALtABEBAAH+CQMI2Gyk+BqVOgzgZX3C80JRLBRM
T4sLCHOUGlwaspe+qatOVjeEuxA5DuSs0bVMrw7mJYQZLtjNkFAT92lSwfxY
gavS/bILlw3QGA0CT5mqijKr0nurKkekKBDSGjkjVbIoPLMYHfepPOju1322
Nw4V3JQO4LBh/sdgGbRnwW3LhHEK4Qe70cuiert8C+S5xfG+T5RWADi5HR8u
UTyH8x1h0ZrOF7K0Wq4UcNvrUm6c35H6lClC4Zaar4JSN8fZPqVKLlHTVcL9
lpDzXxqxKjS05KXXZBh5wl8EGAEIAAkFAlxDmL0CGwwACgkQoNsXEDYt2ZjA
BgH/cP12s3xCwxtVt+Zds8NdqysDO6yve2ha7cc+Vl8AP+YKqFT9IkMZJW/a
qV+0VXeqyyru86F+xfrEKHdbAlqzMA==
=5NaF
-----END PGP PRIVATE KEY BLOCK-----
And so, I send you my public key, and you put it on your key ring, and when you send a message to me, you take my public key off your key ring, and then use it to encrypt the session key that you have used to encrypt the body of the email. Isn’t that perfect? A unique key is used for every message, and generated by the sender. Only you can discover it! The sender also signs a hash of the message with their private key, and then I can then prove the sender by checking their public key, and also prove that the message is unchanged.
We need more trust …
The methods that PGP illustrates is the way that the Internet should work, and those calling for Blockchain, DLT, DAG, and so on, just want an Internet which is a great deal more trusted, and one where we will not receive spam emails, unless they are actually signed by someone. Google forced the Internet to adopted Https, as they were forcing the industry to look after its users. You still see companies posting messages of:
“We have nothing that is sensitive on our pages, so we only use a digital certificate on places where there is payment details”
They thus just don’t get what the certificate is doing a whole lot more than creating a secret tunnel, and it is mainly there to validate that the site can be trusted, and that no-one can install a back-door on your computer and which can spy, change and re-direct things.
Putting citizens rights first and legacy last
The citizen must thus be at the heart of this new Internet we are creating. They must have control over their digital world, and must be given back rights, as the Facebook model of harvesting data for little in return needs to change. Organisations, too, need to understand the sensitive information that they have, share and transmit, and it’s only with methods such as PGP that this can be done properly.
And so do we really want to build a more trusted digital world, or just keep pushing the applications that think that it is the 1980s? With SSH and PGP, we are now building a new foundation, so go understand how they work, and build a more trusted world. If you’re a developer or a cloud architecture, you will know the importance of building proper trust, as our data is now accessible by anyone with an Internet connection.
So, if you are in any cyber security role, would you know how to send a secure email without using a GNU? If the answer is no, they go and learn how to with a command line and some keys. You need to get your management team switched on to the real threats that this data-drive world holds, and in how we can build more trusted systems, … with cryptography, ZKP, DLT, Blockchain … call it want you want … we are now building systems properly, and have ‘security by creation’. We have reached breaking point, and can’t continue with our 1980s viewpoint of our world. We must move to the 21st Century, and we can now build the Internet properly.