The Flawed World of Contact Tracing: Where’s Carol The Tester?

The Flawed World of Contact Tracing: Where’s Carol The Tester?
Governments love quick fixes … “We have an app, and we are working with Google, so everything will be okay!”
I must admit, the specification created by Apple and Google on contact tracing is a massive disappointment, and leaves so many doors open to large scale surveillance. I appreciate that they are laying down a basic mechanism that lands on the phone, but there’s no real privacy embedded into their system, and no hints to how this could be used in the real world.
The whole discussion on user and contact tracing opens up a whole lot of questions, and the most fundamental of these is that we don’t actually have any real infrastructure to implement privacy-preserving methods. It is likely that a COVID-19 app would be a pin-point app, and where the data gathered for location and contact tracking could be easily abused, and would have limited scope outside a country’s borders. Our core problem is that we have built data infrastructures that mirror those from the 1980s, and where we care little about the core rights of the data we gather. Once captured, the owner becomes the entity who captured the data, and without the trustworthiness of the transactions involved, we leave it open to abuse for malicious activities.
The method …
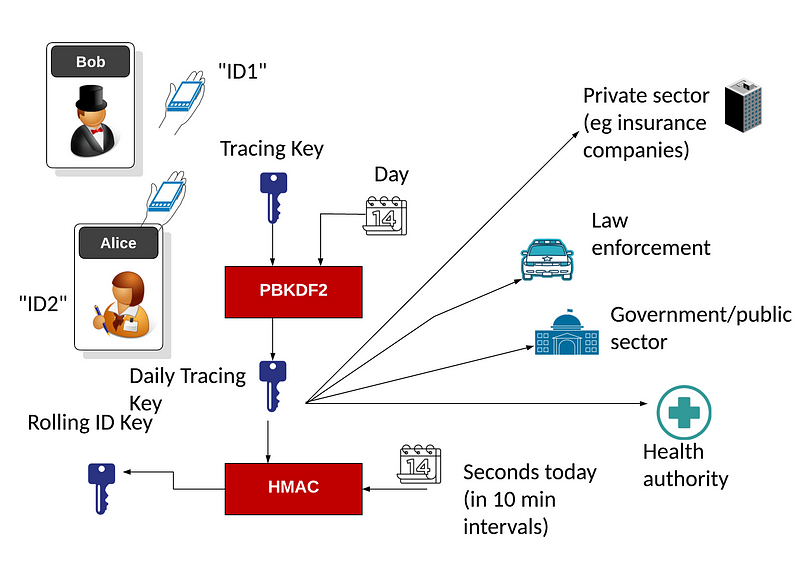
The Apple/Google method works by Alice generating a unique 256-bit tracing key for her phone — and where this key must be kept secret. Every day she then creates a daily tracing key, by creating a hash from the tracing key and the current day. From this hash, it should not be possible to determine her tracing key (as it is generated from the random 256-bit tracing key). Every 10 minutes, she then creates a rolling ID key, and which is an HMAC identifier (a signed hash) of her daily tracing key and a counter for the number of 10 mins that have passed that day.
When Bob comes into contact with Alice, he will receive her rolling ID through a Bluetooth Advertisement, and could then pass that back to Trent (the NHS). Trent cannot correlate Alice from the rolling ID, and whether she has COVID-19 or not. He is just blinding sending it back to Trent, in order for Trent to track the contact or not. In order to preserve privacy, Trent should only track if Alice has been proven to be COVID-19 positive.

Once Alice has been proven to have COVID-19, she will send the daily tracing key to Trent, and who can then match all the rolling ID keys to her identity. This will only happen for one day, and where each day she much send these keys. There is thus a key feature on the phone, and where it makes the decision to send the daily key or not. Here is an outline of the code.
And you trust governments to implement this in a trusted way?
The Flaws …
There are many flaws in COVID-19 contact tracking method proposed by Apple and Google:
- Who is Trent? We often trust our health authorities a great deal more than we trust our governments. If the data goes to clinical staff for analysis, we perhaps find that more acceptable than someone in law enforcement. Thus the fundamental question in the whole system is how we can make sure that Trent is someone trusted. This could be a trusted entity who handles the data on behalf of the citizen (and preserves their privacy on their behalf) or a health authority that Alice trusts? It is unlikely that we should trust anyone else than health authorities, and also we need to make sure that the data gathered is only kept for the required amount of time. Any tracing of contacts should not be kept for longer than it is required, and only the clinical aspect of the tracing should be kept, and only provided to trusted health professionals.
- Where is Carol? There is s no trusted mechanisms to integrate a formal test for COVID-19, and where we bring in Carol the Tester. Carol the Tester would be able to define a state of testing: Positive, Clear, and Suspected, and will have followed a scientific process to provide Carol’s COVID-19 status.

- What is Carol’s attestation? We don’t want the government to control testing, and we thus need to have a trusted network of testers — from our own country and from other trusted places. Thus we need for a trusted way for a number of testers to sign the attestation that Carol has COVID-19, or when has been proven to be negative. A newer attestation will revoke a previous one. So will this attestation be in the form of passporting system, with digital verification, and allow Alice to carry a digital passport of being free from COVID-19, and that can be passed to others?

- The role of Trent is unclear. Overall Trent must be the health authority and not the government. Trent must be the one who marks the status of Alice as: Clear, Suspected, Not Known, and Positive. In this way, there is something defined by Trent that proves the status, and where the tracking will only happen when there is a positive status applied to Alice.

- Border control, and which countries/testers do you trust? The core flaw of having just one health authority involved is that there needs to be a trust between health authorities in different countries. In this way, we can trace over borders, when our travel system regains its operations. In this way, we need to define a trust network for Carol’s in each country and defines the way to hold the attestation, so that it can be shown at borders. Countries thus will define the testing trust network, and where Carol’s testing is trusted.

- There is no real integration of identities. How are we to properly identity Bob, Trent or Alice? Without having a private key signing for Alice and Trent, there is no real way of knowing that Alice is Alice and Trent is Trent. Thus, we need someone for each core identity to sign for the things they are signing, including for the health authority to sign for its own attestations.

- There is no clear mechanism for Alice’s consent. A fundamental flaw is the consent mechanisms that Alice must give to Trent in order to flip her current COVID-19 statement, especially in the changing it to a positive state. While Trent may have the rights to record Alice as being positive, he may need Alice’s consent as to whether she is okay with her COVID-19 state being broadcast to others.

- No binding of data. There is no method which truly binds the capture of contact data to the entities involved in a trusted way. The only thing it does is to mask Alice, until she is proven to have COVIT-19, after which her data can then be revealed to others, without any restrictions.
- There’s no signing involved. A core fundamental aspect of our modern world is that we introduce proper digital signing. As a minimum we should see key pairs being created for devices and entities, and where IDs and tracking are signed by private keys, and then checked for the correctness of the signer. There are many trusted signing methods, and which can be used to anonymise the signer.
In our world, we would setup a trusted permissioned ledger — such as with Hyperledger - with the identities of those involved carefully defined with signing keys. Then the permissions of all the transactions would be controlled by roles and identities.
I state three things I’ve learnt from working in health care:
- People trust their doctor to look after their data.
- People do not necessarily trust the government to look after their data.
- People do not trust private companies to look after their data.