One of the Greatest Cybersecurity Challenge in the Next Decade … Post Quantum Cryptography

One of the Greatest Cybersecurity Challenges in the Next Decade … Post Quantum Cryptography
And, so our current public key encryption methods will be gently (or forceably, in some cases) be removed over the next decade or so. It will so changes to Web browsers, encryption methods, key exchange, digital signature, and so much more. Organisations thus need to think deeply about there migtration, and seek all the areas that involve our current public encryption methods. We will thus say goodbye to our fix on RSA, ECC (Elliptic Curve Cryptography) and Discrete Logs (such as the Diffie Hellman method). Out will go ECDH for handshaking, RSA/ECC for encryption, and ECDSA and EdDSA for digital signing, and in will come the PQCs (Post Quantum Cryptography) methods.
The are two main areas that will be developed:
- KEM (Key Encapsulation Method)/Public Key. This will replace ECDH and our public key encryption methods.
- Digital Signing. This will replace ECDSA and EdDSA.
KEM/Public Key
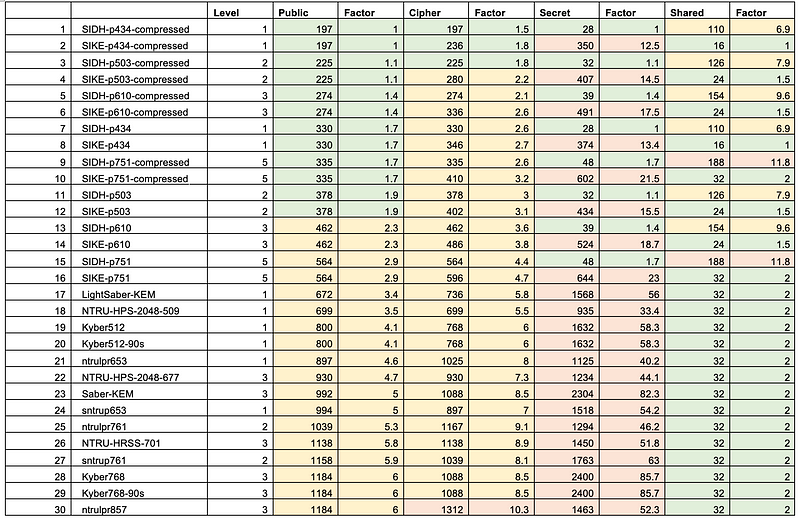
And, so, rather than get into all the detail, I have analysed the current contenders for KEM. For this I ran a test on a Linux machine, and gained the results for key generation, key encapsulation (Bob creates the key and encapsulates it for Alice), and key decapsulation (Alice reveals with key). I have colour coded the results of the factor of increase in the number of cycles taken to perform the task. Green is x1-x2, yellow is x2-x10, light orange is x10-x100, orange is x100-x100, and dark orange is over 100:


The league table is then:

We can see that the lattice methods of Kyber, NTRU and Saber generally win, with Kyber generally performing well. While McEliece (code-based) struggles with key generation it improves on the encapsulation and decapsulation parts. Isogenies, though, struggle in most areas.
For key and cipher sizes we get:

More details here:
https://asecuritysite.com/pqc/pqc_kem
Digital Signatures
For digital signatures, I have analysed key generation, signing and verification. We see the Hash/ZKP method of Picnic does well with the key generation, but struggles in other areas. Kyber and Dilithium generally to well, and gains the highest scores, with Dilihium generally doing best. The hash-based methods of SPHINC+ and the Multivariate Quadratic method of Rainbow, struggle in most areas:
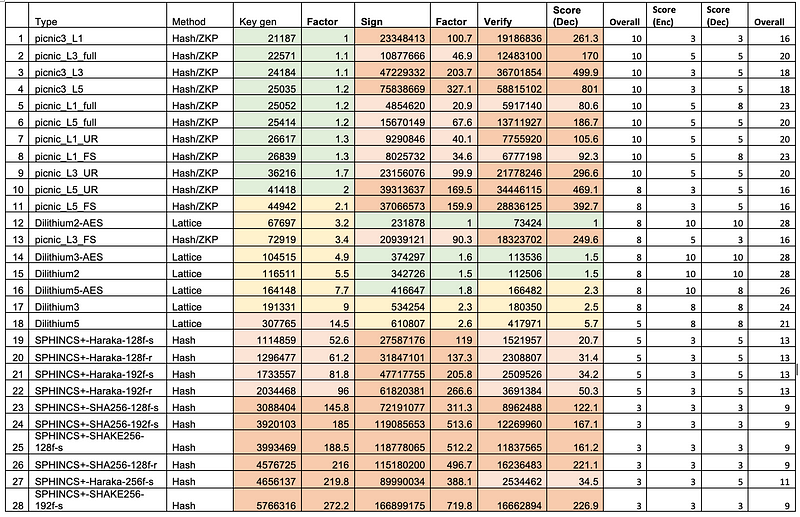


In this case we see that Rainbow and SPHINCs+ are poor overall compared with Dilithium, Saber and Picnic. The league table is:

And for key and signature sizes:
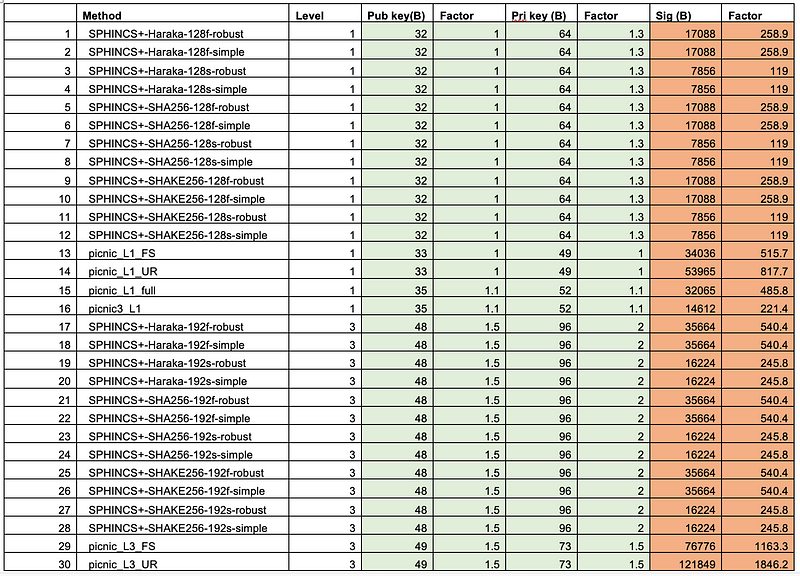
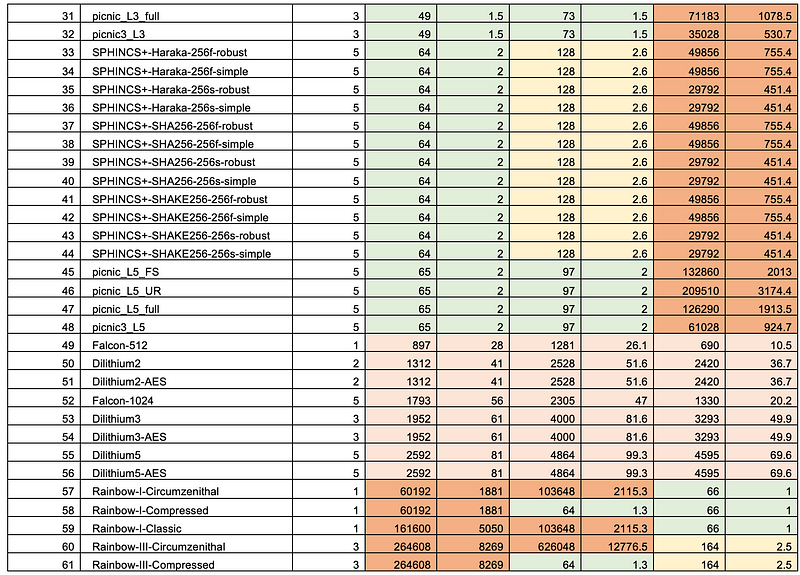

More details here: