When Teaching Mirrors Real-life … Sunburst, Solarwind and Soaring Cybersecurity Stock Prices

When Teaching Mirrors Real-life … Sunburst, Solarwinds and Soaring Cybersecurity Stock Prices
We are proud of our Network Security and Cryptography module which myself and Rich Macfarlane teach. And so for the coursework (which had a submission date this week) we setup a fake bot and a controller using .NET programs, and then get students to analyse the bot. They must then understand the traffic generated from the bot, its static code, its behaviours, and its running code. We also encode messages with ciphers and hashes, so that students can use their skills they have learnt on the module to crack them. For this they have Wireshark, a firewall, and Snort at their finger tips [here]:

For this, each student has their own virtual infrastructure (within our vSoC infrastruture), and then ask them to protect the network using a firewall and to implement a detector with Snort. And guess what was announced this week? The Sunburst backdoor within the Solarwinds hack, and which sent the stock prices of companies such as FireEye Inc, Palo Alto Networks and CrowdStrike Holdings soaring. And what did it use? A .NET backdoor, with DNS encoded cipher messages, and where Snort is then used to detect the backdoor. The current analysis of the backdoor, too, also follows our approach of the methods that students our students have followed for their analysis.
The soaring stock
Well. Cybersecurity and Biotech are kinda strange industries. Often when there is bad news, it can leave companies with soaring stock price valuations. And so, with the announcement of the SolarWinds backdoor, it happened for companies such as FireEye Inc, Palo Alto Networks and CrowdStrike Holdings, and with FireEye seeing a massive 33% rise in its stock price over a single day:
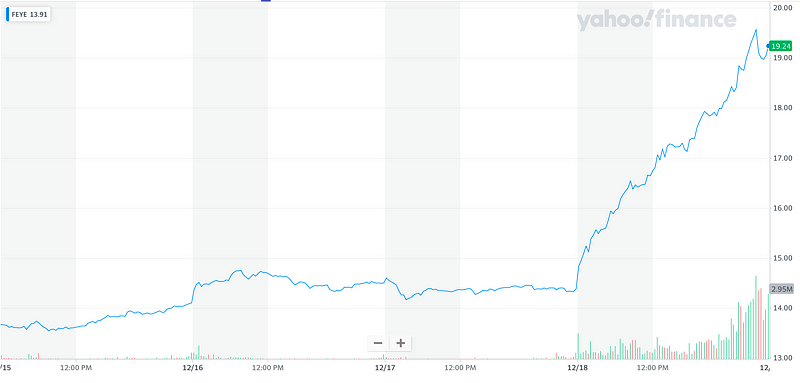
The soaring stock price was stimulated by the SolarWinds hack, and the likely consequence of governments of the world investing heavily in cybersecurity to both investigate the hack and improve their defences. On the announcement, Solarwinds announced that they were installing CrowdStrike’s Falcon Endpoint Protection Platform, and which sent CrowdStrike’s stock into overdrive:

Let’s Zoom in:

The announcement was made at 10:13pm ET on 17 Dec 2020, but look around 4pm on the 17 Dec 2020, there was a dramatic rise in the trading on the shares:

This can only point to the fact that the press release was leaking to some people who trade shares and look to bail into companies which were likely to benefit from the SolarWinds hack. The pre-trading before the announcement is also seen around another company (Cisco Systems Inc) named within the press release:

The Backdoor
It was on 13 Dec 2020 that FireEye published details of a .NET backdoor (Sunburst) on the SolarWinds Orion IT software, and which was downloaded by around 100 companies. It is thought that the backdoor may lie dormant for a few weeks, and then look to contact a C&C (Command and Control) server using encoded DNS requests. The DNS response then includes the CNAME of a second-level C&C server. Fireeye released details of the request and response [here]:

For this, FireEye have already published Snort rules to detect the presence of Sunburst [here]:

QiAnXin Technology, too, has since published a Python script to decode many of these encoded names [here]. Researchers, too, have used a .NET compiler to reverse the code, and found that it uses four different methods to send DNS requests:

While it is possible to decode many of the encoded URLs, there are others which seem to be encrypted and are still to be found. Once these are all traced, it should be possible to find out where exfiltrated data from a wide range of companies and governments actually went. The mystery continues …
Conclusions
The module that Rich and I taught has been so interesting this year, and we hope our coursework matches exactly to the ever more complex world of cybersecurity.