Under The Hood of Zoom

Under The Hood of Zoom
There are so many things said about the security of Zoom, that it is often difficult to know what’s right and what’s not. So, let’s have a quick look:
We see the TLS connection with a server at 3.126.143.72. Other subnets include: 3.21.137.128/25, 3.22.11.0/24, 4.34.125.128/25, 4.35.64.128/25, 8.5.128.0/23, 13.52.6.128/25 and 52.61.100.128/25. Apart from TCP Port 443, Zoom uses UDP ports 8801 to 8010. Here is the basic TLS connection:

Initally, we see a standard three way handshake with the Zoom server, afterwhich the client sends a “Client Hello”:

In this case, we see that the Zoom client requests 21 cipher suites. Around half of these are ECDH (Elliptic Curve Diffie Hellman) for the handshaking of the key, but there are some that use RSA encryption of the session key. With this method, the client takes Zoom’s public key, and encrypts the symmetric key that the client wants to use, and then encrypts with Zoom’s public key. This is then sent back to Zoom, who will decrypt with their private key.
SSL Labs also identifies these as being weak [here]:
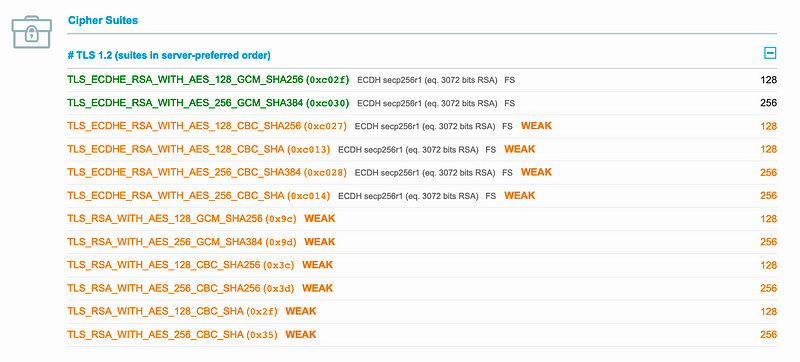
The RSA method for handshaking is weak, as a long term breach of Zoom’s private key could release all the other keys which were used. In the end the “Server Hello” selects 128-bit AES with a GCM mode, and with a key handshake of ECDHE with RSA, and SHA-256 for the hashing method:

If you are interested in the elliptic curve parameters for the key handshake, we can see we are using a curve of Sepc256r1 (just like Bitcoin!):

ECDHE with RSA is good, as it is ECDH with RSA authentication of the server. If you are interested, here is ECDHE with RSA: