Don’t Over-egg Your Profile …

Don’t Over-egg Your Profile …
Oh, you have to smile about the “industry” that is Cybersecurity. It is an area that has around 52 different job roles, but still we wrap it all up together as a single entity. On broadcast media and in conferences, you sometimes see people boosting their expertise, for their Cybersecurity experience. As it is an evolving area it is one area where those with little actual experience and knowledge boost themselves forward with profiles that don’t quite match reality.
The medical profession, for example, has long has had a history of individuals boosting their expertise, and this is one reason that academia has a strong peer review process in both promotions and for research publications. Through a peer-review process, someone who overpromotes their expertise is likely to be found out. But, as cybersecurity requires high levels of trustworthy knowledge, it is important that true experts are able to prove their viewpoints.
But things often get through, and the RSA conference yesterday posted this message:

It related to a blog and social media post which proposed that the flaws in TCP/IP could be solved with blockchain [here]:

The blog proposed to overcome TCP/IP with blockchain. In the end, it is a generic piece that ends up on cryptocurrency and Bitcoin, and with little relevance to the flaws in TCP/IP. While these types of articles are all over the Internet, it was the background of the author that brought many questions. In a classic case of bending the truth a lot, it outlined his 30 years of experience in blockchain and Defi [here], a whole lot of blockchain expertise, and publication record:

While decentralised currency methods have been around in the 1990s, and Merkle invented the Merkle Trees in the 1980s, there is little chance that Rohan was even thinking about the transformations that public key could make to finance. And, it would be surprising if Rohan worked closely with Satoshi Nakamoto on his Bitcoin work around 2009. And, if you are interested, here’s Rohan’s book (from 2004):

I smile, as it is so easy to keep adding things to your bio, and forget what you updated. When you present at a conference, you want to make your experience look relevant, and show your expertise in the area. On Rohan’s LinkedIn profile, it is much more sensible [here]:

In academia, we have had great problems in the past with his type of overexpression of expertise. This is especially relevant when publishing in poor quality journals and conferences. We thus look to other metrics to define the overall quality of the work, such as impact factors on journals, citation counts, and conference quality assessments.
Overall, though, we tend to keep our feet on the ground, as anyone can review our h-index score or the number of citations we have. For Ron, we can see his papers have been cited over 148,000 times, and 106 of his papers have more than 106 references:

His impact is obvious, and he is a true expert in his field. Within academia, we tend to stick to our outputs and impacts which can actually be proven in some way.
In the case of Rohan’s article, the quality of the article perhaps does not match the quality of the conference, and so RSA pulled it. Rohan, though, has great experience, and I am sure he runs a successful company. But there’s a balance to be struck between creating an interesting and engaging article, and something that is generic click-bait content.
Black Hat
And it’s not just at the RSA conference there’s questions over expertise, it happened at Black Hat in 2019, and where someone shouted:
“Get off the stage … you shouldn’t be here! Black Hat are going to take all this down”
at research presentation [here]. The focus was on Robert E. Grant and where cryptographers and academics around the world started grumbling and even openly shouting over social media that they think there’s something not quite right with his company’s claims:

One thing you learning in academic research is that you need to get things right, and the title itself rings alarm bells:
The World’s First ‘Non-Factor ‘ Based Quantum Encryption Technology
The title is completely wrong! As I said before, encryption involves both symmetric key and asymmetric key methods, and symmetric key methods — such as AES and ChaCha20 — don’t go anywhere near factorization. In an academic conference, the title — or any claim like this — would never be allowed (unless proven to the nth degree).
Also, there are lots of “Non-factor”-based quantum encryption methods, and NIST is looking at that now!
And then the thing that has gotten many researchers hot under the collar is the claim:
In March of 2019, Grant identified the first Infinite Prime Number prediction pattern, where the discovery was published on Cornell University’s www.arXiv.org titled: “Accurate and Infinite Prime Number Prediction from Novel Quasi-Prime Analytical Methodology.” The paper was co-authored by Physicist and Number Theorist Talal Ghannam PhD. The discovery challenges today’s current encryption framework by enabling the accurate prediction of prime numbers.
The paper is here:

I can’t even start to explain how making a claim like this, by saying it is published on arXiv is academically unsound. If you know the peer review process, then you will know that anyone can publish a pre-print there. I have only just recently been using it, and here are some of mine’s [here]:

The first paper here has been published, and No 3 is just going to production, after two peer-review stages. Papers 2 and 4 are still in the peer-review process. While we can make claims on the findings in paper No 1 and No 3, we cannot make any claims, yet, on paper 2 and 4, and, in fact, they may get rejected outright, and we would probably remove them from arXiv.
As part of peer review, there should be a rigorous analysis of the methods used, and the paper will only be accepted into a peer review journal if it has been shown to produce a significant contribution. But, in the case of the TIME AI paper, there is no existing peer review done on it, even though it is claimed in the press release. This is a crazy situation, and media outlets have been happily publishing the press release with little care that it is currently building on sand.
One of the people I respect most in cryptography is JP Aumasson, and who has a long track record of core contributions in computer security. Here is his thoughts on the presentation:
Go read here. There are claims too about the confidentiality of a talk. Surely if you give a talk to an audience who will listen to you, then they are not is not quite confidential. Basically, you would have to get everyone who attended the talk to sign NDAs before it and take their mobile phones away. And, there are big questions, too, about the sponsorship of the talk. Continually we get called by conference agencies asking us to pay to present at any event, and we always say, “No!”, as it compromises our academic integrity.
The company have a strange profile — and perhaps wacky profile — and even advertise 5D encryption:

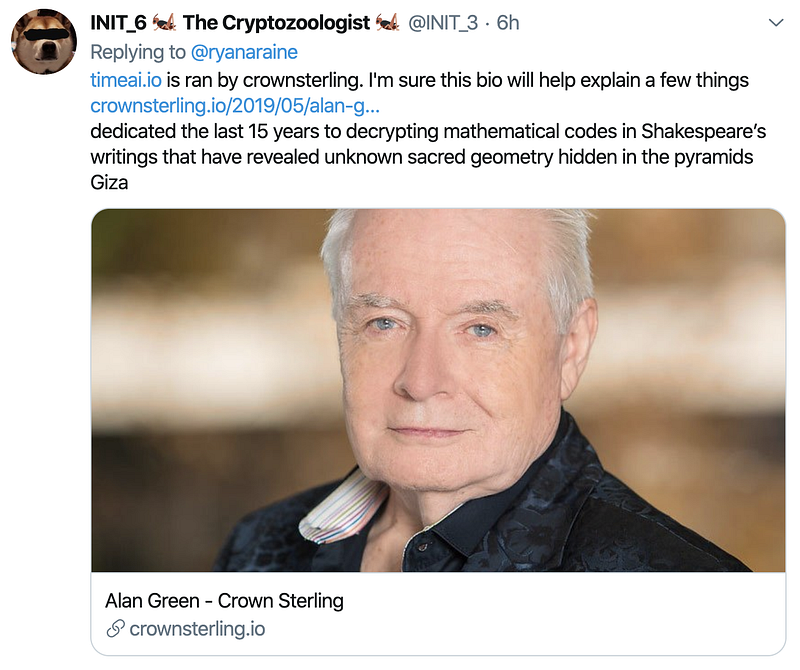
And for the company founder, some have been highlighting a rather strange history in research:
Conclusions
So … watch your bio, and don’t overegg your actual experience, as someone will catch you out. In this case, there’s been a little bit of editing of the profile, and where the level of the blog item did not hit the market. For me, I’m off to review my AWS Infinidash board experience:
