The Crazy World of Passwords: To “@” or to “!”

The Crazy World of Passwords: To “@” or to “!”
I did an open day at my university on Saturday, and part of this was a fun Mentimeter test on passwords. As with every talk I have given on this, the majority used a single upper case character, put the number at the end, and used “!” or “@” in their password. The usage of this type of approach is well known to tools such as Hashcat, and where rules can be set up to take standard dictionary words and add them together, while making the first character uppercase and adding a numeric value, and “@” or “!” to the end of the password.
So, some day, soon, we have to realise that passwords are just a legacy from a time of mainframe computers and that we need to find better ways to authenticate ourselves. Now a new paper reveals just how we use our passwords on public and private wifi [here]:

The research has analysed around one million passwords taken from public wifi hotspots, and compared them to the passwords used in the China Software Developer Network (CSDN) [here], LinkedIn and Yahoo! Voices data breaches:

We can see that while the LinkedIn and Yahoo! Voices password list typically had characters, users within wifi hotspots tended to go for numeric values for their passwords, with a common sequence of a count up, or a single-digit repeated. In fact, over 40% of the characters in the wifi and CSDN passwords were all numeric ones, as opposed to less than 10% for the LinkedIn and Yahoo! Voices data breach:

On a public wifi network, possiblu “12345..” is the quickest to setup, and remember. This approach is highlighted in the structure of the password, and where we identify a digit with a ‘D’, a lowercase letter with an ‘L’, and an uppercase letter with ‘U’. In the public wifi passwords, we see the top three passwords all had numeric values, and many of the other top ones were purely lowercase letters:

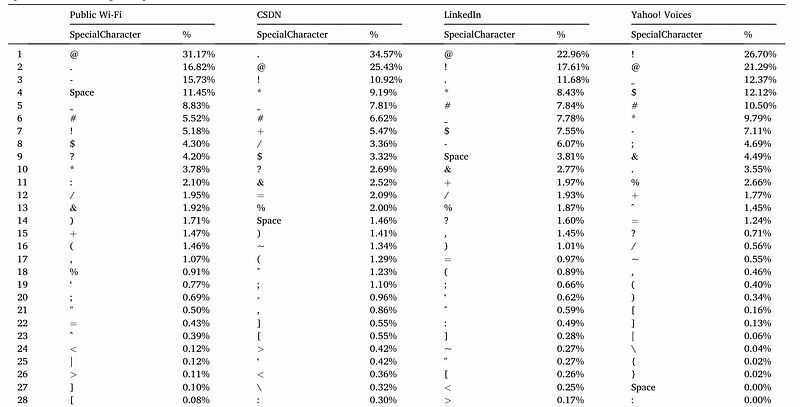
When it came to special characters, the ‘@’ proves popular in all breaches, along with the ‘!’. These are popular as they are typically the first two characters that appear from the left-hand side of the keyboard or keypad. Users often typically select these for their passwords, as they are easy to remember. A full stop is also fairly common, with brackets and braces hardly registering for their popularity:
The most popular passwords varied within different regions of the world, and with placenames being popular in Turkey (such as “istanbul”, and “galatasaray”), and names in Egypt (such as “ahmed” and “omar”):

Public or private?
In order to understand how public wifi differs from setting passwords on private wifi, the researchers conducted a survey and found that numeric values were still the most popular, and where alphanumeric and numeric passwords were almost equally probable. The percentage of passwords using special characters certainly increased to over 46%, and perhaps showed password policy restrictions on private wifi systems:
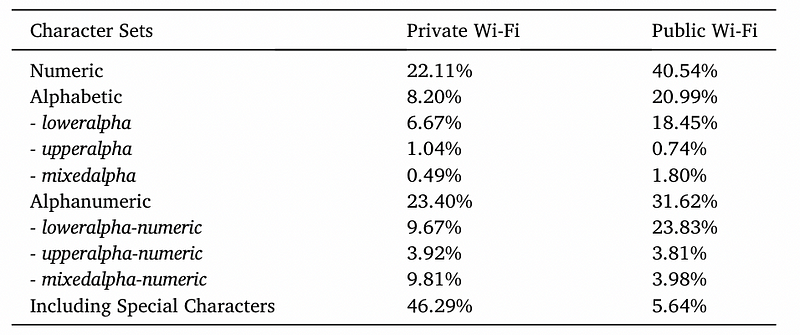
While the usage of “@” was strong in the public wi-fi dataset, it is “!” that is the most popular on private wifi. This is likely to be because the “@” symbol is easy to access on a mobile phone, but on private networks, the user is likely to be setting the password with a keyboard:

When we set passwords on public wifi systems we often go for fairly simple passwords, as we know we will only need it for a short time, while we are often required to set longer passwords for private wifi networks. The password policy on public wifi systems can also be weaker than on private wifi. This approach is shown and where an eight-character password is the most popular on public wifi system, whereas a 10-character password is the most popular on private wifi:

Conclusions
Like it or not, we are human, and we have human failings. The datasets for public wifi and the other data breaches covered are rather old now, but give some insights into the way that users set more public facing passwords and the weak security policies they have. There is more of an insight within the private wifi settings, and where users often have to setup stronger passwords.