Meow The Infinite — The “Fastest” Key-based Hash Around?

Meow The Infinite — The “Fastest” Key-based Hash Around?
In cryptography, sometimes, you need to be fast. If you have gigabytes of data, you need to process your data efficiently, and with lesser regard for the overall security.
Unfortunately, most of our cryptography methods are focused more on efficiency and security, to be bothered with being as fast as possible. But when you need Gigahashes per second, you need to find ways to optimize the hardware and make full use of it. And so we turn to a hash created by Molly Rocket [here] and is named after a character known as Meow the Infinite [here]. It was created by Jacob Christian Munch-Andersen [here] and Caset Muratori [here].
Their problem was that they processed many hundreds of gigabytes of game assets and wanted a hash that could cope with high throughputs. Unfortunately, the existing SHA methods were just too slow. They thus found that most of the existing fast hashes focused on smallish amounts of data, and did not find any methods to suit them. And so they created the Meow hash. It is super fast with a data buffer of many gigabytes and can produce a 128-bit hash output. The authors think it is the fast hash around. Along with this, they do not make any claims for its security, as they just wanted a fast hasher that did not produce collisions (as tested by smhasher). In some cases, we do not need a total robust hashing method, if we only just need to protect against collision, such as with a hashtable.
An AES engine
Meow is a key-based hashing method, and where we use either a pre-defined default key or a random one, for each hash. One of its core advantages for Meow in its speed is that it is based on AES methods, and where the code can use the embedded AES engine. For this we compile:
gcc -maes -mavx meow.cpp -I ./ -o meow
In this case we compile meow.cpp with “-maes” and “mavx” switches. These enable access to the AES engine on the processor.
1,024-bit key and 128-bit hash
Overall, Meow is defined as a non-cryptographic key-based hash. For this, we have a 1024-bit seed (the key) and produce a 128-bit output. In this case, we use a default seed value for the key (MeowDefaultSeed), and a Buffer to hash (with a given Size in the number of bytes in Buffer):
meow_u128 Hash = MeowHash(MeowDefaultSeed, Size, Buffer);
With the default seed, the designers think that the hash can be seen as being insecure, but with a random seed, that it will be secure. Here is the “nothing-up-our-sleeves” default seed:

A running version of the code is here:
https://asecuritysite.com/encryption/meow?val1=test
We can run the code on Repl.it by compiling with the correct switch options [here]:

A Level 3 hash
Meow is defined as a Level 3 hash for its security, and can be used for hash maps and for MAC (message authentication codes), but lack the methods required for a Level 4 and Level 5 hash which do not need a secret key to keep them secure. At Level 5, we typically define the method as a cryptographic hash, such as with SHA-1, SHA-256 and SHA-3. The levels are defined here.
Some of the claims of Meow, though, have been reviewed through a full cryptoanalysis here:
Meow hash is a fast keyed hash function, on GitHub here. At time of writing, Meow hash has 1.2k stars and has several…peter.website
Other non-crypto hashes
One of the most popular non-crypto hashes is the Siphash [here]. In the analysis below we can see a throughput of more than 6GB/s:
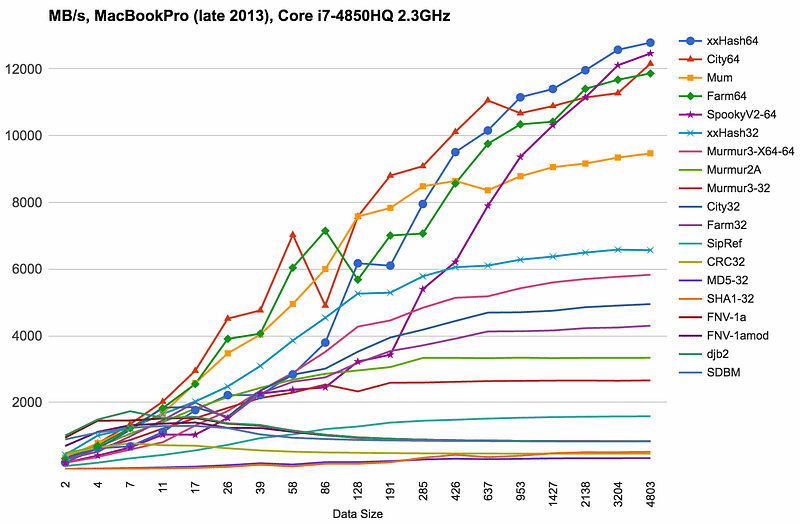
For xxHash, we see that xxHash was over 15 times faster than SHA-1 [here]:

Some of the fastest non-cryptography methods are:
- FNV. FNV. FNV is one of the fastest hashing methods.
- Murmur. Murmur. Murmur is one of the fastest hashing methods.
- Siphash. Siphash. Siphash is a fast hashing method.
- Spooky. Spooky. Spooky is a fast hashing method.
- xxHash. xxHash. xxHash is one of the fastest hashing methods.
These methods have been around for a longer time than Meow, and have thus been probed for their vulnerabilities. Saying that, if you just need to create a collision free hashing method for a hashtable, Meow looks to be a reasonable alternative to many of the other methods.
Conclusions
In some cases, we need speed, and not necessarily super-duper security. For a hashtable list, the non-cryptography hashes are up to the challenge. For more public methods, we would avoid them for actually deriving a hash value, and would use the cryptography hashes for their overall robustness and proofs.