Hidden Pixels, Click IDs and Other Tricks … Is The Internet Just One Big Spying Network?

Hidden Pixels, Click IDs and Other Tricks … Is The Internet Just One Big Spying Network?
I don’t use Facebook (Meta), and I don’t like visiting a website that obviously has customized adverts for me. There’s something not quite right about private information jumping over browsers and websites. And so a new paper opens up the methods that Facebook have been using to track user activity [here][1]:

Tracking users
Overall, many methods have been developed to detect tracking and try and block users from leaving an activity trail. The methods that advertising companies have used include first and third-party cookies, cookie synchronization, and fingerprinting mechanisms. In the paper, the authors outline that Meta has recently defined a tagging mechanism with a one-time tag (FBCLID — Facebook Click ID). This is then added as a tag for links that go to other websites — a leaving present from the site, and thus allows Meta to track the linkage between the sites (Figure 1).

The research team has shown that this tag can be de-anonymised and reveal the activities of a user, including being about to go back to 2015. They also found that around 1-in-5 web sites are actively using the tagging system and that even a user creating an account today, then Meta could trace their activities as far back as 2015 and continue to track them into the future.
The paper also outlines that a Meta cookie has a lifetime of three months but that these have rolling expiry data, and which allows Meta to track the user for a longer period than three months.
Facebook Pixel
A trick that many advertisers have used in the past is to add a 1x1 pixel graphic to a web page, and which cannot be seen by the user. This is then loaded from a tracking web site, and which can then link someone’s identity to a cookie and thus track them as they move from site to site. For this, in 2013, Facebook introduced Facebook Pixel, and where advertisers could track users across platforms.
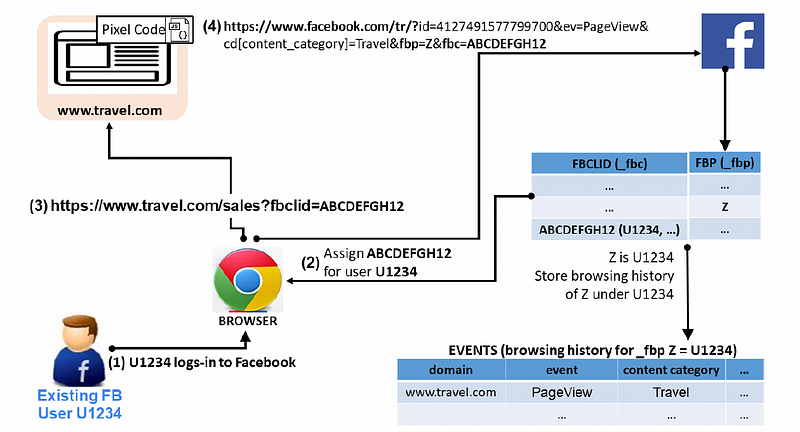
Overall, Facebook managed to track users not only within the Pixel infrastructure but also outside it. The cookies that are used allow third-party cookies to be used that link back to the user’s Facebook ID. This bypasses the anonymisation that is put in place by the browser. As seen in Figure 2, the client website contains the pixel code and which links back to the customer’s Facebook ID using a first-party cookie. Pixel is then used to provide in-depth analytics on the user, such as the amount of time spent on a page.

The paper lists the types of events that Pixel can provide advertisers, including on check-out processes, adding to cart, purchasing, and subscriptions:

So what kind of sites use Facebook Pixel?
The research team found that of the top 10K sites on the Internet (Figure 3), around 23% of the sites were using Facebook Pixel, and that News, Education and Shopping provided a higher than average usage. It should be seen that Government sites and Search Engines had a much lower relative usage of Pixel.

Along with Pixel, FBCLID provides a way of tracking across sites. An example tag shows the FBCLID:
https://www.ncbi.nlm.nih.gov/pmc/articles/PMC5678212/?fbclid= IwAR0J2ueFwGP2ZSIznw04PQEFAbkMDue3T9YSg6
In Figure 5, we see an example of a user logging into Facebook and then leave the site with an FBCLID, and which can then be linked to the third-party site.
The full paper is here:
Over the past years, advertisement companies have used a variety of tracking methods to persistently track users across…arxiv.org
Conclusions
Many services on the Internet are free, but every user pays for this by releasing their data.
Reference
[1] Paschalis Bekos, Panagiotis Papadopoulos, Evangelos P. Markatos, Nicolas Kourtellis, The Hitchhiker’s Guide to Facebook Web Tracking with Invisible Pixels and Click IDs, https://arxiv.org/abs/2208.00710.