Did You Know An Electrical Vehicle Can Be Hacked, Through A Charging Session?

Did You Know An Electrical Vehicle Can Be Hacked, Through A Charging Session?
The rise of the electric vehicle (EV) will see massive growth in the provision of charging points. This has led to the creation of private and public electrical vehicle support equipment (EVSE). If not designed and/or implemented correctly, there could be many potential vulnerabilities which could leave the infrastructure open to a wide range of threats. This includes the charging points and the infrastructure that supports them. And, so, a relatively new paper now documents some of the more recent vulnerabilities that have been uncovered and also outlines possible defences [1]:

Overall, EVSE aims to provide charging points for EVs, and then link these into a vendor or operator cloud network. This then links back to the owner/operator through cloud-based services and to grid operators (Figure 1).

The OpenADR protocol, for example, provides a smart grid infrastructure and where the supply of electricity meets the demand. For OCPP (Open Charge Point Protocol) we have a protocol to set up and manage charging stations — along with handling transactions related to charging. This includes the usage of client-side certificates for mutual authentication and the usage of TLS tunnels. An important standard is the usage of ISO 15118, and where the vehicle and the charging system identify each other using an exchange of digital certificates.
The system used is often defined as Combined Charging System (CSS), and it varies per region of the world. This includes CCS Combo 1 (for US vehicles) and CCS Combo 2 (for EU vehicles), and the plug interfaces are shown in Figure 2 [2].
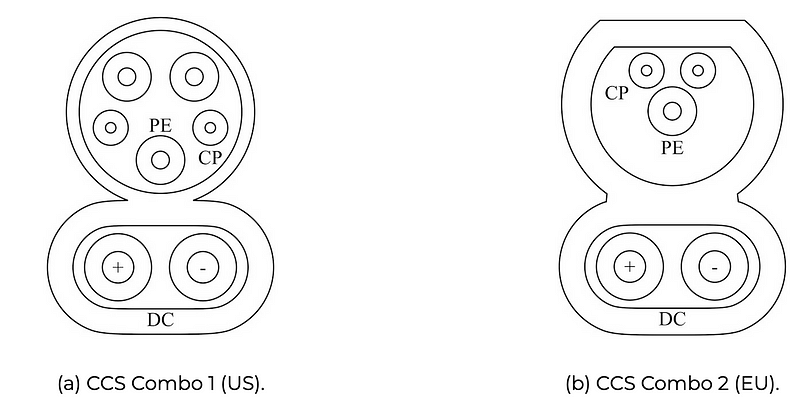
Overall, ISO 15118 provides a full network stack from HomePlug GreenPHY at the Physical layer to OCPP at the application layer (Figure 3). This stack thus supports the connection of the charging system to be connected to the Internet. The plug integrates powerline communication (PLC) using the Control Pilot (CP) and Protective Earth (PE) connection.

Figure 3 outlines the setup of encrypted communications and where encryption can be set up at the Physical layer, the Transport layer (as with TLS) or the Application Layer. With Physical layer encryption, there is a shared secret key — defined as a Network Membership Key (NMK) — and a set of ephemeral Network Encryption Keys (NEKs). The NEKs are rotated on a periodic basis. The Physical layer traffic is then encrypted with the current NEK and implemented with 128-bit AES.

EV-EVSE vulnerabilities
EV-EVSE vulnerabilities, the researchers identified risks in a number of areas, including the injection of Log4Shell payload into a session and using a “Brokenwire” attack [3]:
https://www.brokenwire.fail/images/charger_1_cropped.mp4
The Brokenwire attack uses electromagnetic interference to interrupt the communications between the charger and the vehicle and which causes the session to stop. It requires just 1W of power to conduct the attack and can be done up to a distance of 47 meters [here].

In 2019, a side channel was used by Baker et al [4], and which could eavesdrop on the CCS changing session. Figure 5outlines the method used to unscramble the signals.

Overall the researchers were able to crack sessions in a number of charging points around the South of England (Figure 6). In the left-hand side of Figure 6, there is one vehicle being charged, and the research team were able to recover around 91.8% of all the messages sent. The success rate was only 42.5% when two vehicles were being charged. The results for two vehicles is less successful as there is interference between the two signals.


The paper outlines a wide range of data that could be harvested from the session (Figure 8), including the EV-ID (the vehicle identifier) and the EV MAC (the MAC address of the charger in the car), along with the monitoring of Internet activity related to the car.

Other attacks and defences
The paper [1] has a mine of attacks and also presents ways that could be used to defend against some of these. Figures 9 to 11 outline some of these discovered vulnerabilities from the literature.



Conclusion
Energy supplies one of the most important agenda items at the current time, and it is likely they will only increase in their importance. We must, thus, do everything that we can to make sure that these cannot be hacked by our adversaries. The paper reminds us that we have so much to do in this regard. Generally, car manufacturers have made cars, and where cybersecurity often just focused on the physical aspects of the car. Increasingly, cars are connecting to the Internet, and thus open them up to all the cybersecurity risks we face in our normal lives. So, do the manufacturers actually understand these risks?
References
[1] Johnson, J., Berg, T., Anderson, B., & Wright, B. (2022). Review of Electric Vehicle Charger Cybersecurity Vulnerabilities, Potential Impacts, and Defenses. Energies, 15(11), 3931 [here].
[2] https://www.brokenwire.fail/
[3] Köhler, S., Baker, R., Strohmeier, M., & Martinovic, I. (2022). BROKENWIRE: Wireless Disruption of CCS Electric Vehicle Charging. arXiv preprint arXiv:2202.02104 [here].
[4] Baker, R., & Martinovic, I. (2019). Losing the Car Keys: Wireless {PHY-Layer} Insecurity in {EV} Charging. In 28th USENIX Security Symposium (USENIX Security 19) (pp. 407–424) [here].