A Great User Experience or Security … you can have one or other?

A Great User Experience or Security … you can have one or other?
If Companies Can’t Tell The Difference Between End-to-end Encryption and TLS, We Should Be Worried!
A couple of weeks ago, I used WebEx only to present my distance learning classes, but now I sit in Zoom meetings for at least six hours per day. For me, it’s just as natural to meet someone over Zoom, as it is to travel to a meeting.
And so times are difficult, and we must come out of this period having learned a whole lot more about the weaknesses in our world. It is likely that this new world will be increasenly driven by technology, but, unfortunately, the methods we are using now are really not fit for building a more trusted and resiliant world.
Perhaps the one thing this week that highlights the smoke-and-mirrors world of technology is that Zoom carried an “end-to-end encryption” icon on their screens. But capturing a network trace from the session shows that it was using just good old (or bad old) TLS, and where the difference between end-to-end encryption and TLS is massive, as the former can be broken within a corporate infrastructure.

How did this pass any form of evaluation? Perhaps Zoom throught that they were actually using end-to-end encryption? If so, we must be worried, as Zoom certainly is the most usable video conferencing system, and makes Skype and WebEx feel like 20th Century user interfaces. I had a WebEx meeting today, and it glitched from user to user.
Along with this, the company has faced acquisition on the sharing of user data from their iOS applicaton with Facebook. Along with this “zoombombing”, allows an intruder to discover open conferences and join them.
A poor track record
Zoom, itself, was a carcrash of an application a few months ago, with one of the sloppest security designs I have ever seen. Basically, Zoom installed a Web server on your computer, and which runs on port 19421:
meuser@MacBook-Pro-3:~/Downloads$ lsof -i :19421COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
ZoomOpene 632 meuser 7u IPv4 0xae3b325b7648aa7 0t0 TCP localhost:19421 (LISTEN)
An NMAP scan didn’t pick it up:
meuser@MacBook-Pro-3:~/Downloads$ nmap 127.0.0.1Starting Nmap 6.40 ( http://nmap.org ) at 2019-07-09 11:52 BST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.0047s latency).
Not shown: 994 closed ports
PORT STATE SERVICE
88/tcp open kerberos-sec
445/tcp open microsoft-ds
548/tcp open afp
631/tcp open ipp
1023/tcp open netvenuechat
49165/tcp open unknown
But it was there and just waiting for a connection. All you had to do is just call the local Web server (localhost) with a conference ID:
http://localhost:19421/launch?action=join&confno=XXXXX
and where XXXXX is a valid conference ID. I am stunned by this. I tried it on my own machine, and found that I connected with another on-going conference:
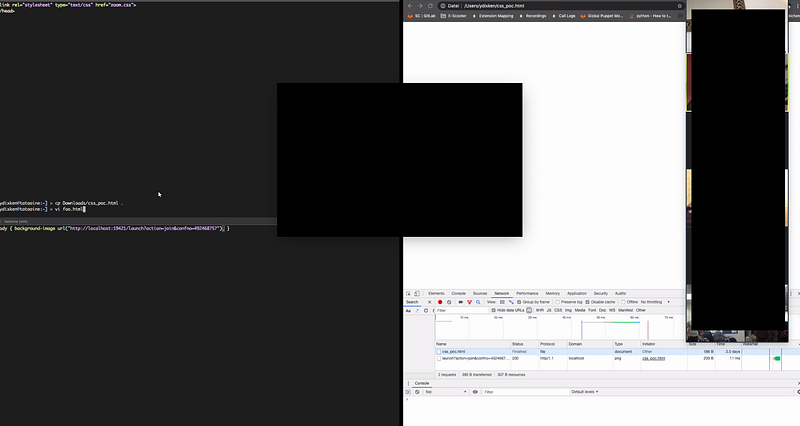
The great worry — and the major security problem — is that someone just had to install an application on your computer, or trick you into running a script on a Web page, and they have you connected to a conference call — full audio and video. And don’t think it will go away when you uninstall the software, it stays there. And in a “did they just say that” moment:

Conclusions
Our whole world has been turned upside down, and virtually everything will change in our work and social lives. I recall over the years, the continual kick-back against Skype within health care, but now it is seen to be a saviour of lives. There has also previously been resistance against technology in health care, but this is likely to change. And so if we move to an increasing use of technology, we need to build a more security, trusted and resilent data world. But, it we cannot tell the difference between an TLS tunnel and end-to-end encryption, we could be opening up our world to more data breaches, more ransomware, and more cybercrime.
Overall encryption is one of the weakest areas in the industry, and it is about time that it was used for the benefit of citizens, and not for ransomware. It must become a core part of every digital system, and created in a trustworthy way — and not as a piece of marketing. There should also not be a binary divide between security and usability, as the two should go together — it’s called “engineering”. So, whenever I see the argument of useability against security, I am reminded to this tweet:

Simplity …. over security? Why not just have one character passwords? That’s easy! Well, back to my Zoom meeting, why not join me (not!)?