The DoubleWammy: Ransomware + Data Exfiltration

The Double Whammy: Ransomware + Data Exfiltration
What Other Industry Will Often Pay Extortion Requestions?
And so Blackbaud — the latest company to be hit by ransomware — annouced:
“Because protecting our customers’ data is our top priority, we paid the cybercriminal’s demand with confirmation that the copy they removed had been destroyed.”
Honestly? You can trust a cybercrimal to delete all the data they captured?
APT + Ransomware + Data Exfiltration
So the Lockheed Martin Kill Chain model defines a weaponize process. For a cybercriminal, this weapon is increasing has two attacking methods: ransomware and data exfiltration. The way in can vary, and many more serious attacks are not focused on blinding phishing an organisation, but to target them with an APT (Advanced Persistent Threat). An intruder thus finds a way into the organisation infrastructure, and then waits for a while, and observe. Their blunt weapon is ransomware, but they keep this back, as once it is deployed, they will have to leave, and the defence systems will go into overload. Before they leave, their task is to steal sensitive data from the organisation, either to sell back to the organisation or to sell for malicious reasons. Once they have that, they will often disable backups and Anti-virus, and then they can drop the ransomware attack, and leave. The cybercriminals now have several routes to profit: the encryption key to unlock the ransomware; the extortion request for the data; and the selling of the data to others. All of these have a high chance of success!
Blackbaud
And, so, we are increasingly moving to the cloud, and that move not only involves us moving our own company’s data into the Cloud but also the increasing usage of cloud-based services. These services are then integrated into a corporate infrastructure. For example, we use Worktribe for our research project management and have a cloud-based system for our HR system. These systems — especially related to engagement and HR information — can hold sensitive information, but are often held away from the organisation. So what happens when these systems are attacked? Well, it happened last week with Blackbaud was brought down by a ransomware attack. The company is one of the largest fundraisers within the charity sector, along with having many university contracts which supports engagement with alumni contacts:

And what did Blackbaud do? They paid the ransom! Like it or not, if you can’t find the private key that the attacker has used, you have very little option. So while this benefits the criminals, one must worry that the adversaries will have taken some of the highly sensitive data off the site, and where it could be sold to others (or used as a follow-up extortion request).
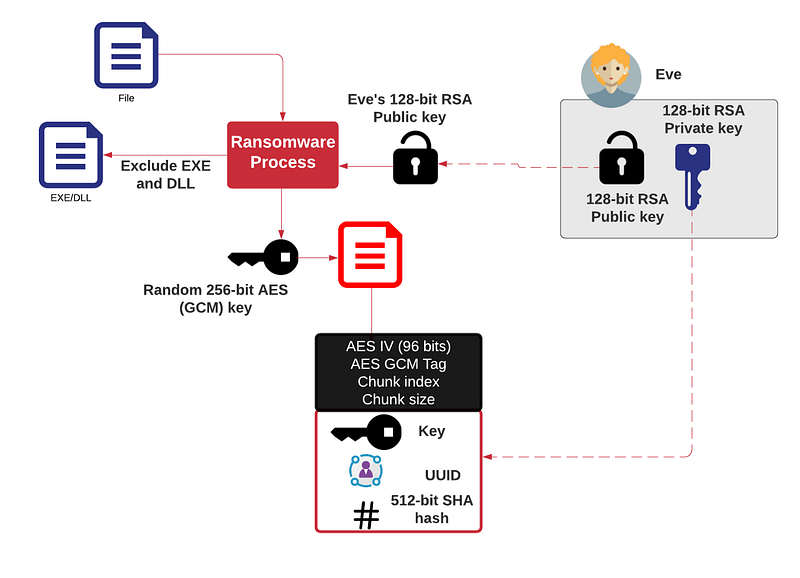
Simple ransomware overview
If you have no back-ups, once your files are encrypted with a key, you have very little chance of getting them back. Here is a typical process, and where each file is taken, and then encrypted with AES (using GCM mode — to make things faster), and then where the key used is encrypted with the public key for the adversary (Eve):
The true cost of ransomware?
The true cost of a security incident is difficult to estimate, but some attacks such as ransomware allow for a tangible appraisal of the impact. Emisoft has now tried to quantify the costs for recent attacks [here]. For 2019, they focus mainly on the US and found that, at least, 966 government agencies, educational establishments and healthcare providers were infected by ransomware and that the potential cost is greater than $7.5 billion. This included 113 state and municipal governments and agencies, 764 healthcare providers, 89 universities, colleges and school districts (with 1,233 individual schools affected).
For 2019, Emisoft estimates a total ransomware demand of over $25 billion (Table 1), and with the US, Germany and Italy suffering the largest number of demands.

Table 1: here
But the cost of the ransomware does not tell the full picture, as there is an impact on downtime costs. The estimated overall cost now rockets to over $169 billion (Table 2).
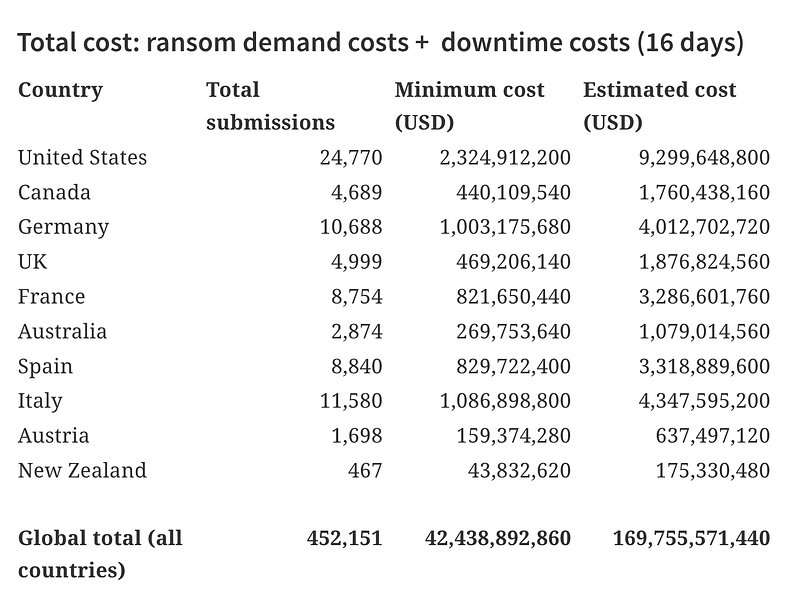
Table 2: here
Within their analysis, Emisoft discovered that the STOP ransomware was the most popular type and that the average ransomware demand was $84,000. But, in 2020, they have observed that the demands have increased significantly. They also think that 33% of companies pay the ransom demand, and that the average downtime is 16 days. Their estimate for a daily cost is pegged at $10K per day. In many cases, this cost will be MUCH higher.
The public sector
Emisoft is fairly damming in their coverage of ransomware incidents, and give the observation that while there were attacks against 966 public sector agencies, there was not one disclosure against a bank. While equally a target, banks tend to have better defences, and Emisoft point to the public sector perhaps adopting best practice within their security infrastructure. Two core areas of focus are perhaps to enable MFA (Multifactor Authentication) on their systems — as this has been proven to thwart at least 99.9% of all account comprises — and enable backups.
But Emisoft highlight that organisations should be careful around a reliance on backups, and where the recovery of files is often not an easy thing. The recovery process often requires days, weeks or even months of painful restoration. This, of course, is not good within areas which require no down-time, such as in hospitals and criminal justice.
Emisoft has an insightful viewpoint and observes that those with cyber insurance may be more ready to pay the ransom. But this could be counter-productive, as it insentivizes cybercriminals. A proper investment in defence, and an investment in cyber insurance, together, are possibly the best strategy. They define thus that cyber insurance is not an alternative to proper investment in security.
Emisoft also highlights that the double whammy attack, and where an attack both encrypts the files locally and also exfiltrates some of the data off the site. This results in a double ransom demand, for the decryption of the files, and for the deletion of the exfiltrated data (of which it is difficult to know if it has been done successfully). As the public sector often has personally sensitive information, this could cause a major data leakage incident.
Conclusions
Emisoft’s main focus was on government agencies, but their conclusions can scale to most organisations:
- Improved security standards and oversight: Government agencies often have weak security and poor auditing.
- More guidance: Emisoft define that there needs to be improved baseline security levels and that investment needs to be targetted.
- Security debt and funding: Many government departments have been underfunded in terms of their cybersecurity infrastructure, and perhaps funds needs to be redirected, or funding increased in key areas.
- Closing the intelligence gap: Government agencies often do not share incident details, but this sharing could help build up intelligence on the threat landscape.
- Better public-private sector cooperation: With this, there needs to be strong partnerships between the private sector and the public sector.
- Legislative restrictions on ransom payments: Many government agencies end up paying the ransom, and this is a model that is not sustainable, as it makes ransomware more attractive to cybercriminals.
- Vendors and service providers must do more: Vendors and service providers need to provide better support for government agencies, and work with on monitoring and protecting public sector infrastructures.
So I leave you with the question … what other attack on a company would — more often than not — result in a ransom demand being paid?