Pushing SWIFT into the 21st Century

Pushing SWIFT into the 21st Century
SWIFT selects Blockchain over Ripple
We cannot underplay the role that our global finance infrastructure plays in our ever day lives, and any risks of it collapsing would cause major damage across the world. And so we should all know that the SWIFT network has major problems — often its trustworthiness is based on sequences of numbers — and must increase its overall trust. At the core of this must be a strong cryptography infrastructure and a fast consensus mechanism, along side the integration into a Merkle Tree.
You can call it blockchain, distributed ledgers, or whatever you want, but basically it’s creating a consensus that a transaction has been checked that is it correct, and then putting it into a Merkle Tree along with a trusted signature.
After a period of evaluation, SWIFT have now announced that they will be starting a trial using R3’s open source blockchain method. This comes as a shock to some people in the industry as Ripple was seen to be the main contender for fast trans-national payments. Many will wonder about the effect that SWIFT going with R3 will have on the XRP cryptocurrency, but we can see that it seems to have had a positive effect, with a rise of over 11% on the day of the announcement:

Overall SWIFT is a global financial network which involves the transfer of billions of dollars of currency each day and which is co-operative that is owned by 3,000 financial institutions. Carolyn Maloney, a Representative in Congress, wrote to the top banking regulators to request measures to strengthen the security of the network. The level of sophistication shown in the recent attacks shows that there is increasing investment and skill used to compromise the infrastructure. Her focus is related to stolen Swift credentials.
In the UK, the Bank of England has ordered UK banks to test their cyber security in order to reduce the exposure to the Swift hack. This includes completing an Indicators of Compromise review that has been created by BAE Systems after had investigated other attacks. Keys aspect are to review and check the users who can access the network.
Where’s there’s money and flaws, there’s crime
Where there’s money, you will find criminals, and the SWIFT network is often a target for those who want to get rich quick. There are thus few crimes that have such a high financial reward, and for such little chance of being caught. While SWIFT has provided a way for us to integrate our banking infrastructure over the world, it has been an increasing targeted hacks, and a recent one on 13 August 2018 focused on the core SWIFT/ATM infrastructure of the Cosmos Bank. In the end, it is thought that $13.5 million was taken.
There have been a number of previous hacks of the SWIFT network, including:
- In February 2016, $81 million had been stolen from the Bangladesh central bank, and that there were a number of other recent incidents.
- Last year, Wells Fargo transferred $12 million from Banco del Austro in Ecuador but it is now believed that these funds have been stolen by hackers.
- A week ago, Tien Phong Bank, a Vietnamese lender, outlined that it stopped a theft of over $1 million on the Swift network.
There are allegations from both sides that the other is to blame, with weak security being pinpointed at the Bangladesh Bank, and where it was stated that engineers left several security holes with its connection from the real-time gross settlement (RTGS) system into Swift network.
Cosmos Bank Hack
The researchers at Securonix have now identified that the attack that was built with a layer approach(a progressive attack) and they pinpointed North Korean hackers (possibly from the Lazarus Group). In investigating the crime, they found that the hackers breached an ATM switch within the SWIFT network and then created two routes which allowed the money to be siphoned off.
It is thought that it involved either a spear phishing attack or an attack against a remote administration service. This allowed the attackers to gain a foothold on the network, and go further. After this, it is thought that the attackers used ATM test software to set up a malicious proxy switch. This created a fake ATM switch which ran in parallel with the bank’s ATM infrastructure, and which then sent fake transactions into the network.
An ATM switch should send an ISO 8583 message to the back-end infrastructure, but this was never received. The fake transactions are then not sent to the back-end infrastructure for checking and sent to a shadow server which authorises the transactions. The transactions included: 2,800 domestic transactions (Rupay) and 12,000 Visa transactions using 450 cloned debit cards, along with another $2 million for a SWIFT inter-banking transfer. This hack is by far more serious than the usage of malware installed on ATM machines, as it attacks the core of a bank’s ATM infrastructure.
The SWIFT Network
The headquarters of SWIFT is in Belgium, and it supports a global network (SWIFTNet) of over 9,000 financial organisations in order to transfer of funds between banks using Business Identifier Codes (BICs), which are also known as “SWIFT codes”. At present there are around 15 million messages per day, and where the network does not hold any of the account details of its members, nor does it clear the transaction. For this it sends payment orders which are then settled by the target of the transaction. Any company which uses the SWIFT network must have a business relationship with an associated member.
The BIC value uniquely identifies the name and country of the bank — and possibly the branch. It was either 8 or 11 characters long. The Bank of Ireland’s BIC has an eight character code which is BOFIIE2D: BOFI (4 digit code for the bank); IE (Ireland ISO Code); and E2 — Location Code. We can also add a three-digit branch code to the end.
A recent hack involved three “fraudulent remittances” and which were sent to accounts in Dubai, Turkey and China. These included remittances of $1million, $372,150 and $500,000 and sent through Standard Chartered Bank accounts. The $500,000 and $372,150 remittance payments have since been blocked. This comes on the back of the same bank being involved in a suspected $1.7 billion fraud using unauthorized loans to bank employees.
Spoofing
The announcement around the Bangladesh bank hack said that there had been a number of fraudulent messages, as the hack involved modifying Swift’s software on back office computers within the Bangladesh central bank, in order to hide the transaction.
It is thought that the intruders obtained valid operator credentials using a “spoofed” ID, and which can create and approve Swift messages. They then submitted fraudulent messages based on the identity of those they are spoofing.

Only as strong as the weakest link
Swift connects 11,000 banks across the world and carries more than 25.8 million messages per day, with around half of these being money transfers. BAE reported that they have found malware that could have been used for the Bangladesh Bank in an online malware repository. It is reported that intruders setup a transfer of $951 million from Bangladesh’s central bank holding at the New York Federal Reserve to the Philippines and Sri Lanka.
The transfer to the Philippines (for $81 million) was successfully transferred, and to two Chinese businessmen (but it is thought that these were spoofed), after which it took a convoluted path through casinos and its path has been lost. The Sri Lanka one, though, failed, and a $20 million transfer was stopped due to a typo in the message (using “fandation” rather than “foundation” for the Sri Lankan organisation involved).
The weak point seems to be related to the IT equipment used in the Bangladesh Bank, which included second-hand network switches and where the Swift servers were not isolated from the external network by a firewall. The malware was used to search for Swift messages and extract addresses and transfer references. It is likely they then spoofed their authentication onto the Swift network and generated valid transfer messages, along with disabling the print-outs of the transactions to the printer in the bank.
Ripple
Ripple, created in 2012 by Chris Larsen and Jed McCaleb, has increased its value to around $13.2 billion.
But is it different from Bitcoin — which is a cryptocurrency — as Ripple (XRP) can also be traded as tokens. These tokens are pre-mined, so there is no need for a mining network. With an XRP token, the value is directly mapped to traditional currencies. Overall it can act as both a cryptocurrency and also as a payment network for transactions.
Currently, it has the third highest market capitalisation of the cryptocurrencies:

Currently, banks solve the problem of transferring money between countries with the SWIFT network, and which is often slow in its operation. Ripple, though, uses a publicly sourced consensus ledger with a distributed infrastructure of trusted gateways. This infrastructure is managed by Ripple Labs. Ripple then aims to complete a currency transaction in seconds, using tokens for transaction fees. These tokens can then be converted back into currency through a cryptocurrency exchange.
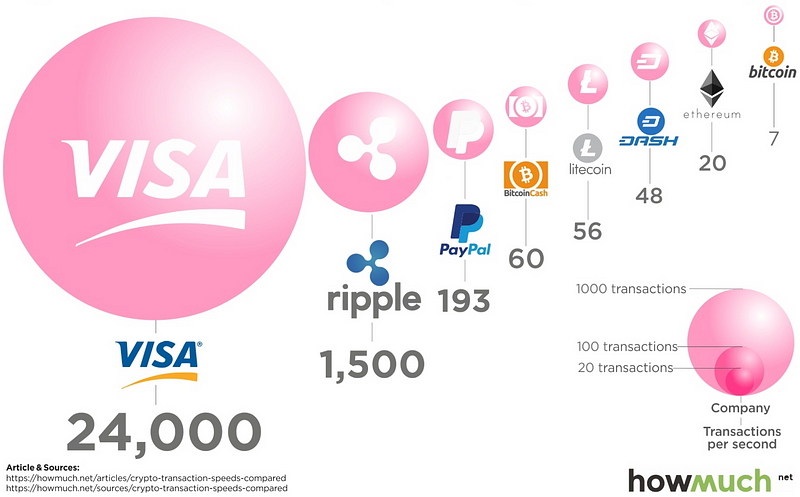
So while Ethereum and Bitcoin struggle to scale, and are hitting bottlenecks with the number of transactions that they can support per second. Bitcoin is especially is slow and can take over 10 minutes to create a consensus, and also requires a great deal of energy to create it. Ripple’s fast consensus — in less than a minute — can thus be used to quickly transfer funds and compete against Paypal and Visa:
Let’s say that Bob wants to send $100 to Alice and who is in a different city. He gives the money to his local agent (Trent) with a password that Alice is required to provide [A]. Trent then contacts Alice’s agent (Peggy) and gives Peggy the money with the password [B]. If Alice then gives Peggy the right password [C], Peggy will then provide Alice with $100 from her account [D]. Now Trent will create an IOU for Peggy for $100, which can be paid at a given time, or used within other transactions.

The trust network created is between Bob and Trent, Trent and Peggy, and Peggy and Alice. These trust elements are created as a Gateway for the chain. Anyone can then register to act as a gateway and thus act as the middleman for the exchanges.
Each currency uses its own gateway such as CADBluzelle (Canadian dollars — CAD), BTCbitstamp (BTC), and USDsnapswap (US $), and multiple gateways can be involved in order to translate the required currencies. This interconnection of gateways creates a “ripple” effect for the transaction.
Balances are thus held at the gateway, and where there could be the risk of a gateway not honouring payments. Users will thus only communicate with gateways which they trust, and which are credit-worthy. In this way, the user will not be exposed to the risk of a transaction hack, as the trustworthy gateway will, hopefully, honour the transaction.
The Ripple network thus does not need a proof-of-work system such as Bitcoin, and the transactions can be cleared within a few seconds. The consensus is then created by validating account balances and transactions by the gateways within the system. This improves on the double-spending method that Bitcoin uses.
So if Eve creates a transaction of $100 and sends them to multiple gateways, all the gateways will then vote on the transaction, and all, but the first, transaction will be deleted (and where the voting system takes five seconds to achieve a majority vote). As there is no central control, the verification of the transaction is distributed.
Each transaction is recorded as an IOU on the public blockchain for the currency used for a user or gateway. These transactions are not linked to an ID, and are pseudo-anonymised (but with complex analysis could be traced to individuals). Unlike the Bitcoin network, the Ripple network scales well and can handle millions of transactions at a time, and where each transaction carries a fee of 0.00001 XRP (which is significantly smaller than the SWIFT network).
Adoption of Ripple
Many banks including UBS, RBS, Merrill Lynch, Santander, BBVA, UniCredit, and Standard Chartered have adopted the Ripple Network and are actively using it to transfer transaction fees. With its growth in popularity, the largest cryptocurrency exchange in the US — Coinbase — is likely to add it to its currency portfolio of bitcoin (BTC), ethereum (ETH), and litecoin (ŁTC) trading. This will make it easier for users to purchase them. The exchanges where XRP is currently traded are:
- CEX.IO — This is a UK-based exchange.
- GMOCoin — This is a Japan-based exchange.
- Huobi.pro — This is a Singapore-based exchange.
The limit applied for ripple is $100 billion. With every payment a small amount of ripple is intentionally lost, and which reduces the total supply over time. This act as an inflationary control and reduces its supply over time. In order to address worries about the supply of XRP, Ripple Labs have placed 55 billion XRP in escrow. This includes 55 contracts of one billion XRP tokens and which will release one billion XRP tokens into the market each month. This provides for a well-defined release of the tokens.
The Ripple network can handle up to 1,000 transactions per second, which is the throughput that Visa handles. Presently, Ethereum can only cope with 15 transactions per second, and where Bitcoin only supports up to six transactions per second.
Risks of Ripple?
As with many cryptocurrencies, there are associated risks. In 2015, Peter Todd analysed Ripple and found a number of potential attacks, and rated them in terms of cost, scope, duration, and probability:
- Consensus Split. This uses different versions of the protocol to confuse the network, and where it is unable to create a consensus.
- Transaction Flood. This is where a large number of transactions are generated, and the network is unable to process the valid ones within a given time constraint.
- Coercion of Validators. This is an attack on specific nodes, in order for them to fail to process their transactions.
- Software Backdoor. This is where a trusted user adds a backdoor in the software distribution.
- Theft of Validator Secret Keys. This is where the secret keys for the infrastructure are leaked.
- Simulated Ledger. This is where nodes can simulate the required signature and create a fake ledger.
The major finding was that the end result of applying Ripple would not be that much different from the current centralised approach, and that if more than 20% of Ripple’s network nodes did not agree, there would be a fork in the ledger. At the present time XRP doesn’t actually have to be used, and can be seen as a “settlement currency”, but most of the coins are currently controlled by Ripple.
Conclusions
The current risks around the SWIFT network puts our financial stability at risk. We now are faced with serious risks to our financial infrastructure, and something needs to change soon, otherwise we risk large-scale damage to the financial infrastructure of countries (and possibly to the world). In a matter of an hour, hackers can make 10s of millions of dollars.
There are few other crimes which can net this much money for so little opportunity of being caught. We need a better financial transaction infrastructure, and one where cryptography is applied in the correct way.
If we continue with the SWIFT/ATM infrastructure in its current state, we risk a massive compromise and a possible collapse of trust, with major banks collapsing. The move to integrate with a more trustworthy infrastructure, especially in using cryptography properly and in creating a Merkle Tree.
Like it or not, the distributed ledgers, Merkle Tree and consensus methods are the way that our finance infrastructure should have been created, and will in the future. You might call it blockchain, but at its core is the Merkle Tree and digital signing, with some form of trusted consensus.