Is Your Computer Fan Swirring … It Could Be Sending Secret Messages to Your Phone?

Is Your Computer Fan Whirring … It Could Be Sending Secret Messages to Your Phone?
The research team at the Ben-Gurion University in Israel have a long track record of sending messages over air gaps. This includes sending messages from vibrations in a USB stick. But now they have really stepped things up by proving that they can pick up message from the vibrations of a PC, and using the AiR-ViBeR method:

The team setup some malware on a computer, and which then sent messages to a mobile phone messages through vibrations passed through a table:

The method can cause vibrations in a computer, by varying the speed of a CPU fan, a GPU fan, a power supply fan, or chassis fan. Overall there is often good access to the power supply fan and the chassis fan, but where the power supply fan typically cannot be controlled for its speed.
Overall, the quality of the detection depends on the accuracy of the vibration sensor on the mobile phone. The researchers found that the access to the accelerometer did not require admin access to the operating system. This means that any application could gain access to the vibrations. In fact, the researchers were able to access the sensor using JavaScript within a Web browser. One of the best mobile phones for accelerometer accuracy is the Galaxy S10, and which has a sensor resolution of 0.0023956299 meters per second squared.
The proof of concept involves the connection of a Raspberry PI to the fan of a PC, and where the malware varied the speed of the fan, depending on the message to send:
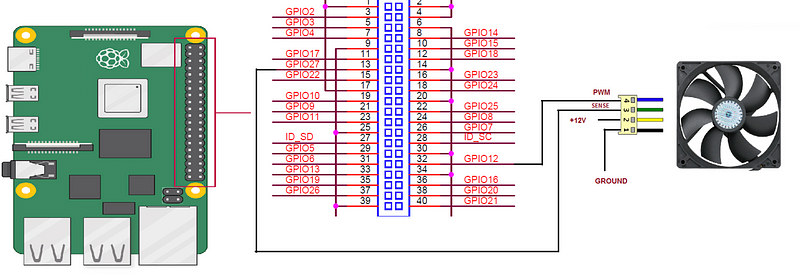
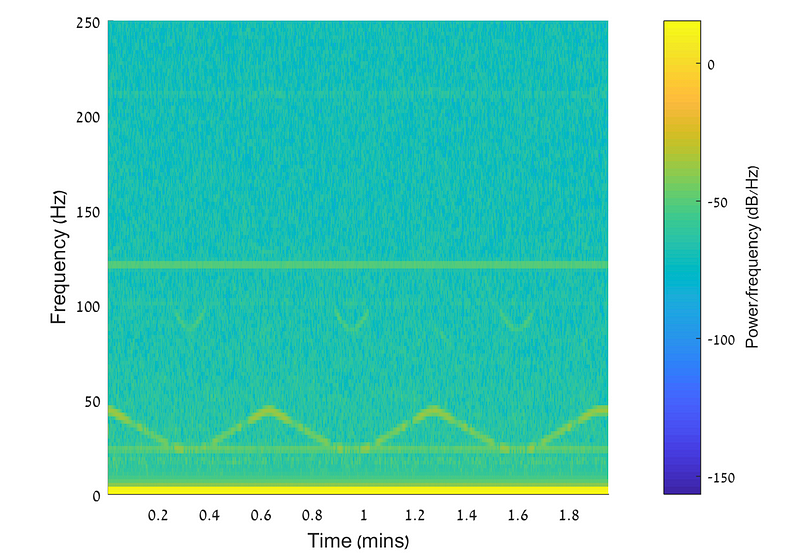
The researchers used thus used Frequency Shift Key (FSK), and where a ‘0’ bit set the speed of the fan at 1300 revs per minute (rpm) and then a ‘1’ at 2600 rpm. A third speed (RPMbase) is used to between the bits transmitted. The frequency of the received signal is then RPM/60 (21.6 Hz for a ‘0’ or 43.4 Hz for a ‘1’). For a message of 101010101 they received a spectrum of:
The team also modulated the fan using ASK (Amplitude Shift Keying), and which ran the fan at 2000 rpm and 2600 rpm:

Overall they found that the transmission rate was fairly slow. In the following we see the message being received over 1.4 minutes, and where we have some preamble at the start, and the followed by the payload, and a parity bit at the end:

A demo is here:
Conclusions
In our lab, we do a great deal of side-channel analysis, and here’s a recent paper on a hack on light weight cryptography: