Blinding ECDSA

Blinding ECDSA
Like it or not, ECDSA is the King of the Hill when it comes to Bitcoin and Ethereum, and is the core of its trust infrastructure. While it is not quite as scalable as methods such as EdDSA, it is possible to implement a range of privacy-preserving methods with a little bit of modification in the creation of the signature. Before we start, let’s have a quick look at how ECDSA works.
Basics of ECDSA
Overall, with an ECDSA signature, Alice signs the hash of a message (h(M)) with her private key (sk), and Bob checks it with her public key (Pk). With ECDA, Alice produces a private key (sk) and a public key (Pk):

We then take a hash of a message:

Alice then creates a random value of k, and produces:

and where r is the x coordinate value of k.G (mod n). The s value is then:

When Bob checks the signature, he computes:

and:

Bob then computes a point at:

If the value of x co-ordinate of Z is equal to r, the signature checks out. In this case, n is the order of the curve.
Blinded ECDSA
With a blinded signature, Bob can sign for a message, without knowing what the message is. In this case, Alice will create a blinded ECDSA signature, and where Bob can then sign it, and then Alice can unblind it. The method is based on the one produced by Oleg Andreev for blinding signatures in Bitcoin.
First, Alice produces four random values of a, b, c and d, and Bob produces two random values of p and q and then computes:

and:

and where G is the base point on the curve. Bob sends these to Alice. Next, Alice computes:

and public key of:

Alice computes a hash of message (M):
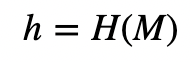
Alice then blinds with:

and send this to Bob. Bob signs the blinded hash and returns with:

Alice unblinds her signature:

The signature is now r=K_x, s=s2.
The proof is here:

Coding
The coding is [here]:
and a sample run [here]:
m=46398016479029616968153310998590589859317634753915956549813904092937392557159
a=3303670661
b=3226384361
c=3530828149
d=3607703383
Public Key Tx=75232732142229191477159812086310547165062017290843364912683578530970424703230
Ty=73950523097040244239776555774732425845079447152113985190585097252768983601069
Hash h=53060989786633559228535141356889483919385714906876242047763586659314070909566
Blinded Signature r=94046861866238546923597525972649788516701559058765278594626970725249113708126, s=103442503972324084972377390983720274585365710753545239530321864819095340728763
Signature r=94046861866238546923597525972649788516701559058765278594626970725249113708126, s=35825078730317479356116975137038450525621519055620748195720062041695485378112
Signature verified: true
And we can see the signature checks out. The running code is here: