Splunking Your Password — Is Splunk Safe for Passwords?

Splunking Your Password — Is Splunk Safe for Its Own Passwords?
We often use tools to assess the security of other systems, but what about the tool itself? Who watches that? And how secure is it? So one of the most popular tools in Security Operations Centres is Splunk. Let’s have a look at how it stores passwords.
Splunk is a great tool. Under the hood it actually operates like a Linux type environment (even on a Windows OS). Each of the user logins and passwords are then stored in the passwd file in the /etc folder (within the Splunk home folder). And so I was having a look, and found that the following is created for a user named “csn01”:
:csn01:$6$Uk8SVGLsBuSmD75R$Lhp5yjwRUAM.LbH5IIthZ1u0bAUdJwBvvccBshAvpFPiRn62EYeiKOaP8xh97aV4UaNfVykRZhUy/3ZOZd1oc.:::user::::18161
So what is the method used for hashing the password. Well, we split the hashed password into three main groups (seperated by the “$” symbol):
6
Uk8SVGLsBuSmD75R
Lhp5yjwRUAM.LbH5IIthZ1u0bAUdJwBvvccBshAvpFPiRn62EYeiKOaP8xh97aV4UaNfVykRZhUy/3ZOZd1oc.
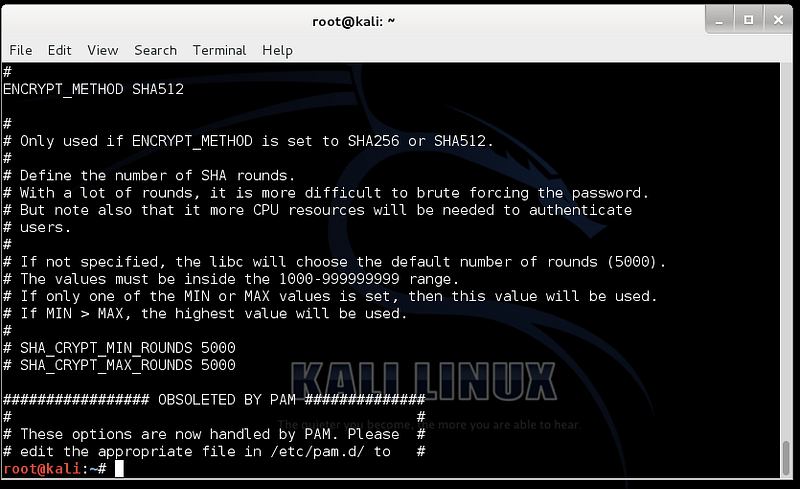
and where “6” is the hashing method (SHA-512), “Uk8SVGLsBuSmD75R” is the salt value, and “Lhp5yjwRUA..d1oc.” is the hashed version. When the user logs into Splunk, their password will be added to the salt value, and the same hashed version should be created. Well, the “$6” part identifies that it is SHA-512, but when I try to hash with SHA-512, it gives the wrong hashed value. The answer lies in slowing the hashing process down by performing a number of rounds. For this 5000 rounds works to give the right result, and so here is the Python code [here]:
import hashlib;
import passlib.hash;
import base64;
import sys;
password="qwerty123"
salt="Uk8SVGLsBuSmD75R"
# csn01:$6$Uk8SVGLsBuSmD75R$ Lhp5yjwRUAM.LbH5IIth
user="fred"
if (len(sys.argv)>1):
user=str(sys.argv[1])
if (len(sys.argv)>2):
password=str(sys.argv[2])
if (len(sys.argv)>3):
salt=str(sys.argv[3])
h=passlib.hash.sha512_crypt.encrypt(password, salt=salt,rounds=5000)
hash=user+":"+h
print hash
A sample run [here]:
===Splunk hashed password===
User: Fred
Password: qwerty123
Salt: Uk8SVGLsBuSmD75R
===Hashed password
Fred:$6$Uk8SVGLsBuSmD75R$Lhp5yjwRUAM.LbH5IIthZ1u0bAUdJwBvvccBshAvpFPiRn62EYeiKOaP8xh97aV4UaNfVykRZhUy/3ZOZd1oc.
and this matches the Splunk entry. With hashcat, the default is also 5000 rounds:
If we now use Hashcat on the hashed version, we should be able to discover the orginal password:
root@kali:~# hashcat -m 1800 1.txt -a 0 /usr/share/wordlists/rockyou.txt
Initializing hashcat v0.49 with 1 threads and 32mb segment-size...
Added hashes from file 1.txt: 1 (1 salts)
Activating quick-digest mode for single-hash with salt
NOTE: press enter for status-screen
$6$Uk8SVGLsBuSmD75R$Lhp5yjwRUAM.LbH5IIthZ1u0bAUdJwBvvccBshAvpFPiRn62EYeiKOaP8xh97aV4UaNfVykRZhUy/3ZOZd1oc.:qwerty123
All hashes have been recovered
Input.Mode: Dict (/usr/share/wordlists/rockyou.txt)
Index.....: 1/5 (segment), 3627172 (words), 33550339 (bytes)
Recovered.: 1/1 hashes, 1/1 salts
Speed/sec.: - plains, 461 words
Progress..: 2172/3627172 (0.06%)
Running...: 00:00:00:05
Estimated.: 00:02:11:03
In this case we use the rockyou.txt list of common passwords, and where it only takes five seconds to find the password. The advantage of using SHA-512 with a number of rounds is highlighted when we run a benchmark:
root@kali:~# hashcat -b -m 1800
Initializing hashcat v0.49 with 1 threads and 32mb segment-size…
Device………..: Intel(R) Core(TM) i7–8850H CPU @ 2.60GHz
Instruction set..: x86_64
Number of threads: 1
Hash type: sha512crypt, SHA512(Unix)
Speed/sec: 454 words
root@kali:~# hashcat -b -m 0
Initializing hashcat v0.49 with 1 threads and 32mb segment-size…
Device………..: Intel(R) Core(TM) i7–8850H CPU @ 2.60GHz
Instruction set..: x86_64
Number of threads: 1
Hash type: MD5
Speed/sec: 17.33M words
In this hashcat can process 454 words per second with SHA512crypt and over 17 million per second with MD5.
Conclusions
So, Splunk uses SHA512crypt, and which is significantly slower to process than our typical hash methods. The 5,000 rounds of hashing thus slows the hash cracking from millions of passwords processed per second, to just a few hundred. If an intruder has a GPU, though, they will be able to increase speeds by many thousand, so watch those Splunk passwords.