The Swiss Army Knife of Cybersecurity: OpenSSL

The Swiss Army Knife of Cybersecurity: OpenSSL
The Program Which Jumped From Version 1 to Version 3
When I was an electrical engineer, my standard tester was my trusty DVM (Digital Voltmeter). But, in Cybersecurity, my trusted tester is one little program that never grew up but which often provides the foundation of security on the Internet … OpenSSL.
The program that caused Heartbleed
It all started with Eric A Young and Tim Hudson, in Dec 1998, and who created the first version of OpenSSL (it was known as SSLeay — SSL Eric A Young). It has since become the program that caused HeartBleed and which generated a lot of other serious bugs.
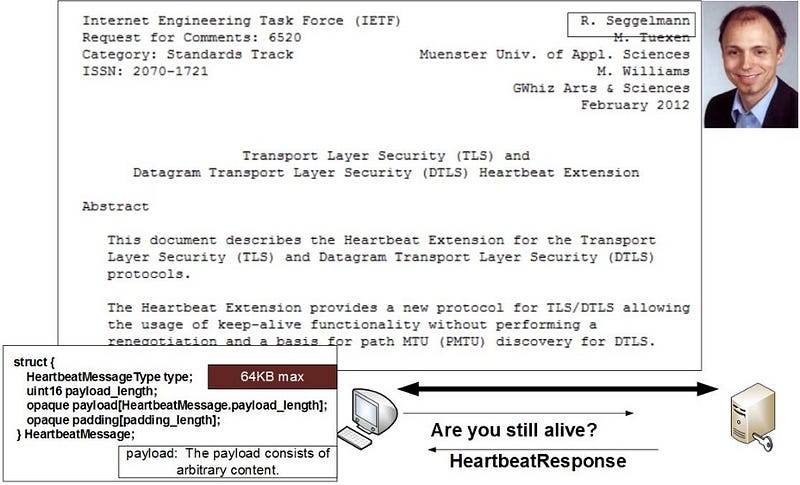
Eric finished his research and was involved with Cryptsoft (www.cryptsoft.com) before joining RSA Security as a Distinguished Engineer. After Eric left, it was then left to Steve Marquess (from the US) and Stephen Henson (from the UK) to continue its development through the OpenSSL Software Foundation (OSF). The code continued to grow with TLS support added to 1.0.1a on 14 March 2012. Unfortunately, a bug appeared on 1 Jan 2012 which implemented the Heartbeat protocol (RFC 6520), and which ended up resulting in Heartbleed (Figure 1). The bug was actually introduced by the same person who wrote the RFC — Robin Seggleman, a German developer. If you want to know more about HeartBleed, click here.
And so the OpenSSL Foundation continued on a shoe-string budget, even though it was at the core of the security of many systems. Other companies, though, looked to replace it with a more up-to-date library, including Google Tink and Amazon s2n. But, to this day, it still exists and is still the ‘go to’ program for testing digital certificates, TLS connections, hashing methods, public key pair generation and symmetric key encryption.
From Version 1.1.1 to Version 3
The last Version 1 release was 1.1.1 on 11 September 2018. It brought a wide range of new cryptography implementations including the SHA-3 hashing method, TLS 1.3, and new symmetric key methods such as ARIA and ChaCha20. It was then a surprise when it then jumped to Version 3.0 on 7 September 2021. As before this kept backwards compatibility and including a new FIPS module (and where FIPS defines standards for cryptography implementations).
Implementing with OpenSSL
So let’s view the hashing methods in 1.1.1. The Linux and Windows commands differ, but both use a piping method to feed data into OpenSSL. We, of course, need to avoid a new line after the text, so we suppress this. The following gives us an example of the word “Hello” hashed in MD5:
Linux command: echo -n "Hello" | openssl dgst -md5
Windows command: echo | set /p = "Hello" | openssl dgst -md5
Message: Hello
Mode: md5
========
8b1a9953c4611296a827abf8c47804d7
The “-n” and the “set /p” options suppress a new line after the string. Using this approach, we can easily code for the other methods [here]:

As we can see, OpenSSL now integrates Blake2b, and which is one of the fastest cryptography hashing methods around. So with hashing, OpenSSL is the Swiss Army Knife of Cybersecurity.
We can also do the same with symmetric key methods, and where OpenSSL integrates virtually every one of the common symmetric key methods, and in a range of modes. Obviously, AES is the most common method, but the ChaCha20 stream cipher method is becoming popular (as it is fast and efficient and an alternative to AES). For example with plaintext data of “Hello” and with 256-bit AES CBC with a passphrase of “qwerty” and a salt value of “241fa86763b85341”, we get a cipher result of:
Linux command: echo -n "Hello" | openssl enc -aes-128-cbc -pass pass: "qwerty" -e -base64 -S 241fa86763b85341
Windows command: echo | set /p = "Hello" | openssl enc -aes-128-cbc -pass pass: "qwerty" -e -base64 -S 241fa86763b85341
U2FsdGVkX18kH6hnY7hTQZ+x9aQ/9b8/DHe9E5n6lxA=
The value of “U2FsdGVkX18” is the word: “Salted__”, and defines that the next part of the salt value. This salt value then follows, and then the ciphertext. Here is the code running on a Mac:

The message says we are using a deprecated key derivation method, so we would just add “-iter” or “-pbkdf2” options. These are improvements as they slow down the generation of the key from a passphrase.
Again, we can implement all of the supported methods and modes [here]:

As we see for AES, we have either 128-bit or 256-bit encryption keys, and a whole lot of modes (ECB, OFB, CTR, and so on). Each of these modes differs in the way they create the cipher, and some even move away from the block cipher approach and implement AES in a stream cipher mode.
If you are interested, here are some of the OpenSSL examples:
https://asecuritysite.com/openssl/
Conclusions
It’s a program that refuses to go away. You can run it as an executable, link it with a static library (LIB), or integrate it with a dynamic library (DLL). It runs on Windows, Mac or Linux, and it is generally fast and should always give the correct results. It is thus the program that professionals would turn to, to see the truth, and make sure their systems are giving the right output. But, basically, it is also a program that provides the core foundation of security on the Internet. For your privacy and security, thank OpenSSL.