Goodbye Passwords (Finally!) …. Here’s To The Future With Passkeys and Privacy Pass

Goodbye Passwords (Finally!) …. Here’s To The Future With Passkeys and Privacy Pass
What’s still the most popular attack vector for cyber attacks? … it’s spear phishing, and normally involves the capture of a user’s password. Passwords are now just too much of a threat to our digital world, along with them not scaling to mobile devices.
For Cybersecurity professionals this has been a big week, and the start of building a new digital world. At Apple’s developer conference, there were no new iPads, or major changes to their hardware, but there were significant changes to the way that the Apple ecosystem will work.
As a Mac user, I think the ecosystem for trust and security has always been much better than Microsft Windows and Andriod. And the new changes to iOS 16 and macOS Ventura, will it truly start to rid our digital world of passwords and CAPTCHA, and move toward toward multi-factor authentication methods (MFA). To me, to use a PIN code and my fingerprint is almost infinitely better than a password — both from a security and a useability point of view.
Privacy Pass and Passkey
The two main announcements for cybersecurity professions were Privacy Pass (a way of authenticating users, devices and applications without the usage of CAPTCHA) and Passkeys (a way to integrate Multifactor Authentication — MFA). If you are interested in learning about the work of Cloudflare and Apple on Privacy Pass, try here:
In the UK, we need to provide “anti-money laundering” evidence, and which involves you providing a utility bill to a…medium.com
For Passkey, we see the usage of integrating FIDO 2 to create a multifactor authentication infrastructure than can use fingers, face recognition, tokens, and many other methods to authenticate users without the use of passwords. Anyone with a smartphone will know how annoying it can be to enter passwords onto a phone. The main move is likely to be that users will not require a login with a password anymore, and might authenticate with their face on a smartphone, or even with a wearable device. This authentication will then be synced across a user’s devices using iCloud’s Keychain so that the same biometric can be used on multiple devices. In terms of privacy, Apple uses an end-to-end encryption method to make sure that biometric information is kept private.
While Apple holds a great deal of power in the industry, it knows it needs to fit in with a standard that scales across the whole industry, and thus is adopting the standards developed in the FIDO Alliance. The greatest change in the movement of the FIDO Alliance has been to share cryptographic keys across a range of systems and devices. This has now been solved with passkeys — aka multi-device FIDO credentials. This new standard will not be supported by Apple, Microsoft and Google, and thus will scale to both mobile devices (iOS and Android) and desktops (macOS and Windows). In fact, Microsoft have dropped passwords, and Google is moving towards having no passwords on their systems.
But, there are still some questions to be answered, especially due to vendor lock-in, such as where someone wants to move the cryptographic keys from Android to iOS.
FIDO2
FIDO2 provides a standardized approach to MFA (Multi-factor Authentication) and 2FA (Two-factor Authentication) and is supported by the FIDO Alliance and the W3C. It is now supported by most Web browsers and aims at creating a passwordless authentication method. In a study by Lyastani et al [1], it was found that many users find it acceptable to replace passwords with a security key for authentication. But there are still worries about the usage of the technology, especially in losing the authenticator and being locked out of accounts. But, these concerns can easily be overcome with easy setups and fall-back procedures.
FIDO supports the standardization of second-factor authentication and an integration framework, along with client authenticators. This specification is known as FIDO2. Each of the methods uses public-key encryption in order to defend against threats such as phishing and credential harvesting. Overall FIDO2 is passwordless and allows one or more client authentication methods including embedded ones (biometrics and PIN codes) and external ones (FIDO security keys, wearable devices, and mobile phones), as illustrated in Figure 1.
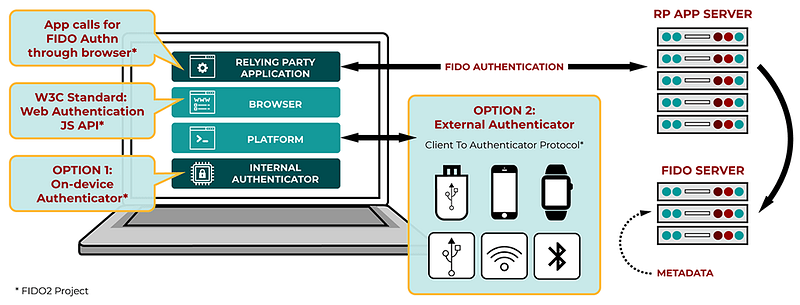
Figure 1: FIDO2 [here]
The integration includes:
- W3C WebAuthn. This integrates into compatible browsers.
- CTAP2. This allows for the integration into smartphones using USB, NFC and BLE connections into browsers.
- CTAP1 (previously named U2F — Universal Second Factor). This allows integration with security keys and wearables using USB, NFC and BLE connections into browsers. An example of this is shown in Figure 2.
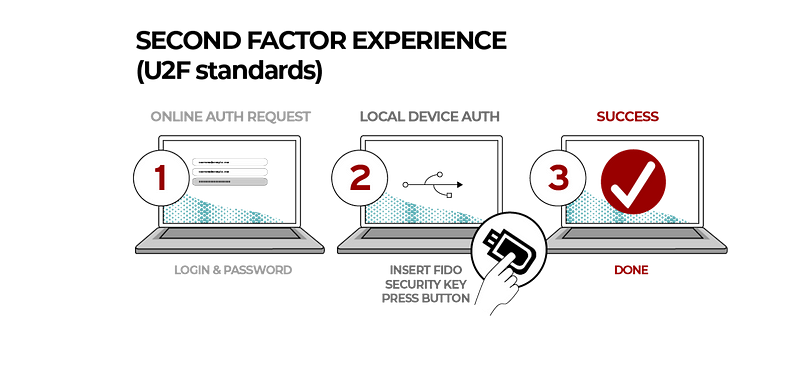
Figure 2: [here]
YubiKey
One of the widely used FIDO2 devices for authentication is the YubiKey. Reynolds et al [2] reported on the usage of the YubiKey for Universal 2nd Factor (U2F) security, and where users must press a button on a YubiKey to authenticate themselves. For this, they set up the login to Microsoft Windows, Google and Facebook accounts, but reveal problems with the usage of the devices, including lock-outs. These problems are often related to the basic setup of the device. Within a second study, the researchers found that users generally enjoyed using the YubiKey for daily tasks, and provided advice on improving the setup process. For Arcana, there are generally two ways that their product could use FIDO2 devices. The first is to authenticate the device to a service, and the second is to use the device to encrypt the user’s key.
Signing data
Within digital signing, a server (or service) can generate a data challenge and then get the YubiKey to create a digital signature using the private key stored on the device. This signature can then be proven with a public key and is illustrated in Figure 1. In this way, the server can store the public key of the device, and then match this to a user, when the user wants to log into the system, they will need to provide a valid signature that matches their public key.

Figure 3: Authenticating with signatures
Encrypting data
Along with the YubiKey signing for data with its private key, it is also possible to use it as a method to encrypt and decrypt data. As shown in Figure 2, we can generate a key pair and then upload the private key onto the YubiKey. This can then be linked to an encryption process. In this case, it is linked to the GPG process, and where we can sign email messages with Bob’s private key, and which will then be proven with Bob’s public key. Along with this, we can decrypt ciphered email using the device, and which involves using the private key to decrypt the message.
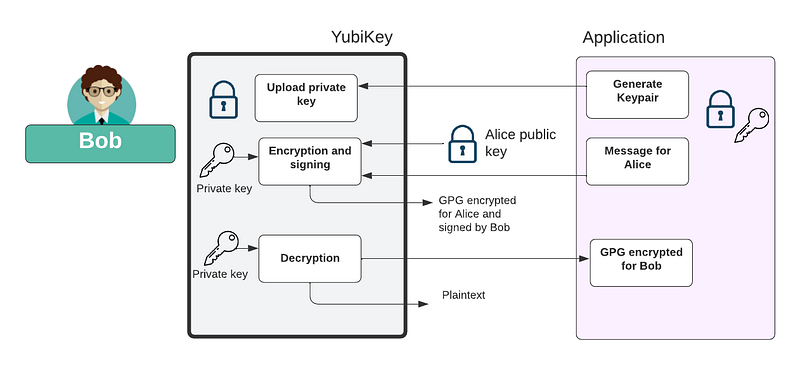
Figure 4: Encrypting and signing
Conclusions
There is still work to be done on Passkey, but within the next few years, the idea of passwords will fade into the past. They came from a world of mainframes, and now need to be retired as the only form of authentication.
References
[1] Lyastani, S. G., Schilling, M., Neumayr, M., Backes, M., & Bugiel, S. (2020, May). Is FIDO2 the Kingslayer of User Authentication? A Comparative Usability Study of FIDO2 Passwordless Authentication. In IEEE Symposium on Security and Privacy (pp. 268–285).
[2] Reynolds, J., Smith, T., Reese, K., Dickinson, L., Ruoti, S., & Seamons, K. (2018, May). A tale of two studies: The best and worst of yubikey usability. In 2018 IEEE Symposium on Security and Privacy (SP) (pp. 872–888). IEEE.