Towards The Cognitive Engine in Cybersecurity
Towards The Cognitive Engine in Cybersecurity
As you may know we are working on a Data Science and Cybersecurity course, and which is part funded by The Data Labs, and it will contain a whole lot of things on SIEM, machine learning and AI. Here we probe the nature of the brain and how we could create a cognitive engine in Cybersecurity. While you can perhaps get a machine to drive a car, the complexity of cybersecurity is a whole lot different thing.
Our wonderful brain
As humans we learn, and often have to learn to perform a task to a high degree of accuracy — such as for handwriting, or driving a car. This type of activity requires very little in the way of us recalling facts and events from the past. It would obviously be dangerous if we approached a traffic light, and had to recall a time in the past when we drove through a red light and caused a serious accident. Once we learn that we should stop at red light, our brain will automatically drive our motor responses. Without a thought we pick up the colour of the traffic and where green tells us to go, while a red light causes us to apply our foot to be brake. But, if a traffic policeman is at the junction and is waving us on, we might recall some of our memories of this type of event from the past, and decide that we do not have to slow down and overrule our automatic response.
Unfortunately, in cybersecurity, we are a long way off machines performing this type of operation. For this, the whole of the information infrastructure within an organisation would have to act as a complete entity, and where decisions were made based on well-defined rules (as defined by an expert system or a procedural approach), but where data could be quickly recalled and processed, and which could overrule previously defined rules. It would then be possible to update a predefined rule based on new evidence, and whereas improved rule could be put in its place.

With this we could define a base line — or starting point — level if security, and where the infrastructure would then evolve from this starting state. This would allow the information infrastructure to change itself over time, and create fast-acting rules which evolved to new threats. For example, we might define a rule that generally blocks SSH accesses on our Cloud infrastructure through a firewall rule, but allow access from an administrative account and on a predefined IP address. But our system could recall information that the trusted administrator also logs in from another IP address, and where cognitive system could then overrule the blocking of the accesses from the new IP address, based on events in the past.
Over time, we could thus evolve the firewall rules to enable accesses from the trusted IP address. But, then, on checking one of the accesses, there is an event which marks the specified IP address as being suspicious, and, again, the cognitive system could overrule the newly written rule. This type of process is typically seen in an Intrusion Prevention System and will work well for fairly simple types of threats, and with standard signatures (such as with malware and scripted attacks), but will often struggle with anomaly-based threats (such as for fraud and data leakage). An adversary — Eve — could thus determine the way that the cognitive engine was recalling and processing information, and could look to compromise its operation. For example, Eve could find out that the machine has learnt to trust certain source IP addresses from users who have logged-in successful over the past three months, and who have no significant alerts against them. Eve then creates a script to perform successful logins from her attack address, and then performs some simple scripted actions. The machine then will learn to trust her IP address and could give Eve’s IP address a higher level of privilege. Once granted, Eve then abuses this privilege to perform an attack on the system.
Being adaptive, iterative, stateful and contextual
Within cybersecurity, unfortunately, we are increasingly swamped with alerts from systems, and to cope with this we possibly need a more cognitive approach in analysing alerts, and one which matches the operation of the human brain (but can perform its actions so much faster). This type of approach will general aid decision-making, and not rely on humans making judgments on fairly trivial things. A cognitive engine would thus be able to be:
- Adaptive. This would allow the machine to learn from changes as new goals and requirements evolve. The engine, too, could also cope with unpredictability and ambiguity, and make reasoned decisions. This adaptability would allow pre-defined rules to be changed and migrated over time, and would also support the strengthening of security when there is a perceived attack, and to reduce it when not under attack.
Interactive. This would support the interaction of the cognitive engine with a whole range of services, people, systems, and so on. A core part of a cognitive engine — as we see in the brain — is the ability for it to take inputs from a range of sources, and then provide outputs in the required way. - Iterative and stateful. This involves understanding previous interactions and be able to sustain future ones, along with plotting the best course and to learn new routes. As humans our interactions with others are often stateful, and we remember where we have left things with different people. Within a cognitive engine we would thus define our interactions as well-defined states, of which we move into and out of. The probabilities of these moves between states is often a key factor in defining system anomalies. For example, it we have received a TCP SYN flag for a connection, and sent back a data segment with the TCP SYN and ACK flags sets, then we will wait in the state to receive a TCP ACK flag from the host. If we receive another TCP ACK flag on the on the same TCP ports, we can see this as an unlikely state, and flag as an anomaly.
- Contextual. This allows the identification of key contextual elements within the data, including locations, names, dates, and so on. The original data may be in many different formats, and could be structured, semi-structured or unstructured.
Our Brain’s Memory
Our brain is basically a network of neurons and which listen for electrical and chemical signals from other neurons. These then fire their own signal when there is are enough of a signal from the neurons they connect to, and where they can then influence other neurons. This network then takes inputs from our senses and create outputs to our muscles. Within a network of 10,000 neurons, we could have around 100 million connections, and each of these connections could be used to process key elements of inputs, and drive outputs. This interconnected network creates learning, memory, thought, and emotion.
Within our brain we have a short-term memory and a longer-term memory. The long-term memory stores either implicit or explicit memory. With implicit memory we have unconscious — or muscle memory. For explicit memory we have episodic memories (events that have happened) and semantic (the storage of facts). A cybersecurity firewall system could be seen as implicit and explicit rules with its memory. For implicit rules (or implied rules) the firewall runs rules which cannot be viewed, whereas explicit rules are generated by the user. Whenever a stateful firewall accepts a new connection, it then keeps track of the connection, and will open up the firewall in the other direction. For example, if an FTP connection from the outside network is allowed to pass into the DMZ, the firewall will open-up the connection from the DMZ to the outside network (with a reverse of the TCP ports).
The three core areas of the human brain which are responsible for the processing and consolidation of memory are:
- Cerebellum. This plays a core role within the learning of procedural memory. These are the skills that are practiced or are routine and then learnt with a high degree of detail.
- Hippocampus: This area provides the consolidation of both our short-term and long-term memories. The explicit memories are conscious and the hippocampus has a core function of writing the data to memory. For the long-term memory, this typically happens when we sleep.
- Amygdala. This plays a key role in emotions and is thought to be responsible for the recall of information around emotionally-charged events. Most of us can thus remember important times of the past, and which we can play back. Our first day at school, or the time that we learnt to ride a bike, often come rushing back to us, but where we might struggle to name some of the capital cities of the world. Along with this, the cerebellum seems to play a key role within creativity and innovation.
Any damage to the hippocampus can cause serious memory loss problems, and lead to an inability to create new memories, or fully consolidate older memories. The storage of facts and events is known as conscious or explicit memory. It is not an automatic process to store event information within our long-term memory, but sensory details of the event are consolidated into memory over time. Once consolidated in memory — and where the event can be stored for a lifetime — the hippocampus does not seem to play a key role in the retention of it in memory. Clinical studies have shown that the removal of the hippocampus has led to the loss of the ability to create memories (declarative memory), but where new skills can still be learnt (as this requires non-declarative memory). Along with this, it is thought that damage to the hippocampus might not affect memory retention after the consolidation process.
For all the inputs, our brain develops rules for the required connection, and where the connections are learnt over time, and then re-enforced. For example, it can take a while child to learn what a “cat” is, as their brain needs to analyse the form of a cat and make the required connections. A core of element of this intelligence is thus the ability to store connections and make linkages between things. This involves storing things within short-term memory, and which are then processed and passed onto our long-term storage — the consolidation process. Encoding is thus used to convert information into something that can be stored in the brain. For human intelligence the speed of access to this data and its processing is thus an important element for us as humans, as the failure for us to respond to a stimulus could result in a dangerous situation.
Within focused tasks, such as the detection of malware, we can either write an algorithm to detect its behaviour or could define a signature pattern that will identify it. We could also create a neural network and train for the required connections for simple tasks. Unfortunately, we are a long way off creating a machine which matches the core intelligence of the human brain. Thus we often simplify things by storing pre-processed information — such as alerts and feed these into a centralised system which creates the required linkages.
Machines and Data
For a machine, the core of intelligence is the access to data, and where they can derive the required information, or where it is used to learn the required connections. Within all our actions we must define whether we need to make a decision based within real-time or non-real-time. Within a Distributed Denial-of-Service (DDoS) attack we must cope with the incoming data and respond to the threat with our defence mechanisms — an active defence. To respond we must then identify the network traffic which is the source of the attack, and undertake the best form of defence, without affecting the quality of the service for other users. This might involve reconfiguring a firewall with a blacklist of IP addresses, or to spin-up more resources in order to cope with the increased amounts of network traffic, or even to apply a quality of service on the network traffic, so that good traffic is given priority over bad traffic.
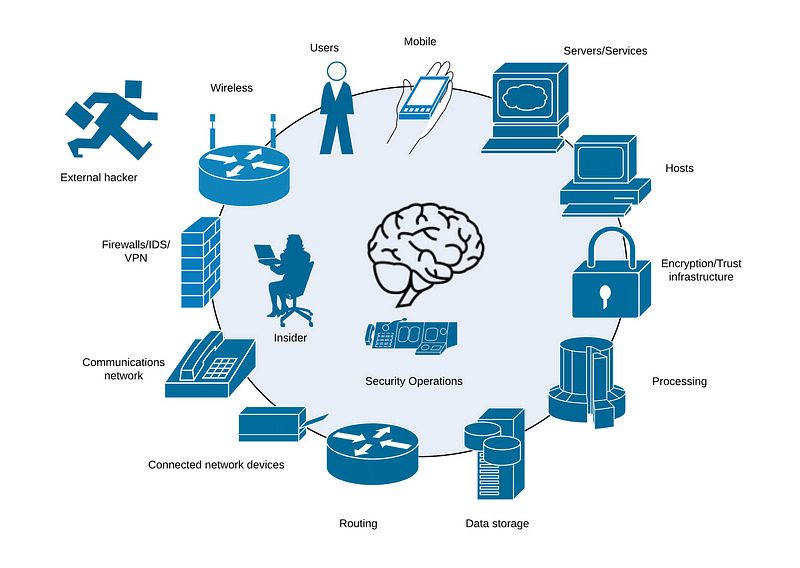
Within an organisation we typically deal with semi-structured data, and where we gather from logs from multiple places on the network, such as from hosts, firewalls, IDSs, Active Directory servers, and so on. Each of the hosts will typically be setup with a data gathering agent and then configured to pick up the required events. The greater the number of events defined, the larger the amount of data that needs to be gathered. We thus define the events that are required for threat analysis, and then aggregate these into a single data source (Figure 2). The data is then normalised and parsed and stored in a more structured form, and which can be processed for the identification of standard signatures of attacks, or mined for key search terms. At this stage we might reduce the alerts generated from millions into just a few significant ones.
We then have to design the system so that we gather enough data events that will give us the required information to cover our threats. Obviously the more we gather, the more data we will have to use within investigations. But, too much data could be expensive both in the costs for data gathering licences, and also in processing/data storage overheads. Each of the systems, too, have a finite amount of space to store logs, thus some of the devices might roll-over their logs once their memory is full, thus we must make sure we gather the data within defined time limits. For many systems, the core of this is a Syslog server, and which is a central place on the network where each of the devices send their data to. The SIEM infrastructure then just has to gather the data from the Syslog servers, and not go and poll each of the devices.

Conclusions
The human brain is the most wonderful thing on the planet. It is responsible for such acts of kindness and beauty, but it is also responsible for evil and badness. Look after your brain, and exercise it every day … go learn something new. Education is your brain’s food, and go and feed it!
If you are interested, here’s my recent “fun” talk on AI and Cybersecurity: