Just Another Patch Tuesday? NCSC Stops Another WannaCry, Adobe Hits 83, and WhatsApp Hits Zero
Just Another Patch Tuesday? NCSC Stops Another WannaCry, Adobe Hits 83, and WhatsApp Hits Zero
Well. It has been a busy week for CVEs. First we we had the WhatsApp Zero day (CVE-2019–3568) and then CVE-2019–0708 (Remote Desktop Services Remote Code Execution Vulnerability). Adobe’s Patch Tuesday included patches for Flash and Acrobat/Reader (83 vulnerabilities):

For Microsoft, Patch Tuesday included the RDP patch within its 79 vulnerabilities, of which 22 were defined as critical. This mainly included critical patches for cripting engines and browsers (18), and also for remote code execution (RCE) in Remote Desktop, DHCP Server, GDI+, and Word.
CVE-2019–0708
The RDP vulnerability allows an attacker to craft an RDP request and gain privileged access to a machine. The vulnerability was found by National Cyber Security Centre (NCSC), and which identified that a worm — could be spread using RDP. It affects systems such as Windows 7, Windows Server 2008 R2, and Windows Server 2008. If exploited this could cause another WannaCry-type infection. One of the most impressive things here is that the NCSC is open about the zero-day vulnerabilty, and is not saving it as a “state secret”. GCHQ’s position is:
“Our default is to tell the vendor and have them fix it. But sometimes… we decide to keep the fact of the vulnerability secret and develop intelligence capabilities with it.”
At present there is no weaponization of the vulnerability, but this often follows soon after a disclosure, so that companies are advised to patch their systems immediate, and possibly switch off TCP port 3369 on the external firewall, until systems have been patched.
For CVE-2019–0708 … PATCH NOW!!!!
CVE-2019–3568
What if someone analysed your phone?
They would find out all your contacts, all of your friends and enemies, all of your calls, all of your locations, all of your browser history, … in fact, virtually everything about you!
And what if they then controlled your phone?
They could pretend to be you, they could send messages from you, they could listen in on your conversations, they could send emails from you, they could read your text messages and even delete them, they could reset all your passwords without you knowing about it … they would know and control virtually everything in your life.
If WannaCry was a wake-up call to the world, then a new vulnerability in WhatsApp shows how we could all be held to ransom from malicious agents — and where you clicking on an SMS link could compromise your device. But what it you didn’t have to click on a link, and the “back-door” into your phone just happened without you doing anything? For this Facebook have announced that they have just patched a major vulnerability in WhatsApp, and which had been exploited by “an advanced cyber actor” to target various users of its application.
The attack is thought to have used software created by the NSO Group — an Israeli security company — and involves calling a number on WhatsApp on either Apple iOS or Android, and automatically installing surveillance software [ref]. The installation of the malicious software does not even show up in call records. Initial signs are that the software performs a buffer overflow in memory and then allows some remote code (SRTCP — Security Remote Transfer Control Protocol) to run on the device. This then installed the NSO Group sourced Pegasus RAT (Remote Access Trojan) software to spy on the user:

The vulnerability was discovered when his phone was investigated when a London-based lawyer suspected that his phone had been hacked, and took it for investigation to the Citizen Lab at the Munk School of Global Affairs at the University of Toronto [link]. The lawyer is thought to have lawsuits against the NSO Group [ref].
The existence of the Pegasus software — thought to have been created by the NSO Group — was discovered by Ahmed Mansoor — a UAE human rights activist — and where he found he was targeted through SMS messages, and for him to click on malicious links. He sent these to Citizen Lab for investigation, and who discovered that the links would have installed the malware onto his device. This software has used zero-day methods in iOS, in order to gain access to the device. The Android version — also know as Chrysaor — does not rely on zero-day exploits to gain access to a device.
The iOS version typically the zero-day vulnerabilities to jailbreak the device, where as Android version of Pegasus uses the rooting method of Framaroot. With iOS, install fails if it does not manage to jailbreak the device, while the Android version is still usable without a root install.
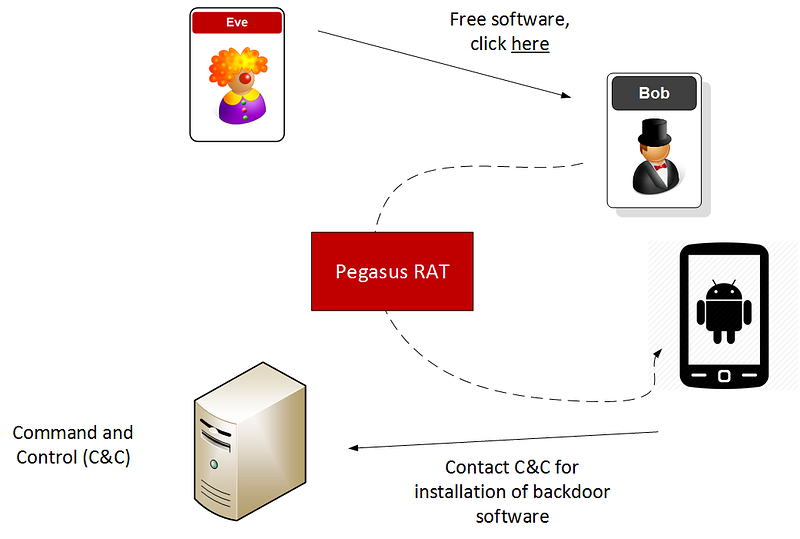
A typical method of tricking the user (Bob) into installing the backdoor, is for Eve to send Bob (the target) an SMS message. When he clicks on the link, it installs the Pegasus RAT, and which then calls up the C&C server for the full installation of the required software components and for control commands:
Once installed Pegasus becomes a RAT and can spy on keystrokes, voice calls, contact lists, browser history, and virtually everything on the device. The usage of encryption is overcome, as all the messages and calls are unencrypted. Pegasus also takes extensive steps to hide itself and will automatically self destruct after 60 days if it cannot detect its command-and-control (C&C) server, and the SIM card does not match the expected SIM card ID. These stop the software from spreading onto non-targeted users.
The affected versions are Android prior to v2.19.134, WhatsApp Business for Android prior to v2.19.44, WhatsApp for iOS prior to v2.19.51, WhatsApp Business for iOS prior to v2.19.51, WhatsApp for Windows Phone prior to v2.18.348 [here].

It looks like most users would have gained the updated version. Here is my Android version of WhatsApp, and showing Version 2.19.134:

If you are interested, here’s “The Art of the Backdoor” …
Do you ever worry that your locksmith may take a copy of your key when they fit a new lock? Or that your locksmith has…medium.com
Conclusions
Three bits of advice … 1. patch, 2. patch some more, 3. patch.
Basically … we have created systems and software which cannot be trusted, and we need to move to a more trusted world of software.