NIST Recommendation for Key Management

NIST Recommendation for Key Management
I may be wrong, but the usage and understanding of encryption are one of the weakest areas of cybersecurity. I know some senior people in the industry who struggle to even get past the acronyms. And so it is great to see a new NIST document which relates to setting the best practice for key management [here]:

The guide should allow those in the senior roles to take the topic seriously. For security levels, it outlines that the baseline security starts a 112-bit security strength. For this we have 3DES (symmetric key) 1,024-bit RSA (public key), 1,024 bit Diffie Hellman (key exchange), and between 160-bit and 223-bit Elliptic Curve (ECC):


If you need 128 bit security, we start at 128-bit AES, 3,072- bit Diffie-Hellman, 3,072-bit RSA, and between 256–383-bit ECC. For 256-bit security, you’ll need 15,360-bit DH and RSA, and over 512-bit ECC.
For hashing methods, we see we start at SHA-224 for 112-bit security, but for 256-bit security we need SHA-512:

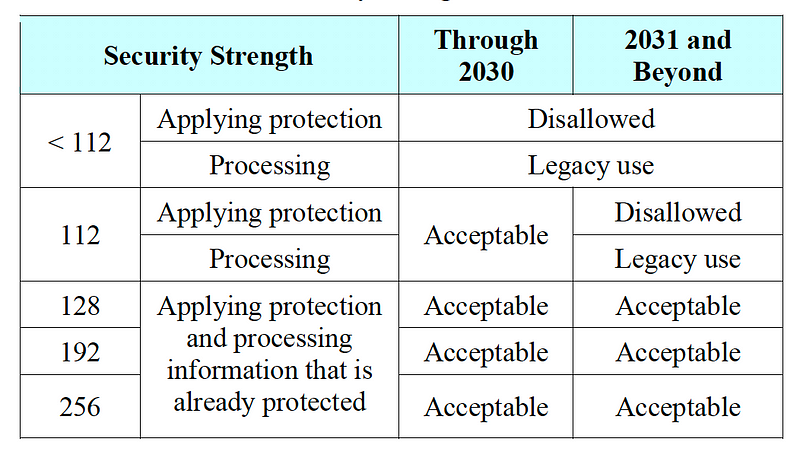
NIST defines that 112-bit security strength should be acceptable for the next ten years, but should be defined after that as legacy:
Well, here’s a fun test for your knowledge of keys. Can you make a million?
and one that is just an MCQ: