Why Aren’t We All Using FIDO2 For Corporate Systems?

Why Aren’t We All Using FIDO2 For Corporate Systems?
With my Macbook, I use my fingerprint to log in, and I now increasingly use my watch to authenticate me. For my banking app, I use face recognition, and to pay for my purchases, I now typically use my watch to authorize the payment. We are thus moving towards a world where we get rid of passwords — or basically a single way to authenicate us. This is especially the case where we are being told that we need increasingly complex passwords, and where a simple PIN and a wearable device is so much more secure than a password. But, still, as employees, we log into our corporate systems using the good old username and password.
Unfortunately, as long as one person fails for a phishing attack, we leave our corporate systems open to stolen user credentials. But, in the future, could we use something we wear, or something we have, or even our face or fingerprint, could be a standard part of logging into our corporate networks?
Protecting against phishing attacks on corporate systems
And, so, this week, Cloudflare announced that they had rolled out a FIDO2 authenticator for their employees, and which allows users to login into internal and external systems using a software secured key as a secondary factor [here]:

This is part of their roll-out of a FIDO2 implementation and which aims to produce phishing proof Web sites. In many existing implementations of Multi-factor Authentication (MTA) we often use Google Authenticator as a secondary factor. Unfortunately, this method is flawed as the access token that is generated can be captured by an intruder c and then play it back into trusted systems and gain access.
FIDO2 takes a different approach to MTA, and where we can implement a range of second-factor authentication methods, including biometrics, PIN codes and hardware tokens. With this, a user could have a wearable device that authenticates them to a Web site, or where they can present their fingerprint.
Cloudflare used Cloudflare Access to implement the FIDO2 integration [here]:
resource "cloudflare_access_policy" "prod_cloudflare_users" {
application_id = cloudflare_access_application.prod_sandbox_access_application.id
zone_id = cloudflare_zone.prod_sandbox.id
name = "Allow "
decision = "allow"
include {
email_domain = ["cloudflare.com"]
okta {
# Require membership in Sandbox group
name = ["ACL-ACCESS-sandbox"]
identity_provider_id = cloudflare_access_identity_provider.okta_prod.id
}
}
# Require a security key
require {
auth_method = "swk"
}
}The “require” element makes sure that all Cloudflare employees log into ACCESS applications, and where “swk” defines the proof of a software-secured key.
What’s FIDO2?
FIFO supports a standardization of second-factor authentication and an integration framework, along with client authenticators. This specification is known as FIDO2. Each of the methods uses public-key encryption in order to defend against phishing. Overall FIDO2 is passwordless and allows one or more client authentication methods including embedded ones (biometrics and PIN codes) and external ones (FIDO security keys, wearable devices, and mobile phones), as illustrated in Figure 1.

The integration includes:
- W3C WebAuthn. This integrates into compatible browsers.
- CTAP2. This allows for the integration into smartphones using USB, NFC and BLE connections into browsers.
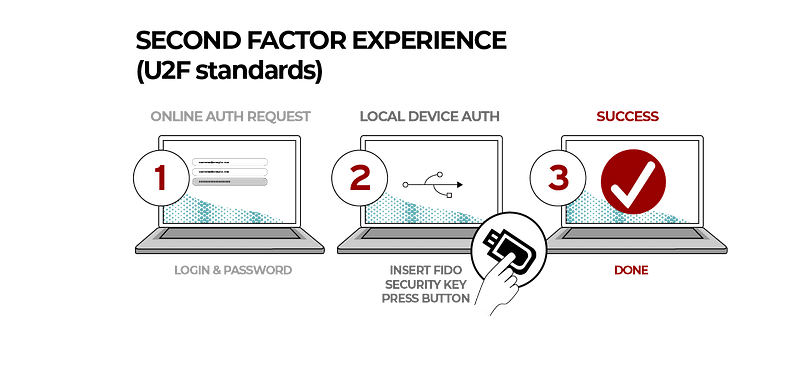
- CTAP1 (previously named U2F — Universal Second Factor). This allows integration with security keys and wearables using USB, NFC and BLE connections into browsers. An example of this is shown in Figure 2.
Conclusions
Passwords should be history by now, but still, we hang onto our old ways. The future is proper MFA, and FIDO2 provides us with a framework to integrate many of the existing authentication methods. We really should be using MFA in our corporate systems, and Cloudflare shows a vision of the future. While we still blinding use the flawed OAuth2 methods, we need to move towards something that integrates the human into the whole authentication infrastructure. To use CAPTCHA and passwords, just seems so silly, as they are still open to phishing attacks. FIDO2 uses public key encryption, and which significantly increases the trustworthiness of the overall infrastructure.
If you want to support Asecuritysite.com — which is free to use and has no adverts — and also get access to all the articles on “Asecuritysite: When Bob Met Alice” consider subscribing here: