In 1991, Phil Showed Us the Right Way To Send Mail … In 2019, We Are Still Stuck in the 1980s with…

In 1991, Phil Showed Us the Right Way To Send Mail … In 2019, We Are Still Stuck in the 1980s with Email
In 40 years, email is still the weakest link in security … so how can we stop email snooping?
In June, 1991, Philip Zimmermann created the first release of PGP (v1.0) [here]:

In a GDPR era, Phil could see the future clearly:
PGP empowers people to take their privacy into their own hands. There has been a growing social need for it. That’s why I wrote it.
Phil Zimmerman was one of the first to face up to defence agencies with his PGP software, which, when published in 1991, allowed users to send encrypted and authenticated emails. For this the United States Customs Service filed a criminal investigation for a violation in the Arms Export Control Act, and where cryptographic software was seen as a munition. Eventually the charges were dropped.
Why doesn’t the community push for better standards? Well, could it be that the status quo is a comfortable place to be for many corporations, and where they can snoop on their employees emails?
Hal Finney — sadly departed — was also the second developer hired for the PGP Corporation, after Phil Zimmerman, and he is quoted that he loved the technology as it protected the rights of individuals to privacy. He remained there until his retirement in 2011.
Hal was completely enchanted by the magic of cryptography and his Web page announced:
Much of my free time and effort these days are devoted to my activities in cryptography. In the past, I have participated actively on the Cypherpunks mailing list. Cypherpunks Archives seem to go down suspiciously often; too much “burn before reading” stuff there, I guess.
and for PGP:
I was one of the original programmers on PGP version 2.0, working directly with Philip Zimmermann, author of the program. Today, I work for Network Associates, developing the crypto library for the commercial version of PGP.
In 2007 it took a step towards a standard as RFC 4880 [here] — note Hal Finney’s name on the list of authors:

PGP
Within 40 years, email has not changed much. Basically, its still the same as it was when it was created, and all we have done is add a tunnel for the sending and the reception of the email message. There is little in the way of checking of the sender of an email, and it is normally in a plaintext format on our email servers. This leaves email open to both phishing, and where scanning systems must try and interpret the body of the email to determine if it is malicious.
Insiders, too, can often view (and change) email messages. PGP, though, should have replaced our email systems, as it provides both the encryption of the message (using the public key of the recipient) and also includes the signature of the sender (using their private key to sign and their public key to prove their signature).

But PGP has failed to take on because of the complexity in dealing with encryption keys — along with Microsoft failing to adopt trusted email within their Exchange product. So while the usage of PGP normally involves the integration of a keyring to store the keys for recipients, we can actually simplify it by just using the symmetric key option. With this we just take a password, and then generate an AES key. This is used to encrypt the message and then covert it into an Amor format (and which can be sent in the body of an email). When received, the recipient just uses the same password to generate the same key, and then decrypt the message.
So let’s send a message of “So did NSA put a backdoor?” and we will apply a password of “qwerty” with 256-bit AES. With PGP we can encode to an armor file format, and which can be easily integrated into an email message:
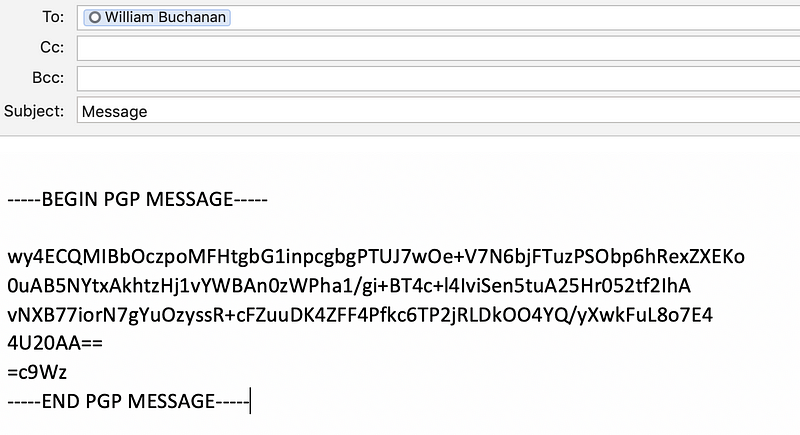
We can also use GPG to generate the cipher message for the email. First we create the message:
> type 1.txt
So did NSA put a backdoor?
Next we create an amor file with the encrypted message:
> gpg -c -a 1.txt
We can then list the encrypted file:
> type 1.txt.asc
-----BEGIN PGP MESSAGE-----
Version: GnuPG v2
jA0EBwMCz1yj3ME13Nae0lQBp7yb3F1PpsC6J0Qe/3UXsh0P4HIxKzslPdXROGrh
VtpKmtVUiLhEFFpHzdgEaFwCLBM/EP86dN7YVJBztoP/trM+Ib5j4buNv+EdGCra
X5YPeJc=
=BAb2
-----END PGP MESSAGE-----
This is the message that is pasted into the email. Finally we decrypt with the given password:
> pgp -d 1.txt.asc
So did NSA put a backdoor?
PGP encryption with Go
So how can we send and receive secure email, without the complexity of public keys? Well, PGP has a symmetric encryption mode, and where we can use a symmetric key to encrypt and decrypt the message [example]:
package main
import (
"bytes"
"errors"
"fmt"
"io/ioutil"
"os"
"golang.org/x/crypto/openpgp"
"golang.org/x/crypto/openpgp/armor"
"golang.org/x/crypto/openpgp/packet"
)
func main() {s:="hello world"
p:="hello world"
s = string(os.Args[1])
p = string(os.Args[2])
plaintext := []byte(s)
password := []byte(p)
packetConfig := &packet.Config{
DefaultCipher: packet.CipherAES256,
}encrypted, _ := Encrypt(plaintext, password, packetConfig)
fmt.Println("Message: ", s)
fmt.Println("Password: ", p) fmt.Println("\nEncrypted:\n\n", string(encrypted))decrypted, _ := Decrypt(encrypted, password, packetConfig)
fmt.Println("\n\nDecrypted:", string(decrypted))
}
func Encrypt(plaintext []byte, password []byte, packetConfig *packet.Config) (ciphertext []byte, err error) {encbuf := bytes.NewBuffer(nil)
w, _ := armor.Encode(encbuf, "PGP MESSAGE", nil)
pt, _ := openpgp.SymmetricallyEncrypt(w, password, nil, packetConfig)
_, err = pt.Write(plaintext)
if err != nil {
return
}
pt.Close()
w.Close()
ciphertext = encbuf.Bytes()
return
}
func Decrypt(ciphertext []byte, password []byte, packetConfig *packet.Config) (plaintext []byte, err error) {
decbuf := bytes.NewBuffer(ciphertext)armorBlock, _ := armor.Decode(decbuf)
failed := false
prompt := func(keys []openpgp.Key, symmetric bool) ([]byte, error) {
if failed {
return nil, errors.New("decryption failed")
}
failed = true
return password, nil
}
md, err := openpgp.ReadMessage(armorBlock.Body, nil, prompt, packetConfig)
if err != nil {
return
}
plaintext, err = ioutil.ReadAll(md.UnverifiedBody)
if err != nil {
return
}
return
}
A sample run is:
-----BEGIN PGP MESSAGE-----
wy4ECQMI702U/65IOE9gpkJvs7+uwZDJxWFcECcTu6/oBNBaBw4SuEW5mzx9Cxgu
0uAB5CeF3hCjroJ/9H719YeLxsjhbSPg3+Dv4TQl4ILiSsWvW+DE4uLOm3LgueCx
4NrkeW0yaNQw/tobiT6PnsCTEOIiZnJ74bH1AA==
=czPe
-----END PGP MESSAGE-----
Decrypted: hello
If we save the PGP message to a file name 1.asc, and then run “gpg -d 1.asc”, we can enter the password and read the message.
Conclusions
While the risks to our society are great, there is, possibly, an even greater risk to our citizens for their privacy. If you ask Phil Zimmerman (creator of PGP), he thinks that law enforcement agencies have never had it so good and that the step to breaking encryption would just be one step too far. So in a world when I can’t even tell if the person who has just send me an email is that person, if anything, we need to move towards building a completely trusted infrastructure built on cryptography.