Did You Know That The Teams App Is Just A Browser?

Did You Know That The Teams App Is Just A Browser?
The App uses Electron and the Web Version uses Edge!
Let’s start with a bit of theory … the Microsoft Teams App uses the Electron-based App — and is basically a customized browser. It thus has cookies, session strings, and logs. The Web version uses Microsoft Edge and which has considerably better security than the App. Confused, already? Then read on …
The three phases of video conferencing?
Now we have that out of the way, let’s see how we have evolved in our online presence over the past few years of the pandemic. Before this, we often used Cisco phones in order to create Web conferences. This was a happy world of pressing buttons on phones. The concept of us needing to use video for all our meetings and interactions seemed a crazy far future world. If we needed it, we’d use Skype for convenience. But the pandemic changed everything, as we rush to find a way that allowed us to continue our business and social world in an online way. In an instance, video calling became a defacto tool. And, without it, we would have crashed our economies and our social life.
For many, we have followed a number of phases:
- Phase 1. Using WebEx, and often disliking its performance and useability. In many corporations, video conferencing has been a fairly formal integration, and where WebEx integrated into the telephony Unfortunately WebEx just refused to change its clunky way of user interaction. The App was not well matched to user-to-user interaction and was designed more for a corporate-type setup of video conferencing.
- Phase 2. Adopting Zoom, and thinking it was generally great. Zoom got it right straight away, with great performance and an easy setup. It was, though, never going to stick for many corporate environments, and which has invested so much in their Microsoft infrastructure. It was a nightmare from a security point of view, as it just didn’t link into the back-end of corporate systems. The corporate world awaited Microsoft.
- Phase 3. Using Teams for most of your online work. This was the final phase, and where Microsoft found a solution to the problem, and dumped Skype, and found a new way of pushing SharePoint.
It has been a gradual move, but many now use Teams as the default way of communicating over video. Microsoft caught the wave and skinned its Sharepoint infrastructure into a user interface which included video conferencing. Overall, it’s fine. It is a jack of all trades and a master of none. It doesn’t have the interaction possibilities of Slack, but it’s acceptable.
But, what actually is Teams? Well, the desktop app is actually a skinned Web browser that uses the Electron framework. You will find the Electron framework in many applications, including Microsoft Visual Studio Code, WhatsApp and Slack. It is thus built from JavaScript, HTML and CSS. This is probably one reason that you really can’t change that much about our environment, and even simple things like listing your Team in alphabet order are not supported.
But it’s a browser!
As Electron is just a browser, it stores its files in the way that a browser does, such as having cookies and sessions. Unfortunately, Electron does not encrypt its data, so these files often store sensitive information, such as access tokens, in plain text within binary files. A team at Electrovolt has found that it is possible to implement remote code execution (RCE) on Electron apps, and which allows code to be run remotely on a machine:
But, it’s a browser (again)!
Another less serious vulnerability has also been discovered by the Vectra Protect team, and which allows an intruder the possibility to steal access credentials. This is because Teams stores authentication tokens in plaintext, including for MFA (Multifactor Authentication)-enabled accounts. Unfortunately, Electron doesn’t support encryption or file system protection as standard.
In the ldb file, the researchers discovered that the access tokens were available in plaintext. These included Outlook and Skype access tokens. On Windows, the file is stored in %AppData%\Microsoft\Teams\Local Storage\leveldb and on macOS: ~/Library/Application Support/Microsoft/Teams/Cookies. For macOS, we get something like:
leveldb % ls
000005.ldb 036400.ldb 036404.ldb LOG
036379.ldb 036402.ldb CURRENT LOG.old
036398.ldb 036403.log LOCK MANIFEST-022716
A sample listing shows a Teams channel and a posting:
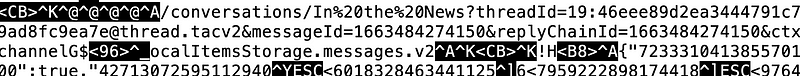
Within the Cookies file, Windows stores in %AppData%\Microsoft\Teams\Cookies and on macOS it is ~/Library/Application Support/Microsoft/Teams/Cookies. This file has a SQLite format and where we see cookie data:

The research team found access tokens — such as for OAuth — contained in this file, such as:

Conclusions
The Vectra team recommend:
- Not to use the App until Microsoft has patched the system. Overall, the Web-based version uses Microsoft Edge, which does support encryption and file access controls.
- Securely store OAuth tokens in an encrypted manner.
To me, to use Electron in a corporate environment seems rather sloppy, and Microsoft obviously just rushed the product to market, in order to fill a gaps. It’s currently a long way off being a tool that takes security seriously. It also is still poor in many respects — in that you can’t order names in alphabet order. Also, the way it integrates with SharePoint is terrible, and shows a real lack of consistency. To me, SharePoint has always been a poor tool for sharing, and it has never really advanced much from being a technical tool.