You’re A Professor of Crip — ology?

You’re A Professor of Crip — ology?
I was interviewed on LBC last week about NHSX App, and realised that some people in media struggle a bit “Cryptography”. When the editor called me she said
“How do you want to introduce yourself — you are a professor of crip-mm-graphy?”
“No, it’s cryptography”. And then the radio presenter:
“And so we have Professor Bill Buchanan, and who is a Professor of Crip-olology … oh, never heard that before”
Gulp! I had to correct again.
So, perhaps next time I might introduce myself as a Professor of Cybersecurity, and make things easier. Overall, though, I worried that the media — and the general public — possibly do not what cybersecurity is all about. We thus need to look at our industry and understand how we can better educate others on what we are all about.
At the present we are going through a recertification of our MSc programme, and the core knowledge areas are defined as:
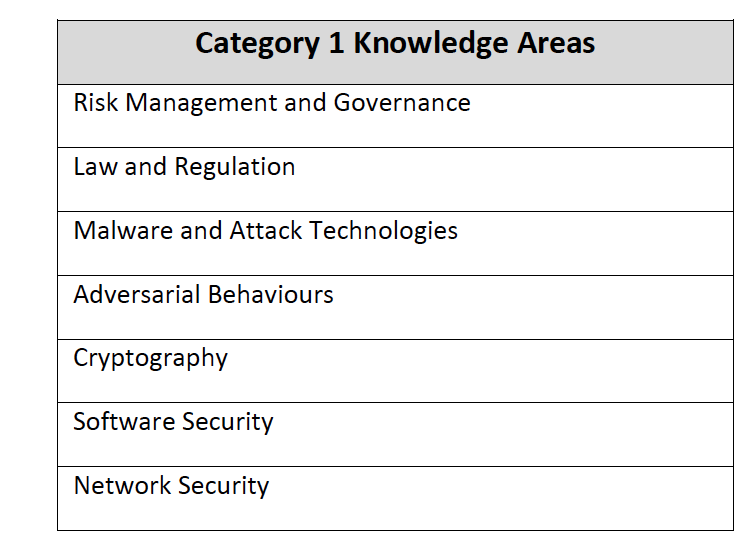
That is the core — the fundamentals — the equivalent of Ohm’s Law of Cybersecurity. To do an MSc in Cybersecurity, you should be doing these subject. As a professional, too, these should be our common base line knowledge. Then we get desirable areas:
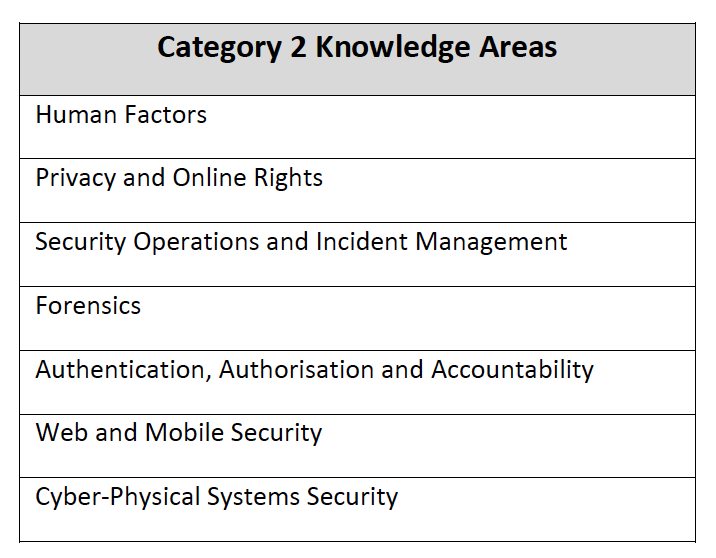
In the end we have core areas in Category 1, desirable ones in Category 2, and optional areas in Category 3:

52 job roles
NIST, too show the confusion in the usage of cybersecurity, and in the need to standardize job roles and knowledge areas:

But our current mappings between industry and academia do not quite match up the things that industry would define within jobs roles, where academia often fails to link with professional development. At one time an academic qualification might be the thing that gets you your promotion, but increasingly its more about the knowledge and skills that you have, and your career progression. NIST thus want us all to use the same names for roles, knowledge, skills and abilities, and this will help recruiters to identify the best candidates and for companies to plan their skills development activities.

In order to address this NIST has broken the field into categories and then split these into specialty areas, work roles, skills, knowledge areas and abilities.
For Cyber Security they define seven categories; 33 speciality areas; and 52 work roles [here], and then map these to 1,007 tasks, 374 skills, 630 knowledge areas and 176 abilities:
- Securely Provision (SP). Risk Management (RSK); Software Development (DEV); Systems Architecture (ARC); Technology R&D (TRD); Systems Requirements Planning (SRP); Test and Evaluation (TST)
- Operate and Maintain (OM). Data Administration (DTA). Knowledge Management (KMG). Customer Service and Technical Support (STS); Network Services (NET); Systems Administration (ADM); Systems Analysis (ANA)
- Oversee and Govern (OV). Legal Advice and Advocacy (LGA); Training, Education, and Awareness (TEA); Cybersecurity Management (MGT); Strategic Planning and Policy (SPP); Executive Cyber Leadership (EXL); Program/Project Management (PMA) and Acquisition;
- Protect and Defend (PR). Cybersecurity Defense Analysis (CDA); Cybersecurity Defense Infrastructure Support (INF); Incident Response (CIR); Vulnerability Assessment and Management (VAM)
- Analyze (AN). Threat Analysis (TWA); Exploitation Analysis (EXP); All-Source Analysis (ASA); Targets (TGT); Language Analysis (LNG).
- Collect and Operate (CO). Collection Operations (CLO); Cyber Operational Planning (OPL); Cyber Operations (OPS).
- Investigate (IN). Cyber Investigation (INV); Digital Forensics (FOR).
Conclusion
So, I’m a Professor of Cryptography, but to the media I’m now a Professor of Cybersecurity.