EU Green Passport System Breach … A Large Scale Leak of Private Keys or A Human Trust Breakdown?
EU Green Passport System Breach … A Large Scale Leak of Private Keys or A Human Trust Breakdown?
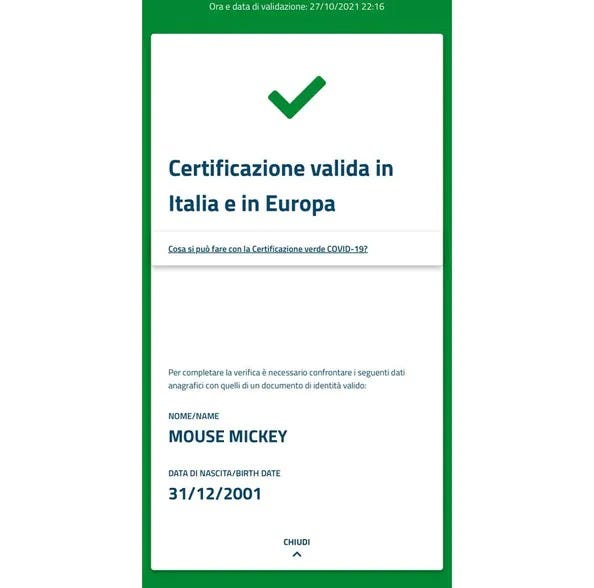
Well, it had to happen. Last week it was reported that Adolf Hitler and Mickey Mouse could prove their vaccination status with valid EU’s Green Pass vaccine passports. Unless the EU Commission find the root of this compromise, the whole of the EU Green Pass vaccination identity system could collapse, and thus our first major attempt at building a more trusted health care world across our borders will fail.
The magic of the private key
To give you an understanding of how these passports are created, each trusted authority in each country will a set of private and a public keys (they should use more than one, in case they have to revoke some of them). A single signing key pair would cause major problems, as a single like of this key, would mean that all of the passports signed within that country would be revoked.
The vaccine status passport is signed by the private key and proven with the associated public key. This digital signature on the passport proves both its contents and its validity (or trustworthiness of the passport). When the passport is checked, it is then checked against a set of trusted public keys. These public keys can be stored centrally by each country, or by the EU Commission. At a border check, the Validator App will have access to all of the trusted public keys.
When a private key has been found to have been leaked, the associated public key will be marked as untrusted and will be revoked. Anyone with a passport signed with this private key will then be marked as being invalid. A major compromise of these private keys would thus bring the whole infrastructure down, and allow fake passports to be trusted. Many trusted passports would then be untrusted, and cause difficulties for travellers. In terms of signatures, the passports normally use EdDSA, and which is fairly free of the weaknesses associated with ECDSA.
An overview of the processing is defined in [1] as [here]:

First we start with the basic data for the vaccine status report [here]:
{
"1": "GB",
"4": 1992212161,
"6": 1425632973,
"-260": {
"1": {
"v": [
{
"ci": "URN:UVCI:01:GB:D23AD1B216A11133B272BEA32C426AC0#D",
"co": "GB",
"dn": 1,
"dt": "2021-01-14",
"is": "NHS Anywhere",
"ma": "ORG-110302699",
"mp": "EU/1/21/1529",
"sd": 2,
"tg": "341534114",
"vp": "3339315014"
}
],
"dob": "1977-01-10",
"nam": {
"fn": "SMITH",
"gn": "FRED SMITH",
"fnt": "SMITH",
"gnt": "FRED SMITH"
},
"ver": "1.3.0"
}
}This contains the date of birth of the person, their name, and the details of their vaccination. To then encode this into the QR, we create a signed object. In this following case this is an EdDSA signature signed by a private key (such as from the NHS). The library used is COSE [here]:
message='{"1": "GB","4": 1772210913,"6": 1830374921,"-260": { "1": {"v": [ {\"ci": \"URN:UVCI:01:GB:D36AF2C745B94400A176CF3E3B526BA#F","co": "GB","dn": 1,"dt": "2021-04-11","is": "NHS","ma": "ORG-100331689","mp": "EU/1/21/1529","sd": 2,"tg": "840539006","vp": "1119305005"}],"dob": "1977-01-04","nam": {"fn": "SMITH","gn": "FRED SMITH","fnt": "SMITH","gnt": "FRED SMITH"},"ver": "1.3.0"}}}'The code is [here]:
import zlib
import base45
from cose.messages import CoseMessage
from binascii import unhexlify, hexlify
from cose.messages import Sign1Message
from cose.keys import CoseKey
from cose.headers import Algorithm, KID
from cose.algorithms import EdDSA
from cose.keys.curves import Ed25519
from cose.keys.keyparam import KpKty, OKPKpD, OKPKpX, KpKeyOps, OKPKpCurve
from cose.keys.keytype import KtyOKP
from cose.keys.keyops import SignOp, VerifyOp
msg = Sign1Message(phdr = {Algorithm: EdDSA, KID: b'kid2'},payload = message.encode())
cose_key = {KpKty: KtyOKP,OKPKpCurve: Ed25519,KpKeyOps: [SignOp, VerifyOp],OKPKpD: unhexlify(b'9d61b19deffd5a60ba844af492ec2cc44449c5697b326919703bac031cae7f60'),OKPKpX: unhexlify(b'd75a980182b10ab7d54bfed3c964073a0ee172f3daa62325af021a68f707511a')}
cose_key = CoseKey.from_dict(cose_key)
msg.key = cose_key
en = msg.encode(tag=True,sign=True)
After this we compress with zlib, and then encode with Base-45:
compressed = zlib.compress(en)
encoded = base45.b45encode(compressed)
print ("Code: ",encoded.decode())
This then gives us the code for the QR code. In this case it is:
6BFX A0087I0ZQ2M95*7DF.4 4JUZ1U0OC0OL-5RO3E9VR/BVBKBPD*62: D*OH+$2$XEU-RI7A18PFNH-:DVN7 VJWBKB%JHBWN.D0-D2$4NV23QIH6O+P9N*SR:4*O3+:TH%D4R9H7D-%MIQ4OWDNTC6D261HBHQ445L52GG48TLY4QDEBYAK194L/STCA7M1KR61P8DSHW069.QN-G3 MHBJV.CI588 STC55J22Z9M2H%41R10REKDRI M9XAP8%ROZHKIA6*L5JNDU2JUII5LNV0MF7PI7RR35WT Y9E*SE:NV%LKHJ *8I40SDIA+G2X6EXQ.53/65.GQTG13M9%OQZPU .QS/DPIPG30$RIR226V8GCO566H7OK0PM+IIG15QQWKP9FM3ZN0XFIY9+2I09LXSMKOIE/0KSJ29LV%5LUL4BW:+B-J6RWPIEDL.RPO0CZ2CVSQAWIIVAETH3T 49E3YOREXJ.0P7FV5Z88DWXKUJWVRGD2T36MB5RAHYUQUL712W6S3Y9Z-TC4VY5SYTBGS361S6XR%AB.WVVFS++F
We then add “HC1:” to the string, and this is then simply written as a QR code. To decode we read the QR code data, and then decode the Base-45, decompress, and check the signature:
decoded = base45.b45decode(encoded.decode())
# decompress using zlib
decompressed = zlib.decompress(decoded)
cos = CoseMessage.decode(decompressed)
cos.key = cose_key
print ("Signature: ",cos.verify_signature())
print (cos.payload.decode())
A leak of the keys or human trust issues?
So while the EU Commission investigate the case, we need to understand if this was a large scale breach of the digital signing infrastructure or a breach of trust by those associated with generating the passports. We can basically dismiss flaws in the digital signing process, as the methods used are the same that we have with digital certificates, and they are safe. There are no current major weaknesses with the EdDSA signing method, and the strength of the keys used means that all the computing power in the world — and a trillion times more — would not break a single signature. And so, it’s either a data leak of the private keys or it's an insider job.
At the core of this is the protection of the private key, and which should have ultra-strong protection and should not even be accessed by insiders within certificate signing authority. The nightmare scenario is that breaches of the private keys could bring down the whole of the green passport infrastructure.
The strange element of this breach is that multiple countries are reporting that there may have been compromised. This includes reports from France, Germany, Italy, Netherlands, North Macedonia, and Poland. France and Poland have especially been pinpointed as being possible sources of fake certificates. There have also been reports that private keys used for the signing of these certificates have been circulating on the Dark Web.
Because of reports across different nations, it is likely to have not been from the leak of the private keys, and that the certificates have been generated by people with valid credentials within the IT system of issuing authorities. People being people often like to play around with the system, and generate some fake certificates. This could be to test their system, or where they want to commit fraud. In this case, perhaps we are seeing test certificates from the IT teams involved, and which have leaked out. But another scenario is that these signed certificates would be worth a great deal of money, and could be sold around the world for those who might want to travel into the EU. Anyone looking to make money, could have found a way to generate certificates that might be sold on to others — an ‘inside job’.
Conclusions
A breach of the methods used in digital signing can be dismissed, as any weakness in that would cause problems with our PKI infrastructure, blockchain and with cryptocurrencies. For the breach of the private keys across different countries, it is possibly unlikely, unless these keys have been stored in a central place. The most likely source is likely to be … humans. When a developer is asked to produce a test certificate they are more likely to turn to Mickey Mouse than to an auditable test account. For some, it will seem more like a ‘little joke’. In conclusion, I hope in each country there is a strong implementation of a trust infrastructure, as the whole infrastructure for green vaccine passports could fall like a house of cards.
If you are interested, here are how the passports are created:
Well, we now live in a strange world. Our world has been damaged over the past 18 months, and, for the sake of our next…billatnapier.medium.com
or: