Protecting Against Side Channels with Re-keying: Meet Isap

Protecting Against Side Channels with Re-keying: Meet Isap
There have been many examples of systems being cracked through side-channel analysis. One of these methods is differential power analysis (DPA) and where an intruder can obverse the operation of the encryption key through electrical disturbances. One way to overcome these problems is to only use a key for a short time, and then to generate a new one. If an intruder finds one of the keys, it will only be relevant for a short-time, before they have to rediscover the new key. This is likely to be expensive in cost and time. We thus need a way to have a pre-shared secret key and then derive our session keys from these. The pre-shared secret key can then be kept secure, and the process for generating the session key can be protected against side-channel leakage. The re-key method is fairly standard in TLS and tunnelling but has struggled in its implementation on devices. Here is Dr Owen Lo doing a live DPA attack on an embedded device:
Differential Power Analysis (DPA)
The work of modulating the power rails on chips is well documented for discovering encryption keys, where the security and protection of the key is reduced. There has also been work on a “cold boot” where the memory chips are frozen, and which keep their bit states:
Until recently, we all thought that SIM cards were secure from most types of attack. But Prof Yu-Yu from Shanghai Jiao Tong University has now shown that 3G/4G SIM cards, using 128-bit AES, can be hacked — so the nightmare of SIM card cloning could come true [paper].
The access to SIM encryption keys is a key focus for law enforcement, and it was highlighted earlier in the year when law enforcement agents were suspected of stealing the billions of encryption keys from Dutch SIM card manufacturer Gemalto. These keys would allow access to both the data and voice messages on the phones.
In his Black Hat USA 2015 presentation, Prof Yu-Yu outlined how a differential power analysis method that recovers encryption keys from SIM cards and which allows them to be cloned. Overall it takes 10–40 minutes to recover the key, and his method has succeeded on eight of the most popular SIM card manufacturers.
He uses basically an oscilloscope to capture the power changes and a MP300-SC2 protocol analyser, along with a PC to analyse the cryptography (Figure 1). The work uses Differential Power Analysis (DPA). With Simple Power Analysis (SPA) we monitoring the power consumed by the processor, and this can give hints on the contents of its registers and data buses.
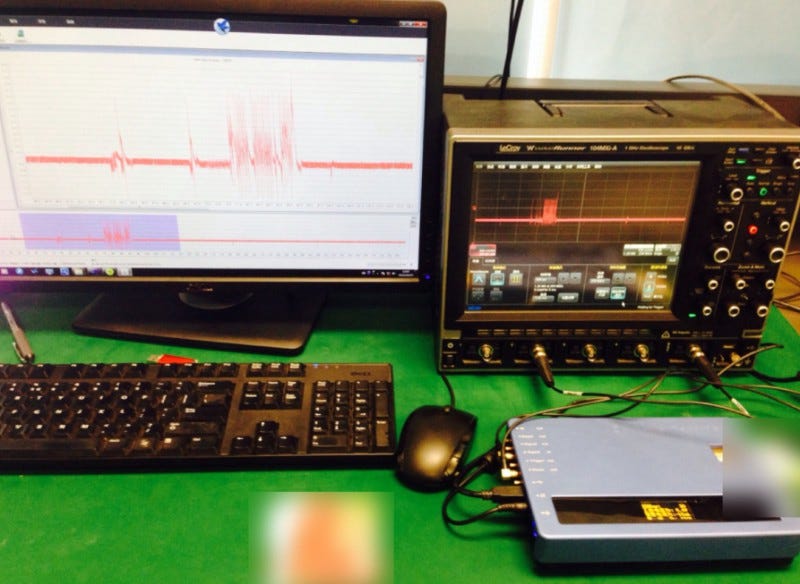
Figure 1: Prof Yu-Yu’s experimental setup
With DPA, the chips are given some tests for encryption, and then the power levels are observed for the chips, after which they are analysed to show a correlation of the bit patterns used (Figure 2). The differences in the encryption process are then used to crack the key. For example, we take some test data, and apply a range of keys to the device, and watch the power levels. Each of the power consumption levels will change depending on the activity within the chip.

Figure 2: Power analysis of the AES method
Isap and re-keying
One of the key areas of protection is in device security, and NIST’s competition on light-weight cryptography aims to assess a range of methods against things like performance, ease of implementation, and robustness. One of the most important aspects is the robustness against side channels, and Isap is one of the methods in the final stage.
Overall Isap focuses on a re-keying approach for a lightweight cryptography method. It is a light weight block cipher and was written by Christoph Dobraunig, Maria Eichlseder, Stefan Mangard, Florian Mendel, Bart Mennink, Robert Primas and Thomas Unterluggauer. Isap is focused on robustness against power analysis and fault attacks and where there is a node for small code size. Overall it uses a sponge-based mode with SPN permutations. Isap also has mechanisms to protect gain fault attacks and uses an Encrypt-then-MAC design with two keys for IsapMac and IsapEnc.

In most methods that protect against DPA, we have a secure side-channel initialization of the key and then use a pre-shared master key and a nonce, and where a new nonce is used for each session. This is useful against an attack on the sender’s encryption process, but it is not so easy to generate different session keys based on the long-term key and the received nonce. One way to do this is to generate a nonce value to all the parties involved, and then allow them to generate session keys from these, but this has significant overhead in communicating the nonce value. The Isap method overcomes this problem by protecting against DPA for both the encryption and decryption process. Along with this, Isap now integrates AEAD, and which allows the ciphertext to be authenticated by the receiver before it is actually decrypted.
With re-keying, we limit the number of processed inputs we can have for each key which is used. Typically, with DPA, we would need many samples of the process for our encryption key analysis, so limiting the number of times it is used, will significantly reduce the opportunity to discover any of the derived keys. With frequent re-keying, as would be seen in areas like RFID tags, we use a new key (K*) for every new plaintext, and which is derived from a pre-shared master key (K), and a nonce (N). If we define g as the generator function we can represent as:
K* = g: (K,N)
As long as our key generator for K* is secure, we should be protected against DPA attacks. The following page implements Isap using the ASCON light-weight approach:
Back] Isap is a light weight block cipher and was written by Christoph Dobraunig, Maria Eichlseder, Stefan Mangard…asecuritysite.com
And here is the running code: