Cybersecurity: Hard/Soft Skills, MSc or Degree, Specialist or Generalist?

Cybersecurity: Hard/Soft Skills, MSc or Degree, Specialist or Generalist?
I get continually get asked about the best route that someone can take in developing their career, and my answer is always the same … it all depends on what your focus will be, and what you generally expect. Where do you want to live? What things generally interest you? Where are your gaps? Do you want to continually learn and also learn new things? And so on.
For me, I have chosen cryptography as my specialism, and it was one of the best things I have ever done in my career. The more I learn, the better I get in the area, and the more I practice my art, the better my outputs are. To me, I have a toolbox full of methods and techniques in order to practice my art.
So let’s dive a little bit into the catch-all term of Cybersecurity.
Do salaries relate to qualifications?
This is difficult to qualify, but generally the higher the qualification that someone has in cybersecurity, the higher the average salary will be:

The entry in cybersecurity can be from school, as there is generally no real barrier in getting into the area, especially for those with good technical skills. But, a degree is often a good focus for anyone getting into cybersecurity security and then (perhaps) later gaining an MSc or PhD. Often an MSc can be done while still in work, but a PhD often requires at least three years of study, with only a stipend to cover living costs.
But the longer-term prospects of having an MSc and/or PhD will generally pay back the commitment. Say this, though, hands-on and practical experience is also key to re-enforcing academic skills with practical ones. Someone with a PhD, and without any real practical skills will struggle to be matched against a range of job roles and will possibly take too much effort in training up. It is thus important that practical skills are gained while studying.
Does experience matter?
Luckily, these days, many jobs do not mention the number of years of experience that you have to be considered for a job, as it is not a guarantee that someone can actually do a certain job. Just because you have spent 10 years learning to code in Java, doesn’t actually mean you are guaranteed to be good at coding, as someone who has a natural talent for it, and who is just starting their career. But, it’s likely that you’ve picked up the skills and experience that are required to master topics. And, so, salary prospects generally increase through the years of experience that someone has:

Is specialising good?
It all depends if you want to be more general in your approach, and where you know many areas in reasonable detail, or want to develop an in-depth approach. At the extremes, it is wide subject knowledge and thin in depth, or narrow subject knowledge, with depth. There are many different combinations in-between.
In my area, the demand for those with cryptography skills is extremely high, and the salaries are also some of the best around in information technology. Generally, with the chance of remote working, the opportunities for those with in-depth skills have never been higher, and I am continually approached by companies around the world looking for graduates with cryptography skills — but they are generally looking for specialists and not generalists in the area.
While it can be costly in terms of the time in the time it takes to learn cryptography — and some would say it can never be fully learnt — the time invested certainly pays off in the end with an average salary for a cryptographer varing from $149K (ZipRecruiter) to $98K (Payscale), with some even putting the entry-level post around $100K. At the top end, those with in-depth cryptography skills can gain a $200K annual salary.
As with most areas of cybersececurity, there is often a balance between soft skills and hard skills. On the hard skills side, for cryptography, it is generally around software development, maths, and knowledge of encryption. But on the soft skills side, its all about communication, problem solving and collaboration:

If you are interested in getting into the area, try here.
While the hard skills will vary from area to area, the soft skills defined for the cryptography area, could be easily applied to many other specialist areas. I highly recommend this talk for those interested in Security Operation Centre roles, and in defining hard/soft skills:
How many jobs are there?
Just like in software development, there are many job titles and roles, and the chances of moving between job roles is generally fairly easy. Often, at a high level, we cna define Dev (Development), Op (Operations) and Sec (Security), and where we can mix and match these.
In fact, the NICE framework for the Cybersecurity workforce defines seven categories; 33 speciality areas; and 52 work roles [here], and these then map these to 1,007 tasks, 374 skills, 630 knowledge areas and 176 abilities.
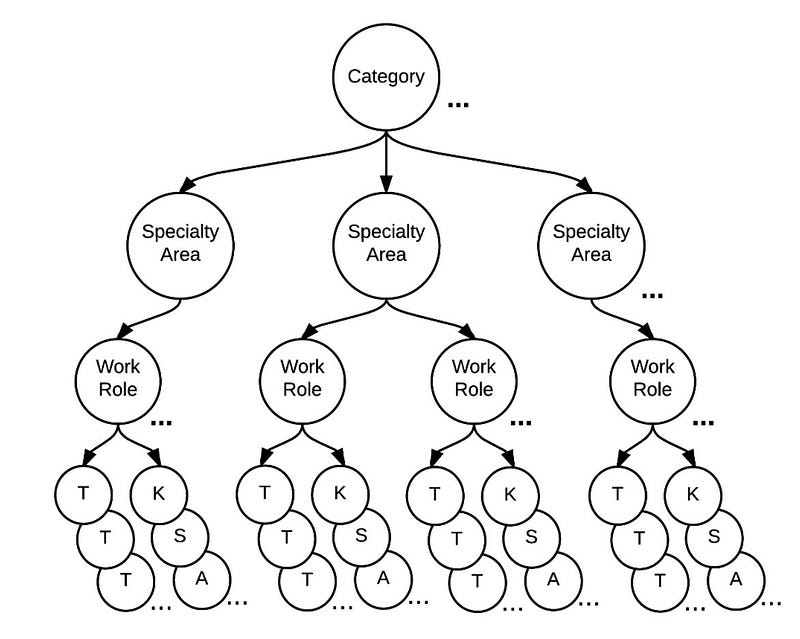
The break-down starts with seven categories and then works these into into speciality areas for the category. Next we break the speciality areas into work roles and then into tasks (T) knowledge areas (K), subject areas (S), and ability (A), that are defined for the work role. The T, K, S and A can then be mapped to specific work roles. With categories and specialist areas they define:
- Securely Provision (SP). Risk Management (RSK); Software Development (DEV); Systems Architecture (ARC); Technology R&D (TRD); Systems Requirements Planning (SRP); Test and Evaluation (TST)
- Operate and Maintain (OM). Data Administration (DTA). Knowledge Management (KMG). Customer Service and Technical Support (STS); Network Services (NET); Systems Administration (ADM); Systems Analysis (ANA)
- Oversee and Govern (OV). Legal Advice and Advocacy (LGA); Training, Education, and Awareness (TEA); Cybersecurity Management (MGT); Strategic Planning and Policy (SPP); Executive Cyber Leadership (EXL); Program/Project Management (PMA) and Acquisition;
- Protect and Defend (PR). Cybersecurity Defense Analysis (CDA); Cybersecurity Defense Infrastructure Support (INF); Incident Response (CIR); Vulnerability Assessment and Management (VAM)
- Analyze (AN). Threat Analysis (TWA); Exploitation Analysis (EXP); All-Source Analysis (ASA); Targets (TGT); Language Analysis (LNG).
- Collect and Operate (CO). Collection Operations (CLO); Cyber Operational Planning (OPL); Cyber Operations (OPS).
- Investigate (IN). Cyber Investigation (INV); Digital Forensics (FOR).
Within the job function, we obviously mix and match to the role. For example, an Incident Responder would be involved within the categories of Investigate (IN), Analyze (AN), and Collect and Operate (CO), and have specialist areas for Cyber Investigation (INV), Digital Forensics (FOR), and Cyber Operations (OPS).
Where the proposal truly excels is to then map each of the categories and specialist areas to example job titles. With Security Provision (SP) we get:
- Authorizing Official/Designating Representative. SP-RSK-001
- Security Control Assessor. SP-RSK-002.
- Software Developer. SP-DEV-001.
- Secure Software Assessor. SP-DEV-002.
- Enterprise Architect. SP-ARC-001.
- Security Architect. SP-ARC-002.
And then within each of these roles, they define the tasks that might be involved. There are 1,007 different tasks, of which the first 10 are:
- T0001. Acquire and manage the necessary resources, including leadership support, financial resources, and key security personnel, to support information technology (IT) security goals and objectives and reduce overall organizational risk.
- T0002. Acquire necessary resources, including financial resources, to conduct an effective enterprise continuity of operations program.
- T0003. Advise senior management (e.g., Chief Information Officer [CIO]) on risk levels and security posture.
- T0004. Advise senior management (e.g., CIO) on cost/benefit analysis of information security programs, policies, processes, systems, and elements.
- T0005. Advise appropriate senior leadership or Authorizing Official of changes affecting the organization’s cybersecurity posture.
- T0006. Advocate organization’s official position in legal and legislative proceedings.
- T0007. Analyze and define data requirements and specifications.
- T0008. Analyze and plan for anticipated changes in data capacity requirements.
- T0009. Analyze information to determine, recommend, and plan the development of a new application or modification of an existing application.
- T0010. Analyze organization’s cyber defense policies and configurations and evaluate compliance with regulations and organizational directives.
And to 630 knowledge areas, of which the first 10 are:
- K0001. Knowledge of computer networking concepts and protocols, and network security methodologies.
- K0002. Knowledge of risk management processes (e.g., methods for assessing and mitigating risk).
- K0003. Knowledge of laws, regulations, policies, and ethics as they relate to cybersecurity and privacy.
- K0004. Knowledge of cybersecurity and privacy principles.
- K0005. Knowledge of cyber threats and vulnerabilities.
- K0006. Knowledge of specific operational impacts of cybersecurity lapses.
- K0007. Knowledge of authentication, authorization, and access control methods.
- K0008. Knowledge of applicable business processes and operations of customer organizations.
- K0009. Knowledge of application vulnerabilities.
- K0010. Knowledge of communication methods, principles, and concepts that support the network infrastructure.
And to 374 skills, of which the first 10 are:
- S0001. Skill in conducting vulnerability scans and recognizing vulnerabilities in security systems.
- S0002. Skill in allocating storage capacity in the design of data management systems.
- S0003. Skill of identifying, capturing, containing, and reporting malware.
- S0004. Skill in analyzing network traffic capacity and performance characteristics.
- S0005. Skill in applying and incorporating information technologies into proposed solutions.
- S0006. Skill in applying confidentiality, integrity, and availability principles.
- S0007. Skill in applying host/network access controls (e.g., access control list).
- S0008. Skill in applying organization-specific systems analysis principles and techniques.
- S0009. Skill in assessing the robustness of security systems and designs.
- S0010. Skill in conducting capabilities and requirements analysis.
And to 176 abilities, of which the first 10 are:
- A0001. Ability to identify systemic security issues based on the analysis of vulnerability and configuration data.
- A0002. Ability to match the appropriate knowledge repository technology for a given application or environment.
- A0003. Ability to determine the validity of technology trend data.
- A0004. Ability to develop a curriculum that speaks to the topic at the appropriate level for the target audience.
- A0005. Ability to decrypt digital data collections.
- A0006. Ability to prepare and deliver education and awareness briefings to ensure that systems, network, and data users are aware of and adhere to systems security policies and procedures.
- A0007. Ability to tailor code analysis for application-specific concerns.
- A0008. Ability to apply the methods, standards, and approaches for describing, analyzing, and documenting an organization’s enterprise information technology (IT) architecture (e.g., Open Group Architecture Framework [TOGAF], Department of Defense Architecture Framework [DoDAF], Federal Enterprise Architecture Framework [FEAF]).
- A0009. Ability to apply supply chain risk management standards.
- A0010. Ability to analyze malware.
And then when you think that they just could go any future, they then map these back to roles:

Wow! Finally, someone has mapped the space. So what has 1,007 tasks, 374 skills, 630 knowledge areas, and 176 abilities … that’s how complex an area it is.
Conclusions
In cybersecurity, there’s a job for all.
Go be great …
If you are interested in our MSc, please get in contact. As you can see, it can increase your salary in the long term. We run flexible courses, and you even get the chance to study cryptography: