Do You Think You Can Analyse Ransomware?
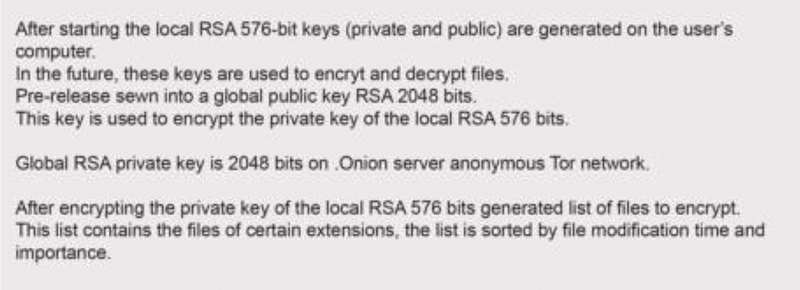
Do You Think You Can Analyse Ransomware?
Ransomware is one of the most popular methods that a cybercriminal can use, and often has a high success rate in gaining financial reward:
Here are the slides:
And a recording of Ceber doing it thing:
So, I have created an evidence bag for the Cerber ransomware. You can view it [here] or download it with this [ZIP].
Look in reports\report.html, and answer the following:
- Outline the traces of evidence that Cuckoo generates.
- Can you identify the message that the user receives after they have infected?
- Can you outline one link that has been created for the personal page for the user? What can you identify from these links?
- Cerber contacts a range of addresses using UDP and passes data. By analysing dump.pcap, which IP addresses does Cerber access for UDP connections and which UDP port is used for the connection?
- Which file extensions are read by the ransomware program?
- Which is the likely file which contains the executable ransomware program?
- The malware changes the registry key for HKLM\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zonemap to which value?
- Why do you think that the registry key for HKEY_CURRENT_USER\Software\Microsoft\Speech\Voices\ has been changed?