A Final Farewell To TLS 1.0 and TLS 1.1?

A Final Farewell To TLS 1.0 and TLS 1.1?
Chrome and Firefox push for better security
The Internet is often a place where you set something up, and then just forget about. But what happens when the Internet moves on, and where things are defined as insecure? Well, Chrome and Firefox wants to change that, and bring up standards related to SSL and TLS, especially in making sure that every site identities itself. Putting a digital certificate on a site is hardly the most dawnting thing for an organisation to do. So the Internet was warned back in January that Firefox was aiming to dump TLS 1.0 and 1.1 [here]:

In the above article a simple test generated:
- Google Chrome 80 states: “Your connection to this site is not fully secure. This site uses an outdated security configuration.”
- Firefox 72 warns: “Connection not secure. This page uses weak encryption.”
- Safari 12.1 displays no warning and says: “Safari is using an encrypted connection.”
- Microsoft Edge Chromium displays no warning and says: “Connection is secure.”
- Microsoft IE 11 displays no warning and says: “This connection to the server is encrypted” (though you can block these protocols in Internet Options).
- Brave 1.2.43 displays no warning and says: “Connection is secure.”
- Vivaldi 2.10.1745 displays no warning and says: “Connection is secure.”
And we now see these messages for an insecure Web site:

And, low and behold, when we assess it’s security it fails almost completely for its protocol support [here]:

This is the site of academic instition, and which should be one of the most trusted places on the Internet. A quick assessment of the SSL protocols shows the problem:
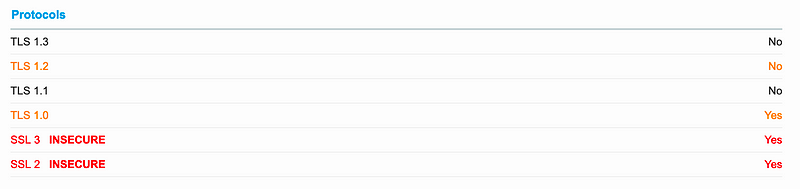
Here, we support SSL 2, which should never be seen, and it only goes up to TLS 1.0. It’s as if the security of this site has never been touched for years. Then every cipher suite that it supports is also weak, with 3DES, RC4 and MD5 even making an appearance:
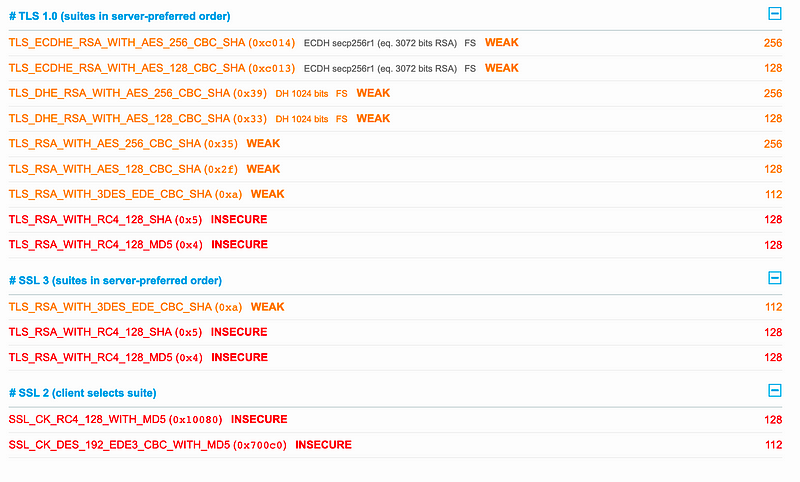
And because it’s still supporting SSL 3, it is vulnerable to BEAST:

If we use Openssl, we get:
— -
No client certificate CA names sent
Peer signing digest: MD5-SHA1
Peer signature type: RSA
Server Temp Key: ECDH, P-256, 256 bits
— -
SSL handshake has read 3809 bytes and written 457 bytes
Verification: OK
— -
New, TLSv1.0, Cipher is ECDHE-RSA-AES256-SHA
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1
Cipher : ECDHE-RSA-AES256-SHA
Session-ID: 054D0000DF40A807A8B02B5E1CD169CED2F13806E4E62B15E34CC9EACFE2046B
Session-ID-ctx:
Master-Key: 40CC1E95498543BD5602534E1F2891199C3DB9E5A950E68C016B5C04AADDD53600CBE8A81F563A538C0949465E38E858
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1594322067
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: yes
But while there are still isolated sites that are not testing for their operation, generally SSL v2 and v3 are poorly supported, but TLS 1.0 and 1.1 is still hanging in there with more than 50% of the site supporting them:

Well, here’s a quick outline of SSL/TLS:
and some background content:
Back] This page creates a secure connection with a remote Web site. The following are some samples: [ Google] [ Live] […asecuritysite.com
Conclusions
If the Internet still used Internet Explorer, we would probably still generally be in a world without any core security. TLS and HTTPs are not the best around, but at least they give us a base line for security, and a foundation to build on. Perhaps we need to rid ourselves of these tunnelled protocols and looks for proper encryption of all our data, but it takes time to change, and this is a great step forward? Firefox and Chrome are forcing changes … “if you don’t change, you will be seen as insecure by your customers”.