RAMus: Cryptographically Secure Memory

RAMus: Cryptographically Secure Memory
As a research team at Edinburgh Napier, we spend quite a bit of time examining memory, and in discovering encryption artefacts. This includes discovering encryption keys and passwords. For some reason, those who create secure applications often forget that memory can be examined, and often leave encrypted forms in a way they can be discovered. And so keys that should take trillions of years to crack by brute force can be discovered in a relatively short time period.
Attacks have included the cold boot attack:
And here is our research where we can discover a 128-bit AES key within 30 minutes:
https://youtu.be/7D-Hr4Nw0T4?t=1140
RAMus
So, now a new research paper aims to overcome these problems [here][1]:
You will notice it includes Vincent Rijmen as an author, and who was one of the creators of Rijndael — aka AES. Overall it is a light-weight block cipher, and which has a lower performance impact than AES. It is also tweakable, and which is often used in disk encryption. With this, each block is encrypted with the same key, which a tweak is used to modify the key that is used in corresponding blocks.
With a lightweight cipher, we often use a smaller block size than AES. With AES the block size is 128 bits, whereas RAMus has a 64-bit block size. We then use a 128-bit encryption and 17 rounds of ciphering. The same key is used for every round and is derived at the start of the ciphering process, along with all of the round keys. This means that there is only a performance hit for key generation at the start of the ciphering.
Within each round, RAMus uses an S-box to scramble byte values:
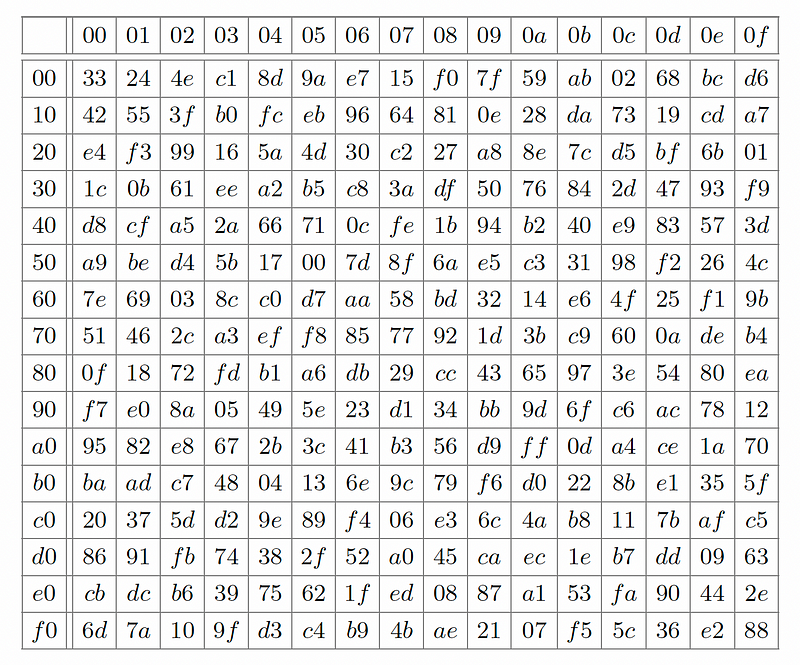
If a byte value of E1 is entered, the output of the S-box will be DC. A reverse S-box then will convert it back again to E1. Overall, we feed the key, the plaintext and the tweak into the Sbox for each round. In Figure 3, the paper shows two rounds, and where we basically perform XOR operations and Sbox conversions.
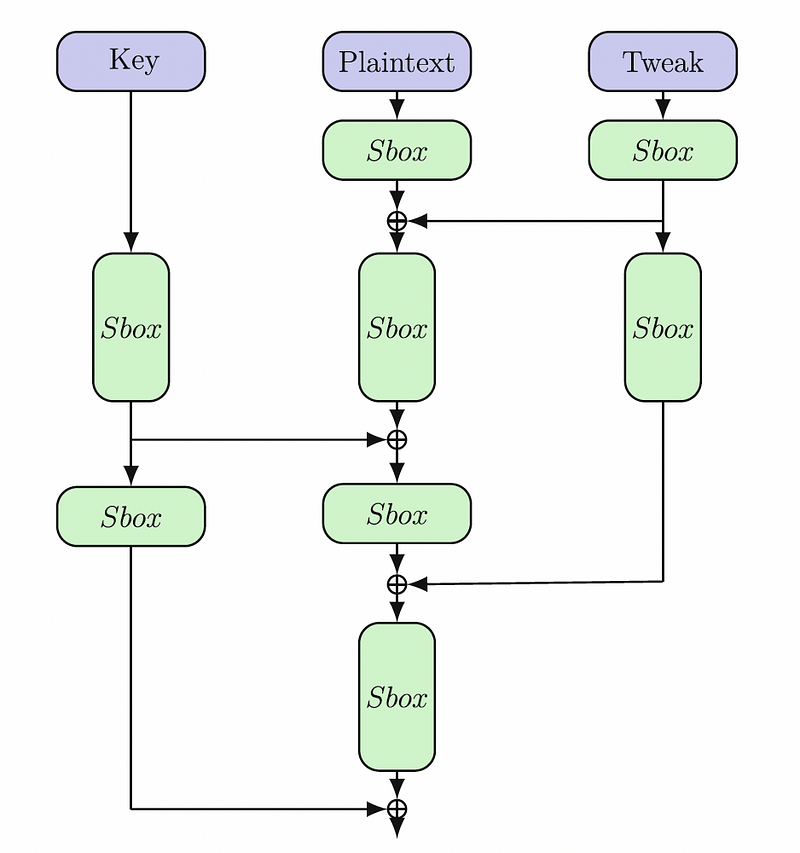
With even rounds, we apply the key, plaintext and tweak in rows, and in odd-numbered rounds, they are applied in columns.
Conclusions
After NIST defined the PQC methods that will go forward for standardization (including Kyber for key exchange and Dilithium for digital signatures), the next great standard will be lightweight cryptography. If you want to learn more, try here:
https://asecuritysite.com/light/
Reference
[1] Posteuca, R., & Rijmen, V. (2022). RAMus-A New Lightweight Block Cipher for RAM Encryption. In International Conference on Security and Cryptography for Networks (pp. 69–92). Springer, Cham [here].