Basically IoT Bluetooth Security is Rubbish!

Basically IoT Bluetooth Security is Rubbish!
I have quite a few presentations coming up, and I’m getting all ready to demo a few things live. And so, while we face a world of IoT, unfortunately the associated security is not quite there. One of the weakests area is Bluetooth, and so I’ve installed an Ubertooth One on a virtual machine (and on a R-PI), and getting all ready to give demos. One of my favouriate devices is the Polar H10 device:

And so I strapped it on, and ran the app, and which gave my heart rate at 68 bpm. Surely the manufacturer has kept this value secret? And so I ran:
ubertooth-btle -f -c output.pcap
and captured the output:

But, no, the Bluetooth packets were sniffed by the Ubertooth One, and where it even gave away the serial number of my device:

And then, shockingly I could interogate the heart rate value within an ADV_IND packet. The value is “2f 14 44 45”, and where the third value is my heart rate. If we convert 44 in hexademical into decimal we get 68, and which is my heart rate (Packet 598):

The data is viewed in Wireshark as:
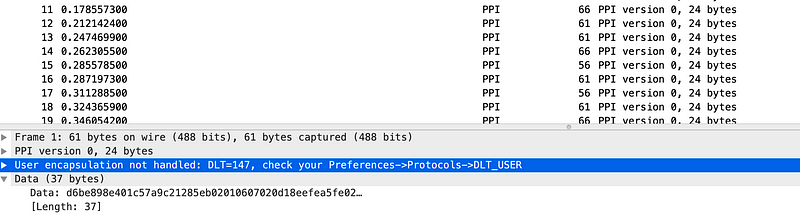
But when we set Preferences->Protocols-DLT_USER, we reveal the details of the packets:

We then get the details of the Bluetooth packets.
R-PI
The Raspberry Pi (R-PI) is a fantastic device is a perfect for a mobile pen testing setup. So I have built a Pen Testing infrastructure with the R-PI, where I can get all the tools I need, within a proper Linux infrastructure. I’ve kinda given up trying to get work arounds with Windows for my Python code, so Linux is the only solution, and Kali is the only one that makes sense for in-depth testing.
First, you download the standard image for Pi 3 (kali-2.1.2-rpi2.img.zx which, with Unarchiver, expands to kali-2.1.2-rpi2.img). On my Macbook, I then pointed my dd utility to write the SD card with Kali:
billbuchanan@MacBook-Pro-3:~$ diskutil list/dev/disk2 (internal, physical):
#: TYPE NAME SIZE IDENTIFIER
0: FDisk_partition_scheme *31.9 GB disk2
1: Windows_FAT_32 NO NAME 64.0 MB disk2s1
2: Linux 7.3 GB disk2s2billbuchanan@MacBook-Pro-3:~$ umount /dev/disk2
umount: /dev/disk2: not currently mounted
You can see we have 32GB on the disk. Then the scary bit:
dd if=kali-2.1.2-rpi2.img of=/dev/disk2 bs=1m
It takes a while to format for 32GB (10–15 minutes), but just press Ctrl-T and you’ll see where it is. In my case, I used /dev/rdisk2 (a raw disk write), which is faster for accesses. When pressing Ctrl-T you see updates on the status of the disk:
244+0 records in
243+0 records out
254803968 bytes transferred in 11.596012 secs (21973413 bytes/sec)
After this you need all the updates:
sudo apt-get update && sudo apt-get upgrade
And then you don’t want to use the HDMI output, so we install VNC server and copy-and-paste:
apt-get install tightvncserver
apt-get install autocutsel
Next it’s SSH:
apt-get install openssh-server
Second, revert to SSH defaults, which will run SSH on boot:
update-rc.d -f ssh remove
update-rc.d -f ssh defaults
cd /etc/ssh/
rm ssh_host_*
dpkg-reconfigure openssh-server
Kali and the R-PI
And then all the Kali packages:
apt-get install kali-linux-all
I booted up, and with a bit of install of Ubertooth One, and in connecting my Pineapple Wifi adapter, it all worked:


A key thing is to get SSH and VNC installed (and to have a handy USB keyboard nearby, to fix boot problems, especially the file system corrupts itself on power off). The new R-PI even has built-in Bluetooth and wifi, but when I turned to a basic pen testing app (nmap), it give me errors:
root@kali:~ nmap 192.168.0.1 -e wlan0Starting Nmap 7.40 ( https://nmap.org ) at 2017-02-19 10:47 UTC
WARNING: eth_send of ARP packet returned -1 rather than expected 42 (errno=22: Invalid argument)
WARNING: eth_send of ARP packet returned -1 rather than expected 42 (errno=22: Invalid argument)
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 0.90 seconds
The problem is that the Broadcom chip on-board the R-PI has a bug, and gives an error from the kernel. I tried so many updates for this, but gave up, so, I popped in my trusty Realtek USB device:

and scanned for it:
root@kali:~ lsusbBus 001 Device 004: ID 0bda:8176 Realtek Semiconductor Corp. RTL8188CUS 802.11n WLAN Adapter
Bus 001 Device 003: ID 0424:ec00 Standard Microsystems Corp. SMSC9512/9514 Fast Ethernet Adapter
Bus 001 Device 002: ID 0424:9514 Standard Microsystems Corp. SMC9514 Hub
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
and by magic it worked:
root@kali:~ nmap 192.168.0.1 -e wlan1Starting Nmap 7.40 ( https://nmap.org ) at 2017-02-19 10:56 UTC
Nmap scan report for myrouter.net (192.168.0.1)
Host is up (0.025s latency).
Not shown: 994 closed ports
PORT STATE SERVICE
22/tcp filtered ssh
23/tcp filtered telnet
53/tcp open domain
80/tcp open http
1900/tcp open upnp
49152/tcp open unknown
MAC Address: XX:XX:XX:XX:XX:XX Nmap done: 1 IP address (1 host up) scanned in 3.24 seconds
SSH and VNC
And it was all systems go for SSH and VNC:

And you have so much control in analysing Bluetooth packets with the Ubertooth One device:

Now if we connect the Alfa Network card:

And test with airmon-ng:
root@kali:~ airmon-ng
PHY Interface Driver Chipsetnull wlan0 ?????? Realtek Semiconductor Corp. RTL8188CUS 802.11n WLAN Adapter
phy0 wlan1 ?????? Broadcom 43430
phy1 wlan2 rt2800usb Ralink Technology, Corp. RT2870/RT3070root@kali:~ airmon-ng start wlan2Found 4 processes that could cause trouble.
If airodump-ng, aireplay-ng or airtun-ng stops working after
a short period of time, you may want to run 'airmon-ng check kill' PID Name
175 NetworkManager
363 wpa_supplicant
491 dhclient
609 dhclientPHY Interface Driver Chipsetnull wlan0 ?????? Realtek Semiconductor Corp. RTL8188CUS 802.11n WLAN Adapter
phy0 wlan1 ?????? Broadcom 43430
phy1 wlan2 rt2800usb Ralink Technology, Corp. RT2870/RT3070 (mac80211 monitor mode vif enabled for [phy1]wlan2 on [phy1]wlan2mon)
(mac80211 station mode vif disabled for [phy1]wlan2)
We can see we are now monitoring on wlan2mon, and to test:
root@kali:~ airodump-ng wlan2mon
CH 5 ][ Elapsed: 1 min ][ 2017-02-19 12:10
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
XX:FC:AF:XX:XX:XX -44 39 893 24 1 22e WPA ZZZZZ
XX:A1:XX:XX:XX:XX -49 34 0 0 11 54e WPA2 CCMP PSK ZZZZZ
XX:D3:XX:XX:XX:XX -65 46 0 0 6 54e WPA2 CCMP PSK ZZZZZ
XX:21:XX:XX:XX:XX -90 3 1 0 13 54e WPA2 CCMP PSK ZZZZZ
BSSID STATION PWR Rate Lost Frames Probe
(not associated) XX:XX:XX:XX:XX:XX -44 0 - 1 0 10 ZZZZZ
XX:XX:XX:XX:XX:XX XX:XX:XX:XX:XX:XX -1 0e- 0 0 46
XX:XX:XX:XX:XX:XX XX:XX:XX:2B:XX:XX -20 0e- 0e 0 836
We can now grab the four way handshake with:
airodump-ng -c 1 --bssid XX:FC:AF:XX:XX:XX -w psk wlan2mon
This reads for the required BSSID on Channel 1, and will create a file which begins with psk, and has a .cap extension. The output here is:
CH 1 ][ Elapsed: 18 s ][ 2017-02-19 21:38 ][ WPA handshake: XX:FC:AF:XX:XX:XX
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
XX:FC:AF:XX:XX:XX -30 0 215 3077 90 1 54e WPA2 CCMP PSK ZZZZZ
BSSID STATION PWR Rate Lost Frames Probe
XX:FC:AF:XX:XX:XX XX:XX:XX:XX:XX:XX 3 -22 0e- 1e 0 2569
Next we create a list of passwords in password.lst. We can then analyse the cap files with:
aircrack-ng -w password.lst -b XX:FC:AF:XX:XX:XX psk*.cap
This gives the results of (where some details have been removed):
Aircrack-ng 1.2 rc4 [00:00:00] 2/1 keys tested (28.31 k/s) Time left: 0 seconds 200.00% KEY FOUND! [ ------- ]
Master Key : 5C ------------------- 0C
3A ------------------- 53 Transient Key : 6A ------------------- EB
4D ------------------- 72
7A ------------------- 87
80 ------------------- 21 EAPOL HMAC : C0 ------------------- 95
And it works perfectly.
Extended the partition
The one problem, though, is that you don’t have space for the full install of Kali, so just run gparted and increase the partition (I have increased to 30GB here):

Before the partition expansion (for a 32GB SD card):
root@kali:~# df
Filesystem 1K-blocks Used Available Use% Mounted on
/dev/root 6992908 6952000 0 100% /
devtmpfs 469728 0 469728 0% /dev
tmpfs 474048 0 474048 0% /dev/shm
tmpfs 474048 12604 461444 3% /run
tmpfs 5120 0 5120 0% /run/lock
tmpfs 474048 0 474048 0% /sys/fs/cgroup
tmpfs 94808 4 94804 1% /run/user/113
tmpfs 94808 0 94808 0% /run/user/0
And after it we see the expansion:
root@kali:/# df
Filesystem 1K-blocks Used Available Use% Mounted on
/dev/root 30244272 7106868 21829232 25% /
devtmpfs 469728 0 469728 0% /dev
tmpfs 474048 0 474048 0% /dev/shm
tmpfs 474048 24500 449548 6% /run
tmpfs 5120 0 5120 0% /run/lock
tmpfs 474048 0 474048 0% /sys/fs/cgroup
tmpfs 94808 4 94804 1% /run/user/113
tmpfs 94808 0 94808 0% /run/user/0
Then we should be good to install all the tools with:
apt-get install kali-linux-full
After this we should end up with all the normal Kali tools:

Installing OpenWRT
So, what do you choose for setting up your wi-fi infrastructure? Well, it’s the best bargain that you can get on Amazon … and don’t be fooled with those wi-fi access points with bells-and-whistles … the best device to buy is a Linksys WRT56GL (the L is for Linux):
Within a few minutes with the correct firmware, it transforms itself from a device that can’t reserve IP addresses, to a full-blown Linux device:

You basically plug your R-PI into a switch port and connect the Internet connection to your local Internet router, and you have Internet access and a local network (as you’ll have many updates to install):
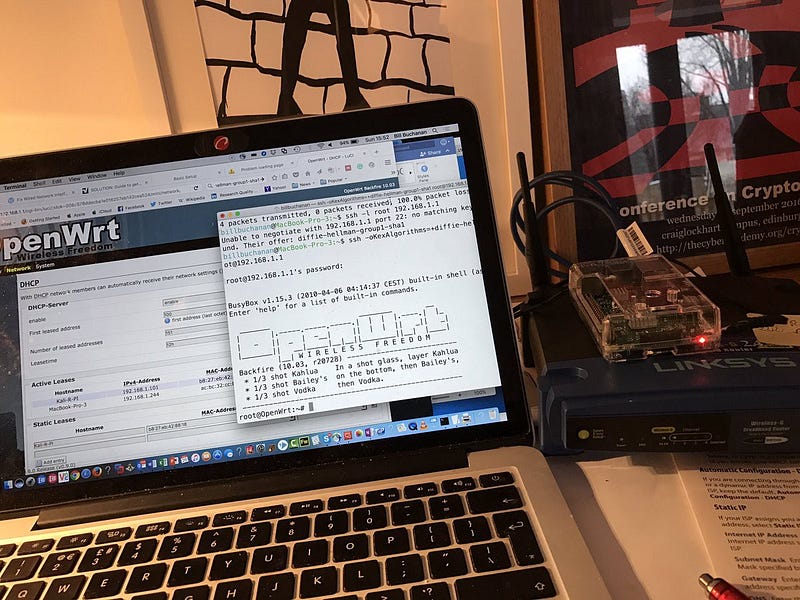
It now has full login facilities over SSH, and so many more options for its OpenWrt infrastructure. One must thank Cisco for their great work on this device. With a bit of a squeeze on the crypto method:
billbuchanan@MacBook-Pro-3:~/Downloads$ ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 [email protected]
[email protected]'s password:
BusyBox v1.15.3 (2010-04-06 04:14:37 CEST) built-in shell (ash)
Enter 'help' for a list of built-in commands. _______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
Backfire (10.03, r20728) --------------------------
* 1/3 shot Kahlua In a shot glass, layer Kahlua
* 1/3 shot Bailey's on the bottom, then Bailey's,
* 1/3 shot Vodka then Vodka.
---------------------------------------------------root@OpenWrt:~# cd /
root@OpenWrt:/# ls
bin etc mnt proc root sys usr www
dev lib overlay rom sbin tmp var
root@OpenWrt:/# ifconfig
br-lan Link encap:Ethernet HWaddr 14:91:82:6C:8B:47
inet addr:192.168.1.1 Bcast:192.168.1.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:638230 errors:0 dropped:0 overruns:0 frame:0
TX packets:1785265 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:65779030 (62.7 MiB) TX bytes:1878021757 (1.7 GiB)eth0 Link encap:Ethernet HWaddr 14:91:82:6C:8B:47
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:2328037 errors:0 dropped:0 overruns:0 frame:0
TX packets:2258657 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1945441297 (1.8 GiB) TX bytes:1769946959 (1.6 GiB)
Interrupt:4 eth0.0 Link encap:Ethernet HWaddr 14:91:82:6C:8B:47
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:527362 errors:0 dropped:0 overruns:0 frame:0
TX packets:1627185 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:31705393 (30.2 MiB) TX bytes:1682368093 (1.5 GiB)eth0.1 Link encap:Ethernet HWaddr 14:91:82:6C:8B:47
inet addr:192.168.0.33 Bcast:192.168.0.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:1800669 errors:0 dropped:0 overruns:0 frame:0
TX packets:631472 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1871830464 (1.7 GiB) TX bytes:75622109 (72.1 MiB)lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:8 errors:0 dropped:0 overruns:0 frame:0
TX packets:8 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:624 (624.0 B) TX bytes:624 (624.0 B)wl0 Link encap:Ethernet HWaddr 14:91:82:6C:8B:49
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:133504 errors:0 dropped:0 overruns:0 frame:102074
TX packets:185871 errors:44 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:40484685 (38.6 MiB) TX bytes:208829188 (199.1 MiB)
Interrupt:2 Base address:0x5000
And in a few minutes, after installing SSH on the R-PI, it’s Linux again:
billbuchanan@MacBook-Pro-3:~/Downloads$ ssh -l root 192.168.1.101
[email protected]'s password:
The programs included with the Kali GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.Kali GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Feb 27 09:08:49 2017 from 192.168.1.244root@kali:~# ls
Desktop Documents Downloads Music Pictures Public Templates Videos
GPIO
We can use the I/O interface to control a radio controller:

For this we just install the Python library:
pip install RPi.GPI
Here is some sample code for turning an electrical socket on and off:
import RPi.GPIO as GPIO
from time import sleep
import time
state=False
start=time.time()
i=1# set the pins numbering mode
GPIO.setmode(GPIO.BOARD)# Select the GPIO pins used for the encoder K0-K3 data inputs
GPIO.setup(11, GPIO.OUT)
GPIO.setup(15, GPIO.OUT)
GPIO.setup(16, GPIO.OUT)
GPIO.setup(13, GPIO.OUT)# Select the signal to select ASK/FSK
GPIO.setup(18, GPIO.OUT)
# Initialise K0-K3 inputs of the encoder to 0000
GPIO.output (11, False)
GPIO.output (15, False)
GPIO.output (16, False)
GPIO.output (13, False)
i=1
while True:
raw_input('Enter...')
if (i==1):
print "sending code 1111 socket 1 on"
GPIO.output (11, True)
GPIO.output (15, True)
GPIO.output (16, True)
GPIO.output (13, True)
time.sleep(0)
# Enable the modulator
GPIO.output (22, True)
# keep enabled for a period
time.sleep(0.5)
# Disable the modulator
GPIO.output (22, False)
else:
print "sending code 1110 socket 1 off"
else:
print "sending code 1110 socket 1 off"
GPIO.output (11, True)
GPIO.output (15, True)
GPIO.output (16, True)
GPIO.output (13,False)
time.sleep(0)
# Enable the modulator
GPIO.output (22, True)
# keep enabled for a period
time.sleep(1)
# Disable the modulator
if (i==1):
i=2
else:
i=1
continue
Demo
The following is a demo for Wi-fi testing: