“Ring” For Law Enforcement?

“Ring” For Law Enforcement?
If you have been to one of our recent presentations, you’ll find our new favouriate demonstrator: The Ring Doorbell. It is one piece of cool tech, all fitted with motion sensors and an HD camera, and with full remote alerting. But, if someone hacks your account, you may be in for trouble! This happened with the Mirai bot, and where 100s of thousands of CCTV cameras, and which took down Facebook in the US for several hours.
Send-in Law Enforcement
But, of course, the other big user of the Ring door bell could be law enforcement, as the alerts and video could be used to trace criminal activity. It has already been alleged that Ring had been sharing videos with over 600 law enforcement agencies in the US. Also, in the US, law enforcement can request up to 12 hours of video footage within one mile of a suspect area, and for up to 45 days. When you sign up to Ring you also can subscribe to the Neighours App, and receive messages such as:

For this Ring will respond to a request from law enforcement for video footage around an incident, such as:
“Car set on fire in Morningside on 4 March 2020 at 8pm. Could you send your footage to police@morningside”
To improve security, Ring has defined that the police can then only view the footage on the App, and which would require explicit permission from the user. Their new T&Cs define:
“you have always had the ability to opt out of these requests after you received your first one, Control Center now ensures that you don’t have to wait for that first request — you can easily opt out from the start.”
But many believe that this still does not address the many privacy issues involved, and a video downloaded by law enforcement could be used for many additional purposes that it was not intended for. The most extreme is that these door bells could be used as a large scale spying network for crime, such as to look out for unlicenced cars, car parking offenses, and so on. Ring, too, have been attacked for their lack of privacy, and where their application supports a range of third-party tracks, including information send to Facebook about “time zone, device model, language preferences, screen resolution, and a unique identifier”. Tests that we have done show that the Ring device is, at least, encrypting traffic from the user to the central server.
Amazon, too, has even been bragging about the data that they collect from the doorbells, and where they said that its doorbell was used 15.8 million times in Halloween. They also promoted a Halloween skin for the doorbells, and scans of kids at doorbells:
Mirai bot
The Internet was meant to be created as a completely distributed system, where data could take multiple routes to get to a service. Unfortunately, the Internet we have created is fairly centralised and where services typically have single endpoints and have choke points for traffic. In the following, Eve creates a distributed attack on a back-end Web server infrastructure, and could reduce Bob’s quality of service in creating a connection:

This means that a DDoS attack can often succeed in either bringing down the server infrastructure or exhaust the bandwidth for the traffic flows. For Bob, the Web site will either crash on him, or the quality of service will be so bad that he will leave and go elsewhere.
And so knowing that companies will lose business through website crashes and poor quality of service, we have an increasing threat from DDoS-for-hire, and where criminals can hire a tool for a given time, and define its target. Normally the way that companies deal with this is to load balance on the main gateway into their infrastructure, and then create new instances of servers. But this can be costly to implement, and can only be sustained for a relatively short time period. The upstream pipeline to the infrastructure could also become exhausted, and reduce the quality of service.
And the attack doesn’t have to focus on the back-end infrastructure. In 2016, Facebook was taken down through a botnet attack on their Dynamic DNS service — and run by Dyn.
With this, the malware infected botnet, such as from compromised CCTV cameras requested a look-up address from the Dyn servers, and which stopped other users from getting IP address look-ups for Facebook, Github, Twitter, SaneBox, Reddit, AirBnB, and Heroku. It basically worked because the cameras produced by XiongMai Technologies (XT) had a default root password of “xc3511”. The Marai malare was then used to take over an army of over 500,000 cameras. This network — a botnet — then was instructed to create false domain name lookups against the Dyn service:
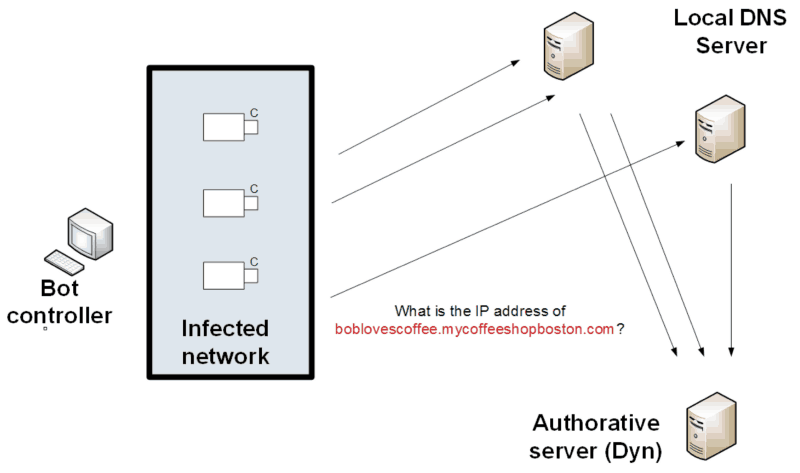
This type of attack is known as a reflection attack. One attack on the KrebsOnSecurity site resulted in a peak load of 620 Gbps. The opportunity for cybercriminals is thus to take control of the command and control (C&C) infrastructure, and instruct the botnet to create a sustained attack on a given site. The tracing of the original source of the attack is almost impossible to determine, as the attacking network is just a network of comprised devices.
In their state-of-the-internet report, Akamai reported that there has been a 16% increase from Summer 2017 and to Summer 2018, and with 7,822 mitigated DDoS attacks. The record attack at the current time is a massive 1.35Tbps. Much of the activity is still bot related, and where compromised systems can be used to perform the attacks. This can be compared with the capacity of 3.2 TBps of the TAT-14 cable which connects the US and Europe.
Conclusions
We are moving into a brave new world of surveillance, and it can be a scary one!